Ransomware threat actors have long been known for stealing data, encrypting data, and then demanding ransom payments from unfortunate victims.
Most of these groups previously focused on on-premises infrastructure or virtual servers hosted in the cloud. Targeting the cloud control plane was seen as an attack surface more likely to be targeted by advanced threat groups, such as nation states or groups like Scattered Spider.
However, Varonis has investigated several cases where ransomware groups actively target opportunities to move into the cloud control plane. This leads to increased complexity for incident responders and shows that the technical barriers required to attack cloud infrastructure successfully are decreasing.
This blog takes a deep dive into the anatomy of an AWS-based attack our team triaged, what it looks like, how to stop it, and how Varonis can help.
What are AWS keys?
An AWS key is a programmatic key that can be attached to a user and allows interaction with AWS based on the attached user’s assigned permissions. It consists of an Access Key ID, which would look something like AKIAIOSFODMM7EXAMPLE, and a corresponding secret access key, which would look something like wJalrXUtnFFMI/K7NDENG/bPxRfiCYEXAMPLEKEY.
The Access Key ID is like a username and is not secret; the secret access key, as its name suggests, is hidden and is like a password. Together, they can be used to access AWS, and if they are compromised, the holder could gain a foothold in the AWS environment. It is important to note that they are independent of an AWS user’s password, and just because an attacker has access to a key set does not mean they necessarily compromised the user’s actual account.
This fact is crucial when tracking where the keys were compromised in the environment.
Why does this matter?
Targeting your cloud management layer exposes a whole new attack surface, where monitoring and detection may not be as mature. In addition, any post-breach ransomware investigation needs to be able to include the cloud environment.
What is the control plane?
When referencing cloud infrastructure, the control plane refers to the provision of APIs to create, read/describe, update, delete, and list resources. The plane manages virtual resources, and how your cloud admins will conduct their work managing your cloud environment.
So, creating an EC2 in AWS or a virtual machine in Azure is done in the control plane. Logging into a created virtual machine and using it is the data plane.
Often, the distinction between on-premises and virtual resources, as part of the data plane, is not apparent to a threat actor, as they frequently present as one network. So, they actively target resources in the cloud as part of the data plane; this is not new.
Ransomware actors targeting the control plane are rarer and arguably more dangerous, as they have much more control and ability to impact the environment.
Traditional security tooling, such as Endpoint Detection and Response software (EDR), which you install on endpoints and servers, likely cannot detect attackers interacting with the control plane.
It is necessary to ensure that telemetry from your cloud environments’ control plane is collected and monitored to identify these types of attacks.
Detecting control plane attacks
Varonis was alerted to a control plane attack in a client’s AWS environment when an alert was triggered on our Data Security Platform.
The alert showed an attempt to utilize the Pacu AWS exploitation framework to target the client’s AWS environment.
Figure 1 : Alert showing an attempt to use the Pacu exploitation framework
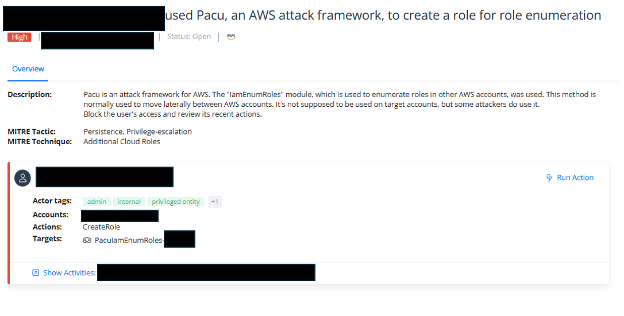
Figure 1 : Alert showing an attempt to use the Pacu exploitation framework
What is Pacu?
Pacu is a legitimate set of tools designed to test and exploit an AWS environment as part of a penetration test. However, like all legitimate tooling, it can be used for good and evil.
This framework contains numerous modules that allow an attacker to pass the module AWS access keys to interact with a target AWS environment.
Pacu provides a broad range of capabilities, which fall into the following categories:
Exfiltrate data- Can download EBS snapshots to the user’s computer, which can then be mounted and explored for sensitive data
- Allows for the exploration of RDS databases by snapshotting existing ones and then using the snapshot to create a new database for the user to browse and interact with
- Offers a module to scan the AWS account for all S3 buckets the account has access to, and offers to download all the data
Exploit
- Allows remote code execution (RCE) and backdoor installation on EC2 instances
- Can create keys to access Lightsail instances
- Provides the ability to explore EBS snapshots within the targeted environment
- Allows the creation of an API gateway for every available region within the account
- Identifies misconfigurations that allow privilege escalation
- Offers numerous and varied capabilities to enumerate many different services within the targeted account
- Can establish multiple backdoors relating to the abuse of IAM
- Adds backdoor rules to EC2 security groups
- Allows the creation of backdoors by abusing the Lambda service
- Can download CloudTrail and CloudWatch logs
- Can take enumerated logging data and present options for disabling or minimizing each source
- Can add IP addresses to the GuardDuty allow list
- Can attempt CSV injection into CloudTrail logs
- Offers capabilities targeting VPC and SNS

Pacu's capabilities are impressive and concerning for those hoping to defend their environment, and detecting its use early on is crucial in this process.
Investigating the alert and searching for the keys
Once the alert was triggered, our forensics experts began an emergency response investigation. After reviewing the alert, we identified the specific programmatic keys used to make the API call that triggered it.
Having identified the keys, we could utilize Varonis to search for specific API actions that had been taken using the compromised keys. Varonis also allowed us to quickly identify the IP address used to make the API calls, providing us with vital indicators of compromise (IOCs) to search for and identify other malicious actions.
In searching for the AWS keys and the IP address, the forensics team quickly identified malicious actions in additional AWS accounts controlled by the customer, bringing them into the investigation scope.
This also identified an additional set of AWS keys being used with the associated malicious IP address. These keys, in turn, belonged to an additional AWS user account. With this extra information, we could work with the victim to identify a common location where both sets of keys were located, a Veeam Backup Server.
Tying it together
Having identified the Veeam server as a common touch point for the compromised keys, the investigation confirmed that the ongoing on-premise ransomware attack had targeted the server.
This informed the overall investigation and allowed for swift remediation, with the affected AWS keys being disabled and an audit of threat actor activity within the AWS environment.
In this case, the threat actor could not properly leverage their access due to the remediation stemming from the swift alerting. Still, it highlights that cloud environments are now a legitimate target for ransomware threat actors, and they are willing to use the available tools.
This case could have been much more impactful had the threat actor remained in the environment longer. They could have exfiltrated large amounts of encrypted data or generated enormous AWS costs for the victim.
Therefore, organizations must have visibility into their cloud environments and consider threat actors' paths to move from a non-cloud environment into the cloud control plane.
Security recommendations
The following recommendations are designed to help you identify, prevent, and mitigate the issues described in this blog.
Identify
- Ensure you have adequate logging enabled for the cloud services in use
- Ensure that logging is ingested, enriched, and routinely monitored for anomalies
Prevent
- Do not use programmatic keys wherever possible. Utilize other more secure authentication methods
- Enforce MFA requirements
- Lock down API access based on IP address for highly privileged users
- Use frameworks like Pacu to assess your cloud environment as part of defense
- If threat actors use it, ensure it won’t find anything useful!
Mitigate
- Ensure permissions associated with keys are the minimum required
Don't wait for a breach to occur.
Threat actors are becoming increasingly adept at exploiting cloud environments — leveraging compromised AWS keys, targeting backup servers, and using advanced attack frameworks to evade detection.
Take proactive steps to secure your environment now. Get your Free Data Risk Assessment today and gain crucial insight into potential vulnerabilities before attackers can exploit them. Protect your cloud assets and ensure peace of mind.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.









