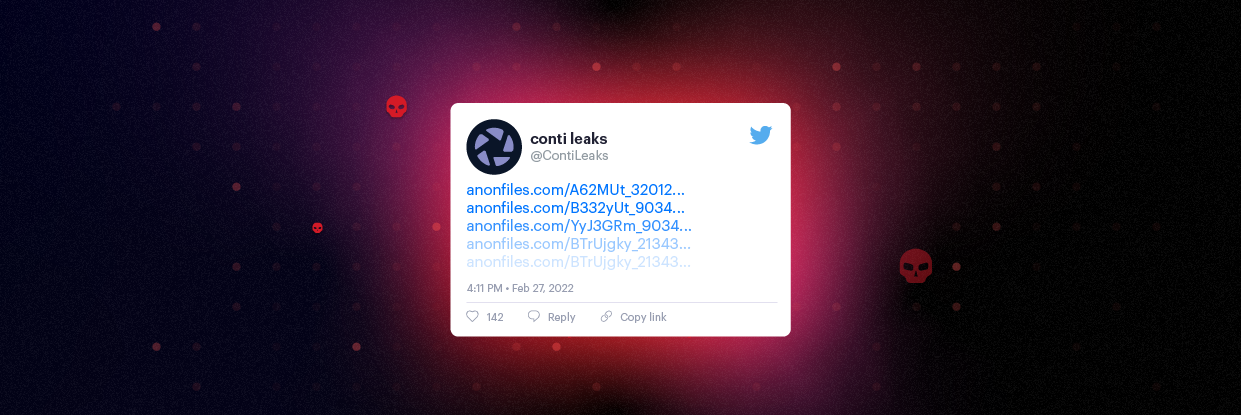
Conti, one of the most infamous, prolific and successful big game ransomware threats, has suffered yet another embarrassing leak with a treasure trove of both internal chat transcripts and source code being shared by a reported Ukrainian member (Figure 1).

Figure 1 – Initial leak message (Source)
Having previously had their internal manuals and tools exposed by a disgruntled affiliate in August 2021, these latest leaks appear to be in response to the group “officially announcing a full support of Russian government” [sic] and that they would respond to any attack, cyber or otherwise, against Russia with “all possible resources to strike back at the critical infrastructures of an enemy”.
Given that members of the group may themselves be Ukrainian or have close ties to the country, this warning likely inflamed tempers leading to both the warning being updated (Figure 2) and these subsequent leaks.

Figure 2 – Updated Conti warning of retaliation
Much as the previous leak allowed their toolsets to be analyzed and revealed common indicators of compromise (IOC), analysis of these recent data leaks and chat logs provides insights into how Conti, and likely other similar ransomware groups, coordinate and conduct their operations.
The outcome of these leaks remains to be seen; Conti and its members may be forced to disband or, as is often the case with ransomware groups, lay low for a period before rebranding and relaunching their operation.
Group Management
Salary discussions like the one below (Figure 3) indicate the size and scale of Conti’s ransomware operation, its internal structure, and number of members.

Figure 3 – Salary discussion
The salary breakdown identifies five distinct teams:- ‘Main’, 62 people
- ‘Reverse’, 23 people
- ‘New coder’, 6 people
- ‘Reverses’, 6 people (appears separate to the other ‘reverse’ team)
- ‘OSINT’, 4 people
As most ransomware groups operate with some form of profit-sharing, these salary figures may be related to ransom payments at the time. At the current rate, the stated 164.8K (assumed US dollars) would equate to almost $2M a year.
Regardless, the number of team members and salary figures clearly demonstrate that the group, a cybercriminal enterprise, have invested a considerable amount of effort to identify and compromise new organizations, steal data and extort victims.
Jorge Gomes made an interactive data visualization that maps the Conti member network based on their interactions:
Group Infrastructure
In addition to paying team members, Conti will likely incur significant ongoing costs to maintain their backend infrastructure.
In addition to renting virtual private servers (VPS), favoring services that accept Bitcoin, the group most likely maintains VPN subscriptions to maintain a layer of anonymity when conducting their operations, as well as subscriptions to or purchases of various security products.
Adversarial use of security products allows a ransomware group to develop, test and practice exploits against security solutions used by their victims in a controlled environment. In Conti’s case, these would likely include various antivirus packages, VMware’s Carbon Black EDR solution and SonicWall Secure Mobile Access (SMA) 410.
Whilst not attributed specifically to Conti, threat actors were actively exploiting SonicWall SMA devices in January 2022 in an attempt to take advantage of CVE-2021-20038, a critical unauthenticated stack-based buffer overflow that would allow full control of the device potentially allowing credentials to be intercepted.
In yet another example of Conti’s liquidity, the group had trouble purchasing VMware Carbon Black directly and therefore appeared to encourage a third-party business to purchase the required solution in return for a $30K payment (Figure 4).

Figure 4 – VMware Carbon Black purchase (EUR14.8K + 20% BTC fees and ‘30’ for the intermediary)
Open-Source Intelligence Gathering
Attackers typically conduct reconnaissance to understand their target and improve their chances prior to engaging. Conti has a dedicated open-source intelligence (OSINT) team that would presumably be tasked with gathering information on victim organizations from both the target’s own website as well as popular online data sources.
Likely used to gather names and contact information for potential high-value individuals, contact database services such as SignalHire and Zoominfo are explicitly mentioned within the chat transcripts.
These database services, typically used by sales and marketing teams, would likely prove useful for a threat actor when determining targets for spear-phishing campaigns, and contacts to ‘name drop’ in social engineering attacks.
The group also mentions the use of Shodan, a search engine for internet-connected devices, as well as a premium Spiderfoot subscription. Both would allow the OSINT team to discover the digital assets of a target and determine weak points for exploitation such as open ports or vulnerable service banners and technologies.
Conversely, the OSINT team could also use these services to hunt for targets that were vulnerable to specific exploits and provide these to their exploit teams.
It appears that the group also OSINT tactics to gather financial details during ransom negotiations. Details of an organization’s earnings can often be gathered from open sources, of course, especially if the victim is publicly traded. Both may be used to determine how much a victim might be able or willing to pay.
Initial Access
Ransomware groups make use of stolen credentials to gain access to exposed services, be they remote desktop protocol (RDP) sessions or web mailboxes, as well as exploiting vulnerabilities in network infrastructure devices such as VPN gateways. Conti has entered into conversations with third-party ‘initial access brokers’ that offer access to compromised hosts via an implant or directly via RDP.
In these instances, the broker would be paid a ‘cut’ of any ransom proceeds. Based on one conversation, this would usually be 25%, potentially rising to 30% for close relationships. The use of a broker would diminish the group’s profits, so it’s unsurprising to see multiple discussions where group members share new vulnerability and exploit articles, and monitor vulnerability alert sites.
Discussions regarding CVE-2020-5135, a critical SonicWall VPN stack-based buffer overflow, expressed interest in creating a scanning tool to find vulnerable devices. Given that some 800,000 vulnerable devices were reported in October 2020 when CVE-2020-5135 was first announced, it is possible that some organizations have yet to patch.
Notably, the group also held discussions about the purchase of a 0-day exploit that targets a use-after-free vulnerability in the Windows User-mode Driver Framework Reflector, `WUDFRD.sys`, although how this might be deployed and its viability have not been determined.
TrickBot: Cookie Grabber
Analysis of the August 2021 leak identified that Conti used stealer malware during their attacks, no doubt to gather credentials, and potentially as part of internal reconnaissance after gaining initial access.
Corroborating this, the leaked chat transcripts include troubleshooting discussions between Conti members with examples of command and control (C2) server URLs, HTTP requests (Figure 5) and server responses.

Figure 5 – Stealer HTTP POST
Based on these shared HTTP POST requests and C2 backend logs, the stealer in use by Conti appears to be consistent with TrickBot’s ‘Cookie Grabber’ module that is used to acquire the following data from victim machines:
- Username
- Browser
- Cookie domain
- Cookie name
- Cookie value
- Cookie creation timestamp
- Cookie expiration timestamp
- Cookie path
Whilst Cookie Grabber can be downloaded for use within TrickBot, it reportedly will also operate as a standalone module, so it is possible that Conti are using specific malware elements to support their activity.
Trickbot C2 activity is further suggested by the use of ‘Cowboy’, an open source small and fast HTTP server written in Erlang, as well as a common URL structure:
- /<GTAG>/<CLIENTID>/
The GTAG is used as a campaign identifier and in Conti’s case ‘lib30’, ‘tot57’ and ‘TST150’ were shared by group members. The first two values have been associated with generic malicious spam (malspam) campaigns; ‘TST150’ may be reserved for internal testing purposes.
As expected, the client ID value is used to identify victims and uses another common structure:
- <COMPUTER_NAME>_W<WINDOWS_VERSION><WINDOWS_BUILD>.<32_CHAR_HEX>
Data Exfiltration
Consistent with most big game hunter ransomware threats, having infiltrated a victim network the threat actor will locate and exfiltrate confidential and sensitive data for later use in the extortion process.
Based on content within the August 2021 leak, it is known that Conti have used the legitimate opensource file synchronization tool ‘Rclone’, likely alongside other off-the-shelf data transfer tools, to exfiltrate stolen data.
As observed in 2021, the group continues to exfiltrate data to the Mega.nz cloud file storage service, likely taking advantage of free accounts with 20GB of storage, although the leaked chat transcripts indicate the group also utilized dedicated virtual private server (VPS) instances.
Given that some organizations may choose to limit access to cloud storage services, the use of VPS instances, typically accessed by IP address and potentially via FTP, may allow the group to avoid scrutiny and exfiltrate vast amounts of data whilst remaining undetected.
Although now taken offline, browsing the directory structure of one of these exfiltration VPS instances provided an indication (Figure 6) of the type of data targeted by the group.

Figure 6 – Conti dedicated VPS host used for data exfiltration
The stolen data consisted of common productivity files, such as documents and spreadsheets, as well as database, image and computer-aided design (CAD) files. Additionally, large 7zip archives, likely created and staged within the victim network prior to transfer, were present along with mail server data in the form of a Microsoft Exchange EDB file.
The stolen data provides leverage during the extortion phase (“pay or we leak”), and the group reviews stolen financial records to determine a victim’s ability to pay.
Evidence of Conti’s approach, which resembles that of other ransomware groups, can be seen in excerpts of a negotiation between Conti and a victim (Figure 7).

Figure 7 – Negotiation using knowledge of the victim’s finances (Chat reconstruction)
If you wait for a breach to occur, it's too late. Strengthen your cloud security today and stay ahead of emerging threats with Varonis. Learn more about our comprehensive cloud security solutions and take advantage of our free Data Risk Assessment to help you safeguard your digital assets.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.