Varonis now integrates with AWS Security Hub to help security teams cut through alert noise, accelerate remediation, and protect sensitive data in AWS environments and across their data estate
Security teams often struggle to distinguish between critical threats and alert noise. To help teams focus on what matters most, the new AWS Security Hub correlates, enriches, and prioritizes security signals from AWS security services, such as threat detection and vulnerability findings.
With the integration between Varonis and AWS Security Hub, Varonis ingests the prioritized findings, adds context on data sensitivity, identity, and user behavior, and delivers a single view of risk. Combined with automated remediation and data-centric threat detection, Varonis helps stop breaches and protect sensitive data.
In this blog, we’ll show how the Varonis–AWS Security Hub integration enhances data security in AWS, across SaaS applications, and in multi-cloud and hybrid environments.
Cutting through the noise
With constant data growth, thousands of users to manage, and new AI-driven risks, security teams can struggle to keep up.
To streamline security, AWS Security Hub simplifies this by correlating and prioritizing signals from services, like Amazon GuardDuty, Amazon Inspector, Amazon Macie, and AWS Security Hub CSPM.
Varonis leverages these findings, adds context about data sensitivity, identity, and user behavior, and delivers a unified view of risk across data sources and applications. With automated remediations for critical issues, including misconfigurations, identity exposure, and public data access, Varonis further helps to cut through the noise and remove the burden of manual fixes.
Ryan Orsi, WW Leader for Security, Cloud Operations, Resilience Partner Specialists at AWS
Enriched AWS Security Hub findings
Varonis enriched AWS Security Hub findings with context on data sensitivity, identity, and user behavior.
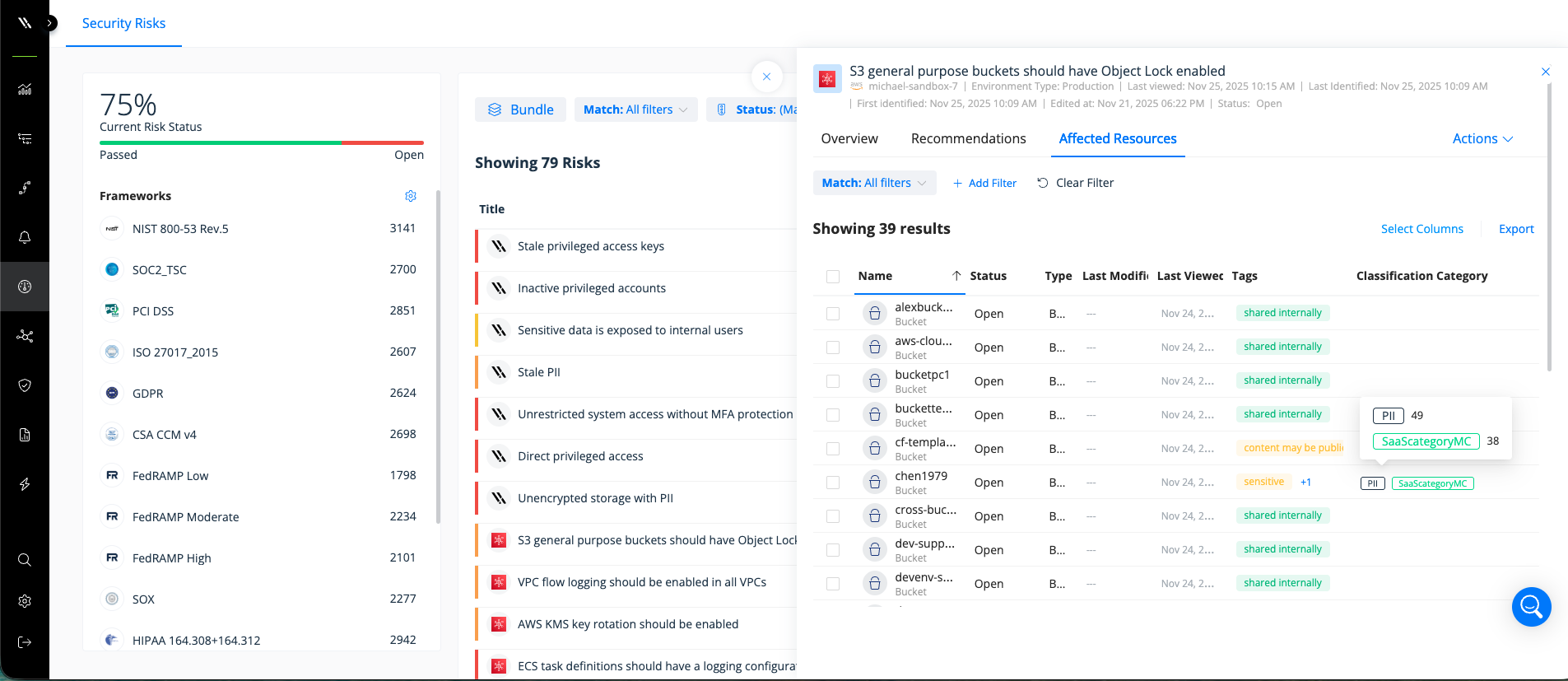
Varonis enriched AWS Security Hub findings with context on data sensitivity, identity, and user behavior.
Varonis enriches AWS Security Hub findings with context on data sensitivity, identity, and user behavior. By combining AWS Security Hub’s prioritized signals with Varonis’ industry-leading data classification, permissions mapping, identity risk analysis, and alignment with frameworks like NIST, HIPAA, and ISO, security teams can quickly identify and remediate risks tied to sensitive data and compliance gaps.
Unified visibility across AWS and your entire data estate
Varonis ingests misconfigurations and risks from AWS Security Hub and shows them in conjunction with risks and exposure from your entire data estate.
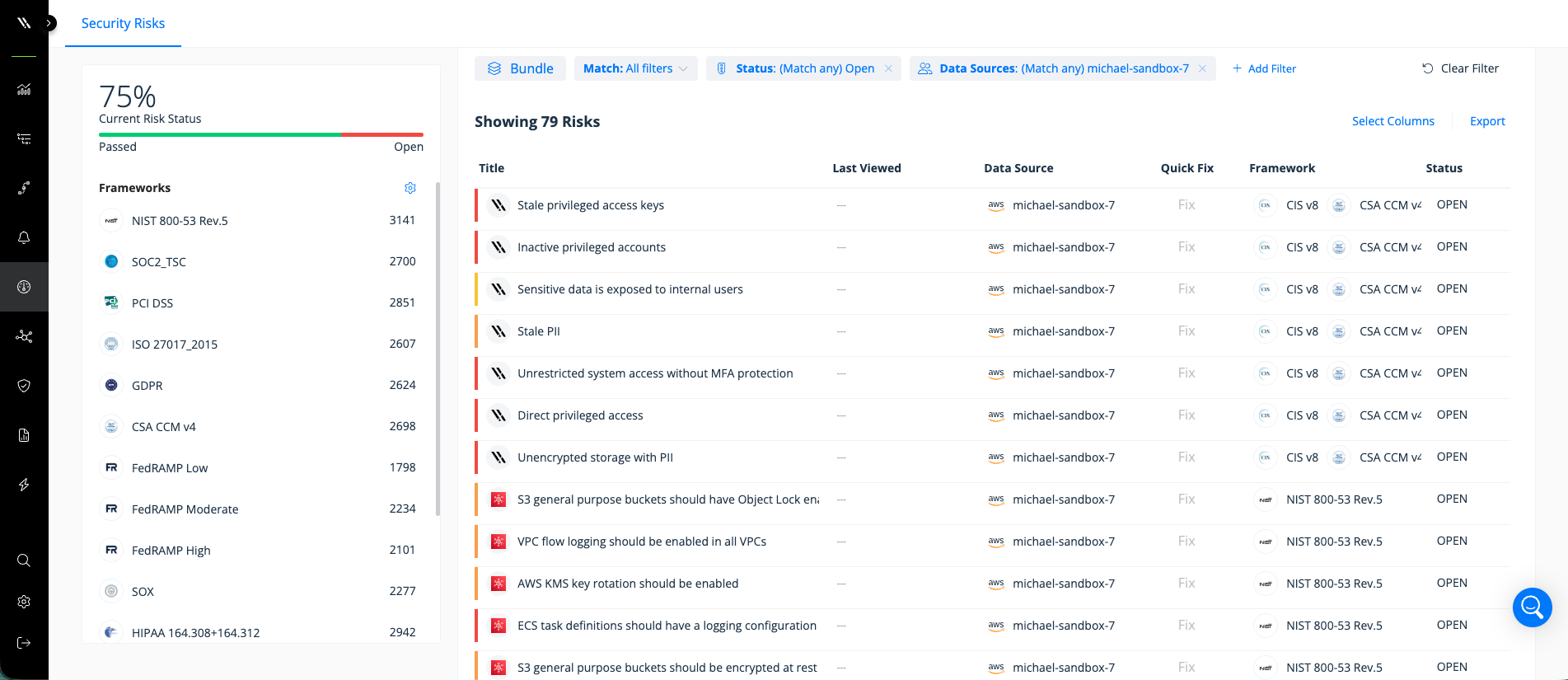
Varonis ingests misconfigurations and risks from AWS Security Hub and shows them in conjunction with risks and exposure from your entire data estate.
Varonis ingests the prioritized misconfigurations and risks from AWS Security Hub and shows them in conjunction with risks and exposure from your entire data estate, including Salesforce, Snowflake, and ServiceNow.
Once they have access to your environment, attackers often move laterally, escalate privileges, and target sensitive data for exfiltration or encryption. Detecting this kind of malicious behavior requires a unified view with context into data sensitivity, identity, and user behavior.
Accelerated remediation
Varonis surfaces remediation guidance directly from AWS Security Hub.

Varonis surfaces remediation guidance directly from AWS Security Hub.
AWS Security Hub delivers integrated risk analysis on potential attack paths, surfaces exploitable vulnerabilities and misconfigurations, and provides actionable remediation guidance. Varonis combines that guidance with automated remediation to help customers quickly and effortlessly fix misconfiguration and secure exposed data.
Varonis continues to develop automated remediations to help scale security in AWS, including blocking public access to S3 buckets, removing stale users, roles, and access keys, and remediating critical misconfigurations like missing password policies and encryption.
End-to-end data security
Varonis delivers end-to-end data security with data discovery and classification, posture and identity protection, and data-centric threat detection and user behavioral analytics. Our integration with AWS Security Hub enhances this approach, providing you with deeper visibility and automated remediation for AWS.
We’re on a mission to simplify security and deliver automated outcomes. The Unified Data Security Platform installs in minutes and protects sensitive data wherever it lives — cloud, SaaS, or on-prem.
Ready to simplify and strengthen your cloud security strategy? Request a demo today and find Varonis on the AWS Marketplace.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.



.png)



