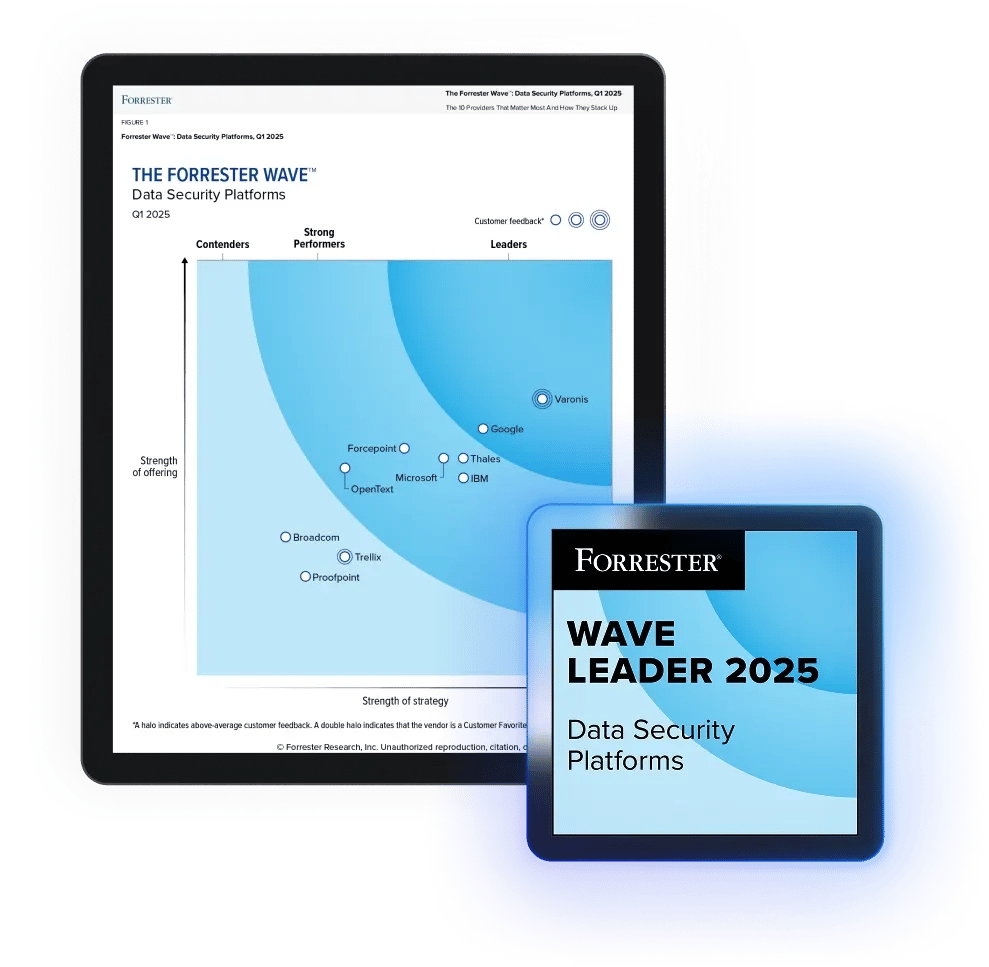
Varonis vs. Cyera
Cyera helps teams understand where sensitive data lives but visibility alone does not reduce risk.
Varonis goes further by correlating data sensitivity, permissions, identity, and activity - then automatically reducing exposure across your environment.
Trusted by 8,000+ customers



Trusted by 8,000+ customers



Data discovery is not data security.
Cyera is a data discovery tool that does static posture analysis. Varonis is an end-to-end data security platform that locks down your sensitive data and stops data breaches 24x7.



Feature Comparison
Cyera is a discovery tool. Varonis is a security solution.
Cyera is built to find problems, not fix them. Cyera struggles to scan large data stores, can't remediate issues without third-party integrations, and can't detect attacks on data.
| CAPABILITY | VARONIS | CYERA |
| Platform Focus | End-to-end data security with emphasis on automated outcomes: find, fix, alert | DSPM with emphasis on discovery, classification, and posture |
| Coverage | Broad and deep coverage across cloud, SaaS, email, and on-premises data; supports structured, semi-structured, and unstructured data | Cloud-first with immature SaaS support; on-premises coverage often fails due to proxy-based approach |
| FedRAMP | FedRAMP High Authorized | ❌ Not FedRAMP authorized |
| Classification Method | Continuous, real-time classification using incremental scanning; LLM-based classification for novel data and precision classifiers for known patters | Periodic scans with sampling by default (full scans by request); LLM-based classification |
| Threat Detection | Behavior-based threat detection for insider threats, compromised identities, ransomware, and data exfiltration | ❌ No threat detection; cannot identify active attacks or suspicious behavior |
| Identity & Permissions Analysis | Continuous identity-to-data mapping, effective permissions, blast radius, and attack path analysis | ❌ No identity-to-data mapping or permissions modeling |
| Audit Trail & Forensics | Comprehensive forensic timeline with unlimited retention (who accessed what, when, how, and from where) | Limited event auditing with 7-day retention |
| Automated Remediation | Native, automated remediation at unlimited scale (lock down data, revoke excessive access, quarantine files) | Requires third-party SOAR and manual remediation; Purview labeling capped at 100k/year with additional fees |
| Managed Detection & Response | 24x7x365 Managed Data Detection and Response (MDDR) with dedicated SOC and SLAs | ❌ No MDR service and no security alerts to monitor |
Why Companies Choose Varonis over Cyera
Varonis continuously removes stale permissions, locks down overexposed data, and enforces lead privilege - without requiring manual intervention.
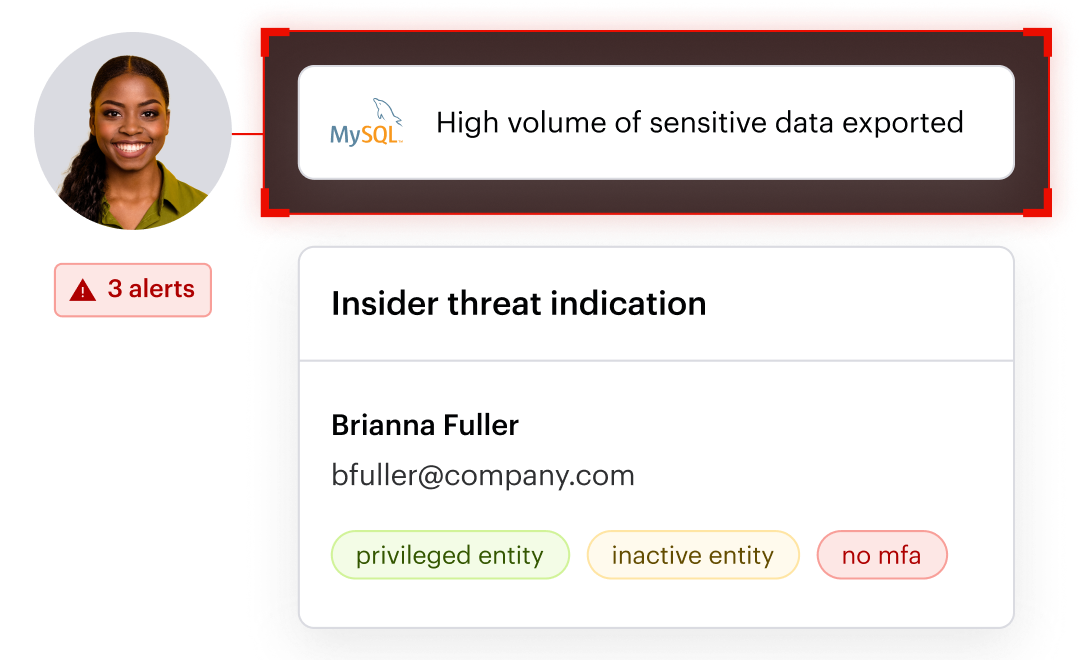
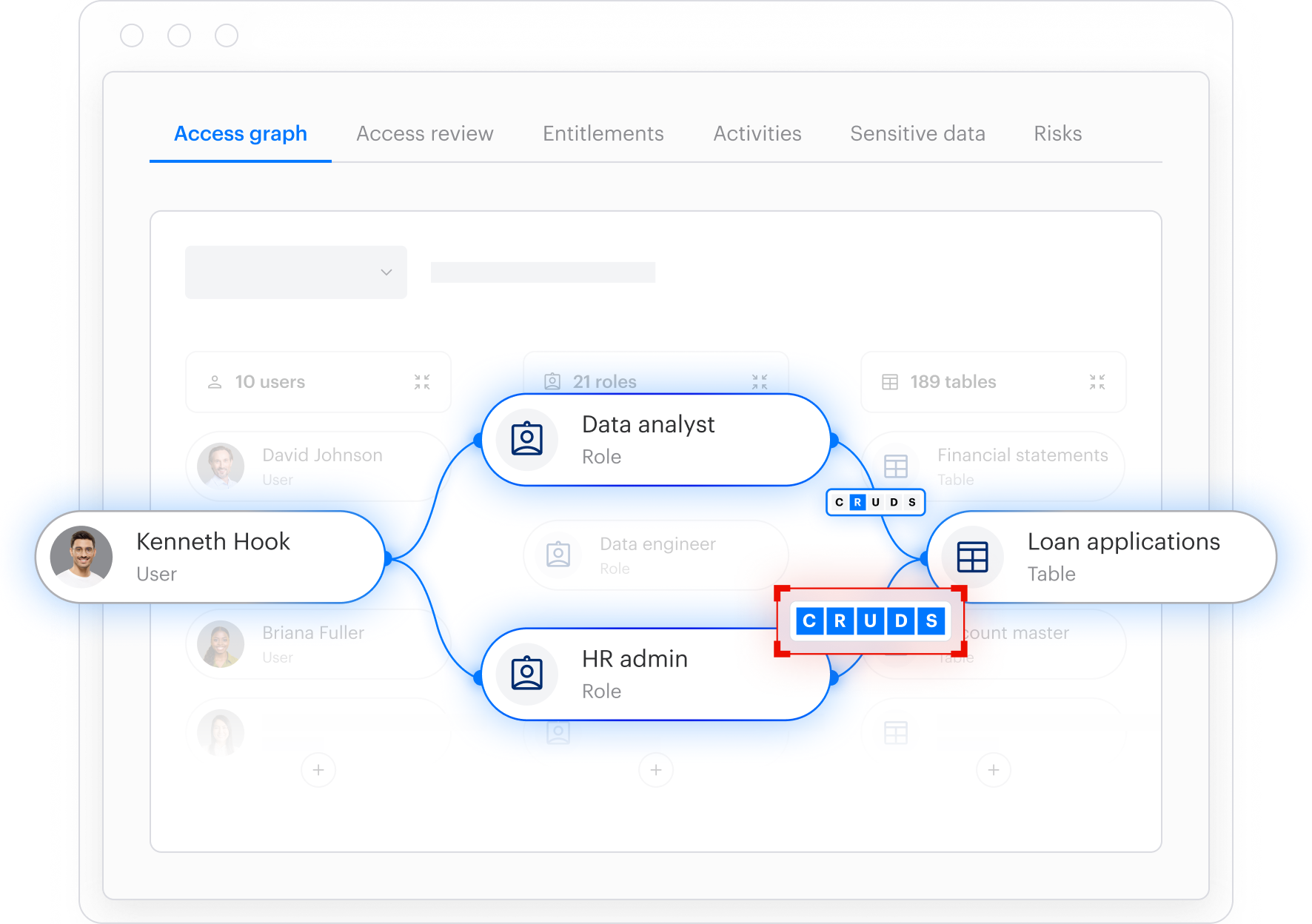
Varonis natively correlates users, service accounts, roles, and groups with the data they can access, providing context tools like Cyera lack.
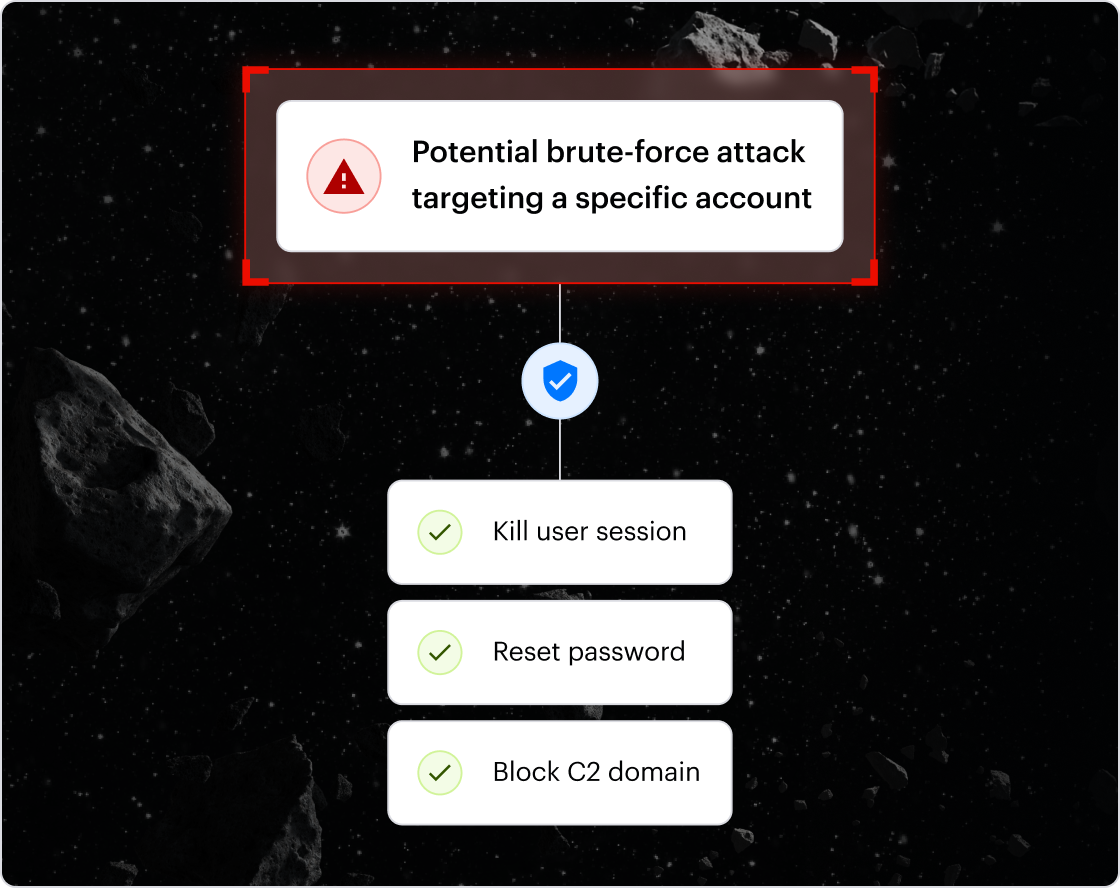
Varonis monitors how data is actually accessed and used, enabling detection of insider threats, compromised accounts, and misuse - not just misconfiguration.
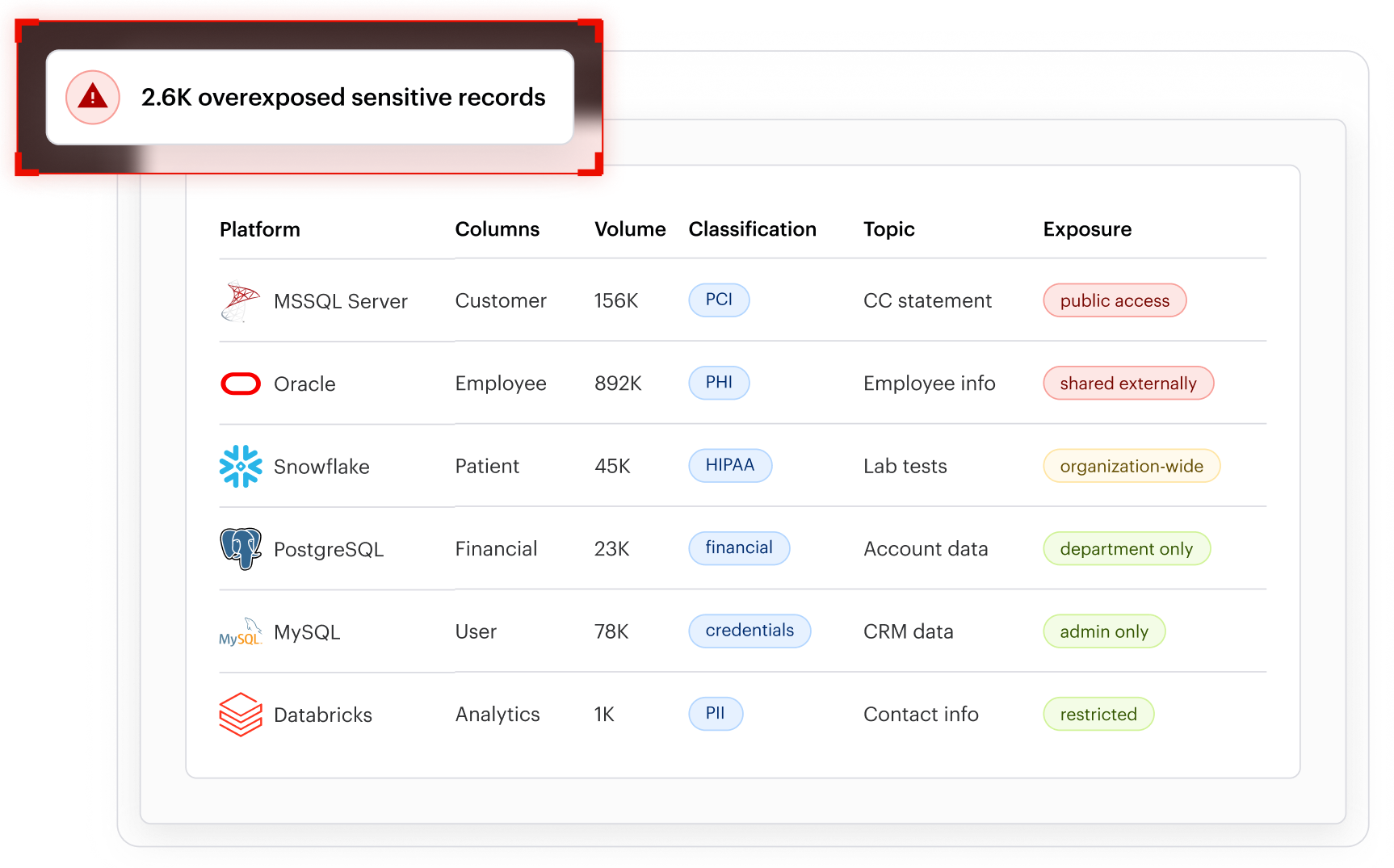
Varonis secures data across all major domains - including IaaS and SaaS data stores, identity providers, email, and network activity - giving security teams unified visibility and control across their entire data estate without adding more tools.
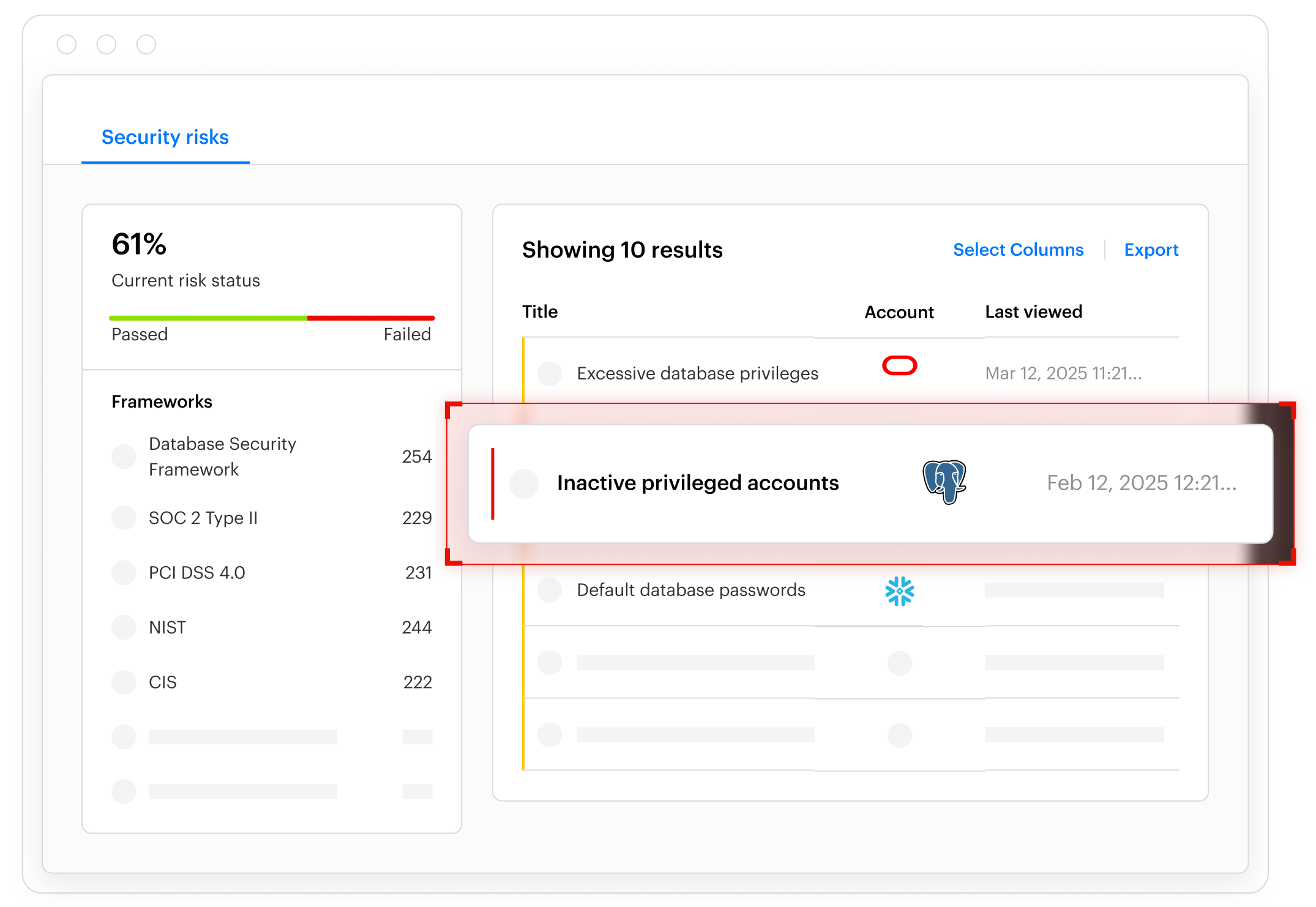
Varonis identifies real attack paths and suspicious behavior in progress, rather than relying on static risk scoring alone.
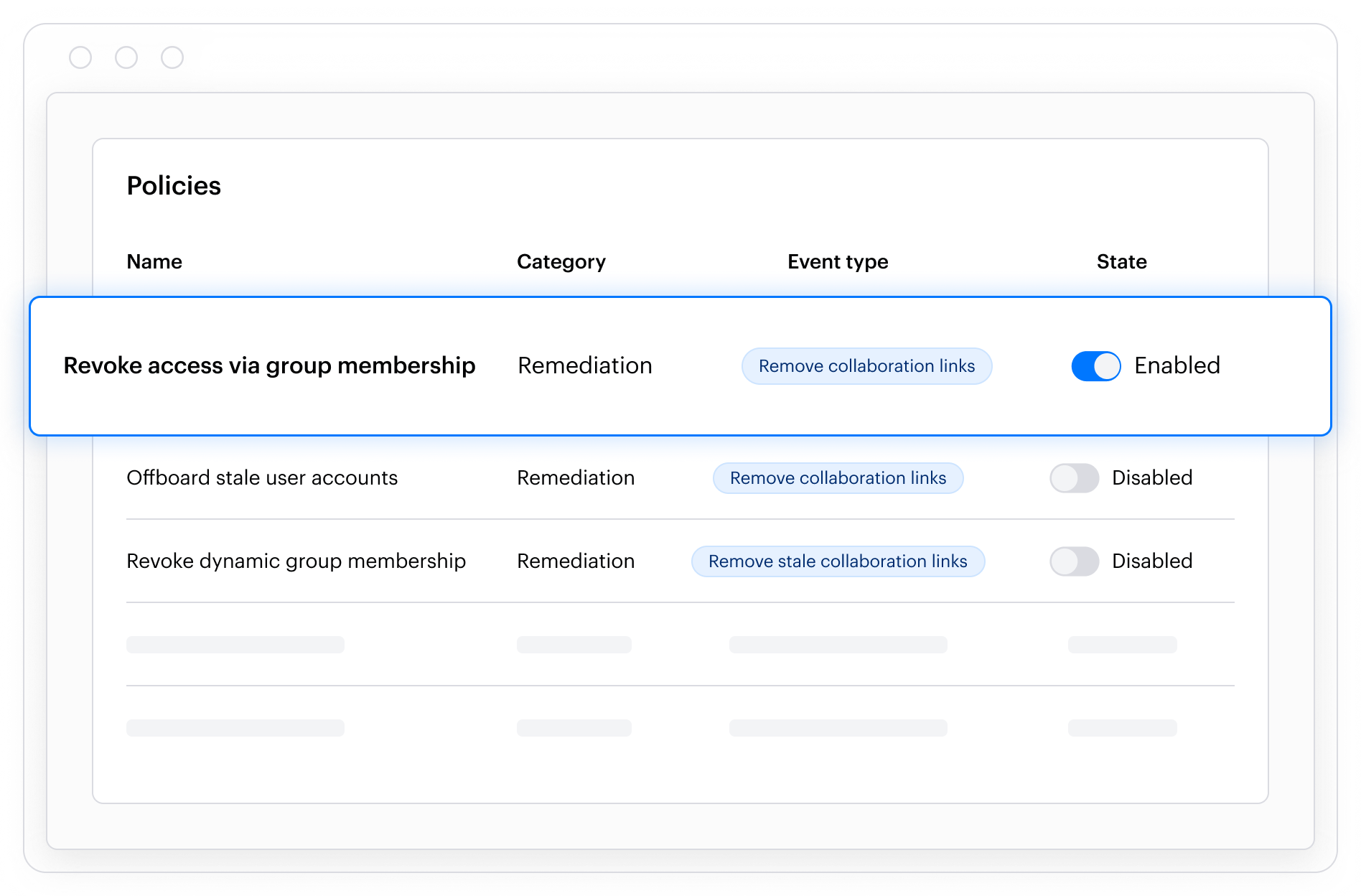
Customers choose Varonis to lower blast radius, reduce standing access, and minimize exposure, not just to inventory sensitive data.
Varonis continuously removes stale permissions, locks down overexposed data, and enforces lead privilege - without requiring manual intervention.
Varonis natively correlates users, service accounts, roles, and groups with the data they can access, providing context tools like Cyera lack.
Varonis monitors how data is actually accessed and used, enabling detection of insider threats, compromised accounts, and misuse - not just misconfiguration.
Varonis secures data across all major domains - including IaaS and SaaS data stores, identity providers, email, and network activity - giving security teams unified visibility and control across their entire data estate without adding more tools.
Varonis identifies real attack paths and suspicious behavior in progress, rather than relying on static risk scoring alone.
Customers choose Varonis to lower blast radius, reduce standing access, and minimize exposure, not just to inventory sensitive data.






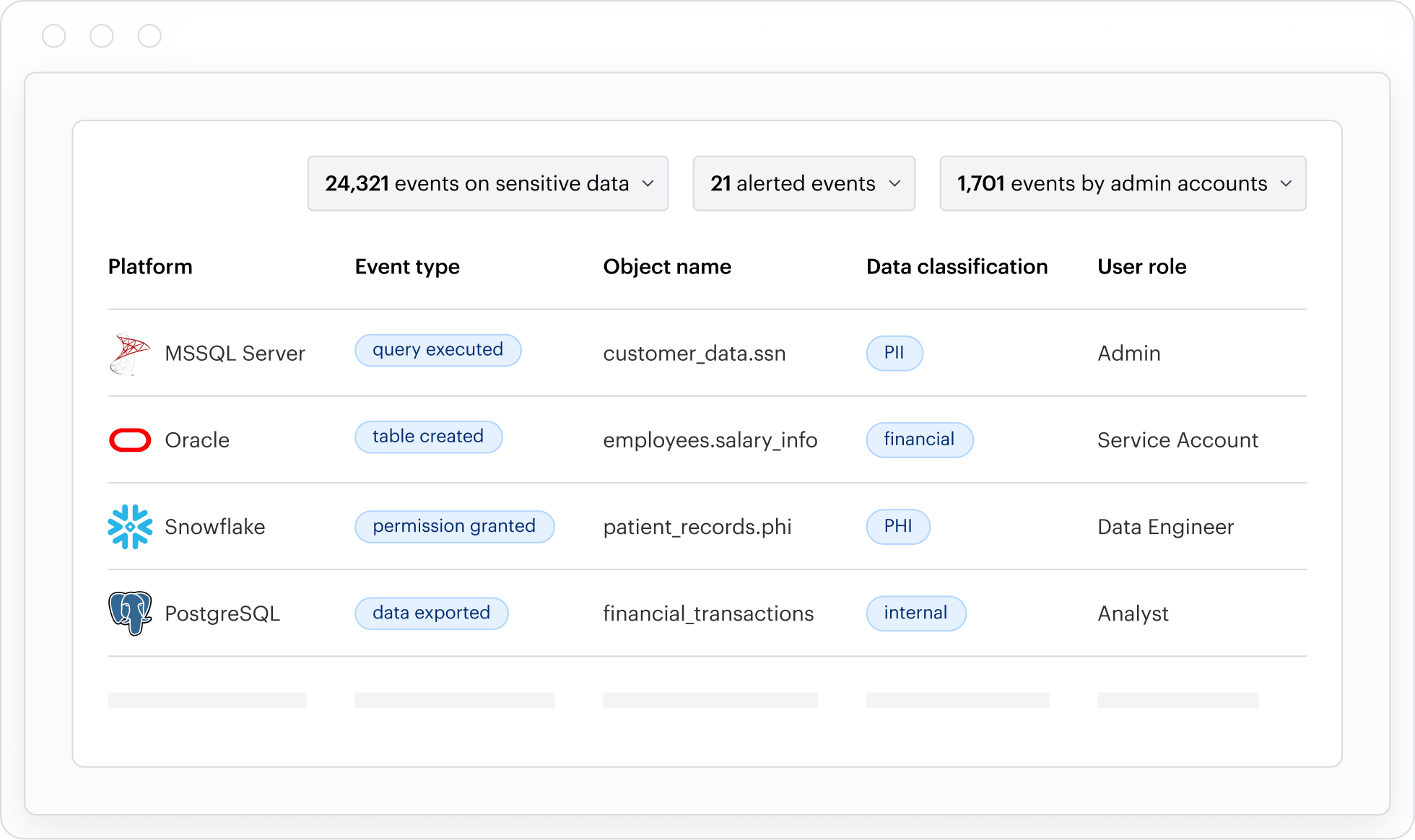
Cyera gives you partial visibility.
Cyera relies on periodic, sample-based scans, which results in incomplete coverage and stale findings. That makes it difficult to product compliance reports requiring a full accounting of sensitive data and easy to miss exposures outside the sampled set.
Varonis uses true incremental, event-driven scanning to classify data continuously, even at petabyte scale. Our AI-native classification delivers complete, current, and contextual visibility you can act on. No blind spots.
Why it matters: Regulatory audits and security decisions require full data inventories, not statistical approximations.
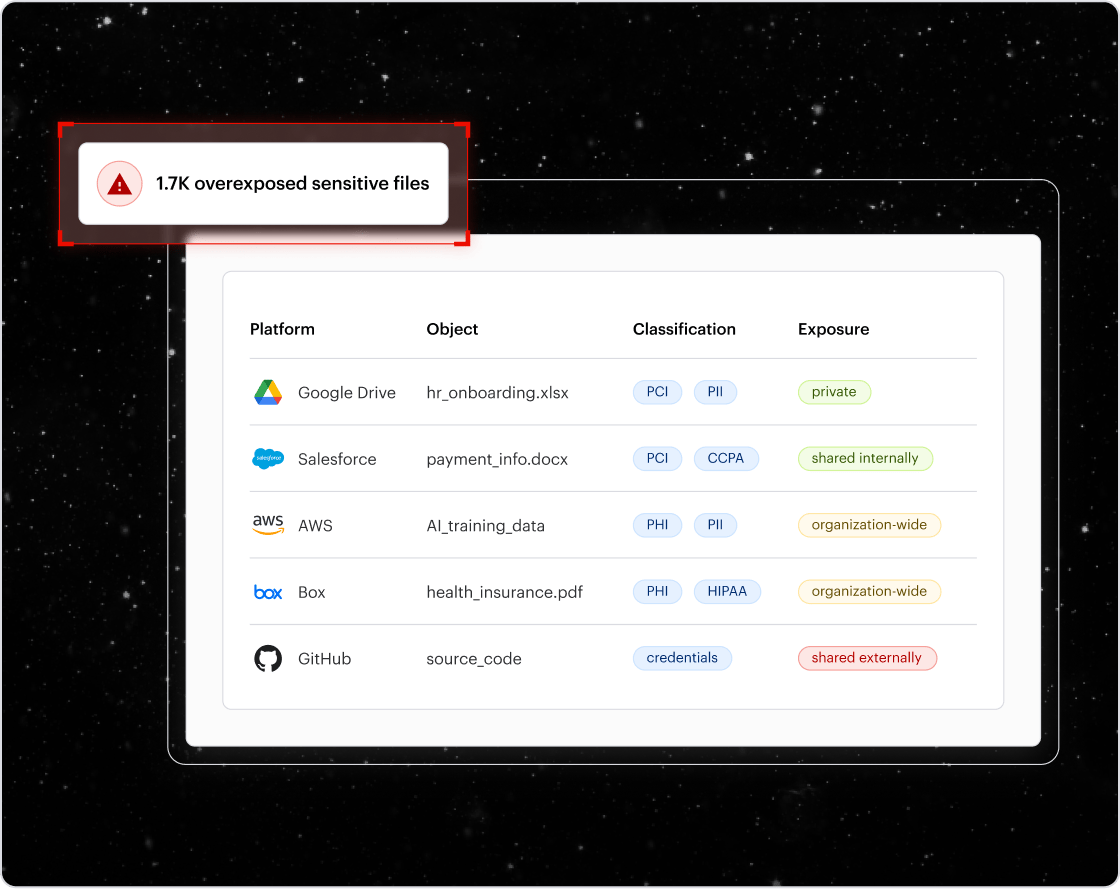
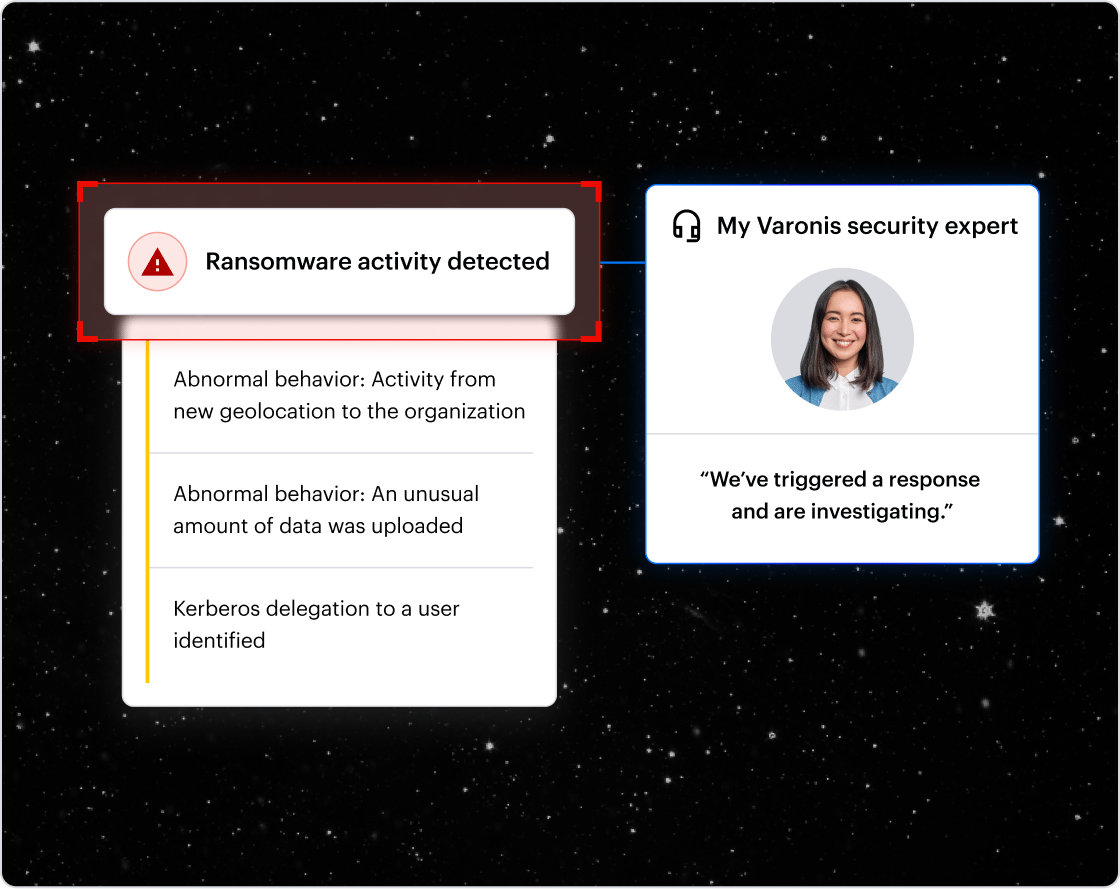
Cyera can't detect threats to your data.
Cyera is limited to flagging static posture issues like misconfigurations and policy violations. With short audit retention and no behavior analytics, it cannot detect insider threats, compromised identities, or active attacks, nor support forensic investigations.
Varonis audits every data access, applies advanced behavioral analytics, and retains activity indefinitely. Combined with 24x7x364 Managed Data Detection and Response (MDDR), Varonis continuously detects, investigates, and responds to threats, without overwhelming your SOC.
Why it matters: Data breaches are caused by attackers and insiders abusing access in real time, not by misconfigurations you plan to fix later.
Cyera charges you a remediation tax.
Cyera depends on third-party workflows to create tickets for issues that teams must manually remediate. Even labeling-based fixes are capped, effectively limiting how much risk you can resolve without additional cost.
Varonis delivers native, automated remediation with no artificial caps. We continuously remove excessive permissions, revoke stale access, and lock down exposed data, and remediate identity-driven risk - processing millions of changes at enterprise scale.
Why it matters: Remediation should be a built-in security outcome, not an added cost or manual burden.

"It’s obvious Varonis is innovating at a rapid pace. They’re being very, very aggressive and making improvements to the platform that I can see on a week-to-week basis. It’s pretty amazing."
Beau Monday
Chief Information Security Officer, Punahou School
"Varonis enables me to provide reassurance that our data is looked after and audited properly."
Ian Siggers
Infrastructure Services Manager, KMPT
"The decision to invest in Varonis has improved our data visibility to a degree we couldn’t achieve manually."
Chris Jessup
Information Systems Security Officer, Anglian Windows Ltd.
Frequently asked questions
Varonis is the leader in data security while Cyera is a data discovery vendor.
Cyera’s product is designed to generate discovery reports and Jira tickets, not stop breaches or automatically reduce your blast radius.
Varonis continuously monitors every data touch, right-sizes the blast radius for every user and agent, and detects threats in real time with behavioral analytics backed by 24x7x365 MDDR.
Organizations should choose Varonis when they need more than data discovery. Choose Varonis if your goals are to avoid a data breach, comply with regulations, and securely adopt AI.
Choose Cyera if your goal is to visualize and categorize the data types within a portion of your data estate.
Discover Next-Gen DAM For Yourself
There's a new way to approach database activity monitoring.
Scale data security across thousands of databases (in the cloud and on-prem) without slowing down.
No agents. No fines. No breaches.
Schedule a personalized, 30-minute call to discuss how Varonis next-gen DAM can help you secure both structured and unstructured data in ONE unified platform.
Thank you for registering!
Add to calendar:
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO

"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO

Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO

"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO

