It’s a familiar data security story: under-patched Windows software, hidden security vulnerabilities, and hackers who know how to exploit them. But if the patch involves Windows Remote Desk Protocol (RDP), as it did with the newly discovered BlueKeep vulnerability you’d think companies would have learned by now the first commandment of infosec: thou shalt not expose RDP on the public Internet.
Even a quick Google search of “RDP vulnerability” reveals that significant vulnerabilities and practical exploits have been discovered year after year. For fun, take a look at this post, which lists all the CVEs from 2018 alone!
Get the Free Pentesting Active
Directory Environments E-Book
Tangled Up in BlueKeep and EternalBlue
In May, Microsoft announced it found yet another vulnerability (CVE-2019-0708) in RDP and urged companies to patch as “quickly as possible”. Dubbed BlueKeep, this latest RDP glitch has gotten Microsoft worried enough to issue a second warning.
What made Big Blue so concerned? This latest RDP vulnerability could allow hackers to remotely run code at the system level without even having to authenticate. In other words, any unpatched Windows system (from XP to Windows 7) with an exposed RDP port is a potential target.
And then to make matters even bluer, hackers now have at their disposal the NSA-leaked EternalBlue, which could turn a working BlueKeep exploit into a wormable virus that would unleash ransomware on a global scale, similar to NotPetya!
Potential BlueKeep Risk: Take it Away Shodan
BlueKeep also got the attention of the Department of Homeland Security (DHS), which issued its own warning last week. This came on the heels of the Department’s successful efforts in crafting and testing a Proof of Concept (PoC) for an exploit.
Keep in mind that it takes significant technical resources — far outside of what a typical hacker can cobble together — to go from a security hole to code that takes advantage of it. More on that below.
To make matters even more confusing, there are fake BlueKeep PoCs running around. With more legitimate researchers claiming PoCs, we have to take the potential for damage very seriously. Even the, cough, NSA is saying “It is likely only a matter of time before remote exploitation code is widely available for this vulnerability.”
So if you haven’t already, patch today! There are quick mitigations and longer term solutions for this and the next BlueKeep, which I’ll get to at the need.
Let’s take a small detour. For those who want to play security analyst and scope out the potential target-scape for RDP-related vulnerabilities, get familiar with Shodan, referred to as the “hacker’s Google”.
Their own web copy is more accurate — “the search engine for the Internet of Things”. Shodan scans the Internet for hosts, routers, web gadgets, collecting public information primarily gathered by parsing banners and html headers, and no doubt probing network information— although they’re somewhat silent about all their sources.
Anyway, if you’d like to see if your own company has exposed RDP or other service ports, simply enter its IP address into Shodan. Not to shame anyone publicly, if you click here, you can see Shodan’s own public profile— they’re very good!
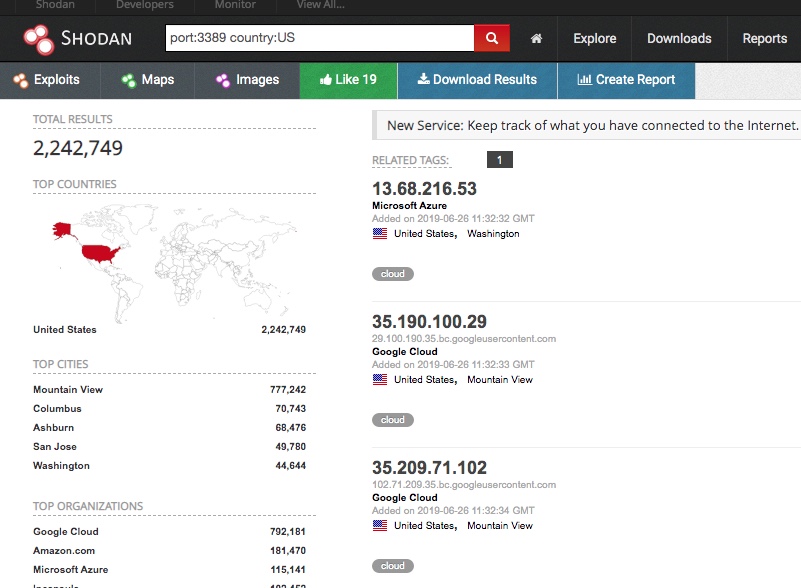
But Shodan goes beyond examining specific companies, allowing you to aggregate security metadata across the Intertoobz. Below you can see the results of a query to discover the number of systems with exposed RDP ports in the US. Answer: over two million. (By the way, on a world-wide basis the number is over five million.)
The bulk of these RDP ports in the US are found in the cloud, divided between Amazon AWS, Microsoft Azure, and Google Cloud. This should not come as a shock to anyone who’s worked with cloud-based Windows images: you download the client-side RDP app to create a virtual desktop on your own laptop.
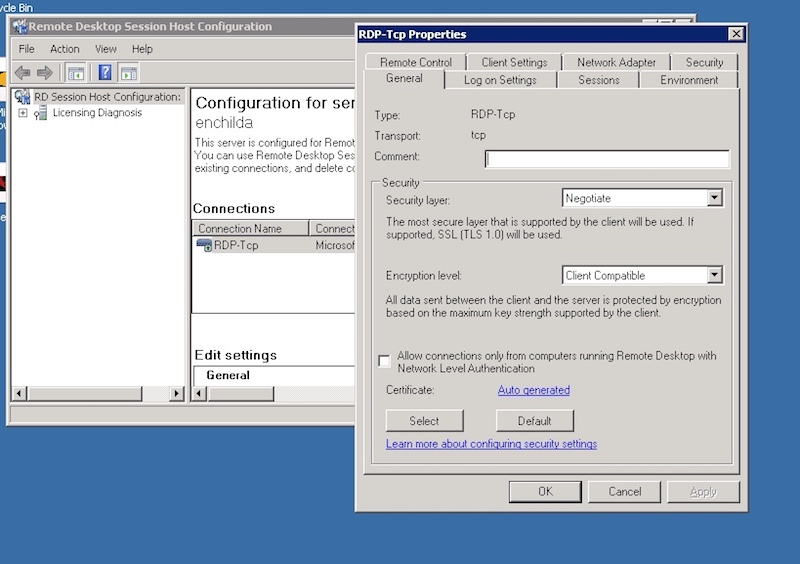
These cloud-based RDP services can be a rich source of BlueKeep victims for hackers. Out of curiosity, I logged into my own AWS domain controller — which I setup once upon a time — to learn whether, by default, AWS has in place one of the mitigations that Microsoft and government agencies have both recommended: enabling Network Level Authentication for RDP to prevent hackers from triggering BlueKeep.
In my quick investigation (see below), AWS appears not to set this up by default! Well you’d think Amazon would be more paranoid in their default security settings for RDP — forcing network authentication to prevent packets from flowing in. I suspect the same is true for Azure and Google as well.
Bottom line: companies that thought Windows in the cloud had tighter security will be in for a surprise. Also note that being in cloud doesn’t mean patching is magically taken care of. It’s not!
But besides the patch state, other factors are involved, including the real possibility that many publicly available RDPs ports may not even have an RDP service on the other side — the port just happens to be open.
This teeny analysis led me to a more realistic understanding of the number of BlueKeep vulnerable Windows installations in the wild. It’s certainly not the seven million that was announced and made the headlines.
Then security researcher Robert Graham stepped in and developed a custom RDP scanning script to perform more precise port probing — you can see his work on Github — and he claims the true number of vulnerable Windows installations is closer to one million. That’s still very significant, of course!
In any case, the BlueKeep vulnerability was a good excuse to introduce Shodan, which is a very powerful pen testing tool on its own right. Next month, I’ll delve into Shodan and a closely-related tool called Censys, and explain how both can be used to help find security issues in your company.
Dipping into the BlueKeep Vulnerability
As the security researchers remind us, a vulnerability does not always translate into a working exploit. It ain’t easy to write code, particularly for an RCE or remote code execution exploit.
To get a taste of how researchers go about their jobs, I urge you to read this great piece over at MalwareTech— but have extra-caffeinated coffee available — explaining their BlueKeep analysis. In short: take a Microsoft patch, do a bindiff, reverse engineer to grok it, and test out ideas in a debugger.
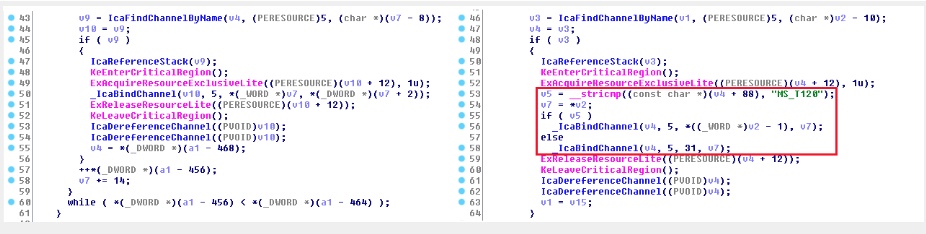
They learned that the unpatched version of RDP allows you to gain access to a chunk of kernel memory, and then potentially perform an RCE or at a minimum crash the target system in a DoS style attack.
If you’re really, really curious to learn how you move from memory errors to an exploit, check out this very detailed post on the subject. Let’s just say the theme of memory leaks and corruption is not a new one to RDP!
As far as I know, there isn’t a publicly released PoC though there are some fakes being put out by fast-buck artists. As I mentioned earlier, we have claims from among others, DHS and the NSA, of real exploit code, so we have to assume that smart hackers will develop their own code.
I offer for your entertainment this video from independent security researcher Zǝɹosum0x0 showing his exploit in action:
Quick Mitigations for BlueKeep
And now for the cheatsheet summary of what we know about CVE-2019-0708 so far.
Systems Affected:
Windows 7
Windows Server 2008
Windows Server 2008 8R2
Windows Server 2003 SP2
Windows Visa
Window XP
Exploit potential: RCE (Remote Code Execution), and worm potential without the EternalBlue patch.
Security Patches: available.
Number of potential victims: ~ 1 million
If you’re in panic mode after finding all this out for the first time, then the quickest mitigation is to turn off port 3389 on your enterprise firewalls, install the security patches, and then re-enable the ports. Expect some angry calls.
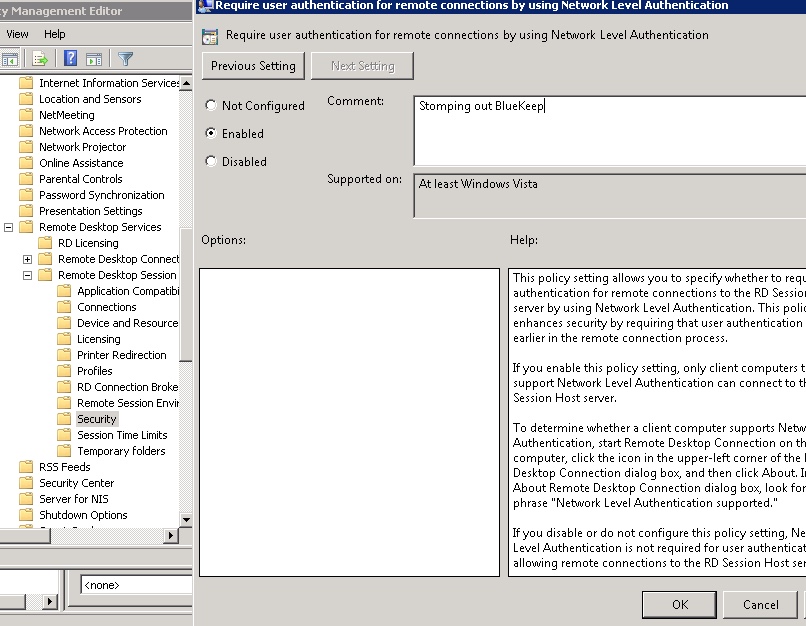
A less disruptive approach is to enable network level authentication, which I explained above. To do this on a domain-level basis, you’ll need to configure the right GPO entry: Computer Configuration\Policies\Administrative Templates\Windows Components\Remote Desktop Services\Remote Desktop Session Host\Security.
And Along Came Varonis
And for the longer term, you’ll want to disable remote desktop services externally, and perhaps allow it internally or over a VNC (virtual network computing). There are some tricks for configuring Windows Firewall for just this kind of situation.
What’s the ultimate answer to all this? Not it’s not 42!
The larger issue is that no one can anticipate when and where the next BlueKeep will show up. But we do know that when it does comes along, the hackers will also use ransomware as the payload in order to richly monetize their hackery.
A smarter approach, then, is to have a threat model that can detect ransomware. The hackers will always find another way to get in, so you have a backup defense to spot and stop their real goal — locking up your files.
While it’s great to know about bindiff, heap overflows, and NSA-inspired malware, Varonis has a real-world solution that will prevent the next attack from taking down your systems. Learn more today!
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







-1.png)

