This month, Varonis released new updates to help organizations secure databases, improve cloud posture, and visualize complex Salesforce permissions.
Our new functionality includes:
- Next-Gen Database Activity Monitoring (DAM)
- CSPM enhancements
- Salesforce access graph
- Data Segmentation in Box and Google Workspace
- AWS GovCloud support
- AWS Resource Control Policy (RCP) mapping
Continue reading for all the details.
Next-Gen Database Activity Monitoring (DAM)
Varonis Next-Gen DAM offers customers a scalable way to protect data across their on-premises, cloud, and hybrid database environments with minimal operational overhead. Unlike legacy DAM solutions that take years to deploy and require dedicated teams to manage, Varonis delivers next-generation database security that deploys fast, requires zero operational overhead, and provides actionable insights with complete visibility across your databases.
With Varonis Next-Gen DAM, security teams and database administrators (DBAs) can identify sensitive data, right-size everyone's access to that data, and prevent unauthorized activity across all their databases.
Varonis Next-Gen DAM makes it simple to answer critical questions such as:
- What sensitive data resides in our databases?
- Which users, services, applications, and AI tools can access and modify our sensitive data within each of our databases?
- Which users, services, applications, and AI tools have accessed which data over the past day, week, month, and year?
Varonis offers organizations complete security, visibility, and control over sensitive data across their entire database portfolio, delivering the key capabilities required to secure data in the modern enterprise.
Learn more about Varonis’ Next-Gen DAM.
Get alerts on suspicious and risky database actions.
Get alerts on suspicious and risky database actions.
CSPM enhancements
Varonis now identifies more than 600 security risks and misconfigurations across AWS, Azure, and Google Cloud. This expanded coverage gives security teams greater visibility into potential security risks, ranging from overly permissive IAM roles to exposed storage buckets and misconfigured EC2 settings.
In addition to detecting risks natively in the Varonis Platform, Varonis now integrates with Azure Policy and Wiz to ingest misconfigurations and risks identified by these tools, such as publicly accessible EKS clusters and AWS IAM policies granting full administrative privileges. These findings are consolidated into a single, unified view, allowing security teams to avoid switching between multiple dashboards or manually correlating results.
By surfacing these risks directly within the Varonis platform, teams can quickly assess their cloud security posture and automatically remediate issues before attackers can exploit weaknesses and exposure.
Learn more about Varonis’ CSPM enhancements
Correlate cloud misconfigurations with data sensitivity and user permissions.
Correlate cloud misconfigurations with data sensitivity and user permissions.
Salesforce access graph
The Salesforce access graph simplifies permissions analysis, making it easy to understand different users, profiles, permission sets, and permission set groups. The Salesforce access graph makes it simple to understand exactly what a user can access and do in Salesforce.
Get a bi-directional view of the resources that your Salesforce users can access and the origins of their permissions. Users can simply zoom into each connected element to find overexposure and access pathways.
Varonis factors in profiles, permission sets, groups, roles, inheritance, sharing rules, direct sharing, and muted permissions into its analysis of effective permissions, making it simple to understand where your sensitive Salesforce data is exposed to risk.
Visualize effective user permissions in Salesforce to quickly identify where data is exposed to risk.
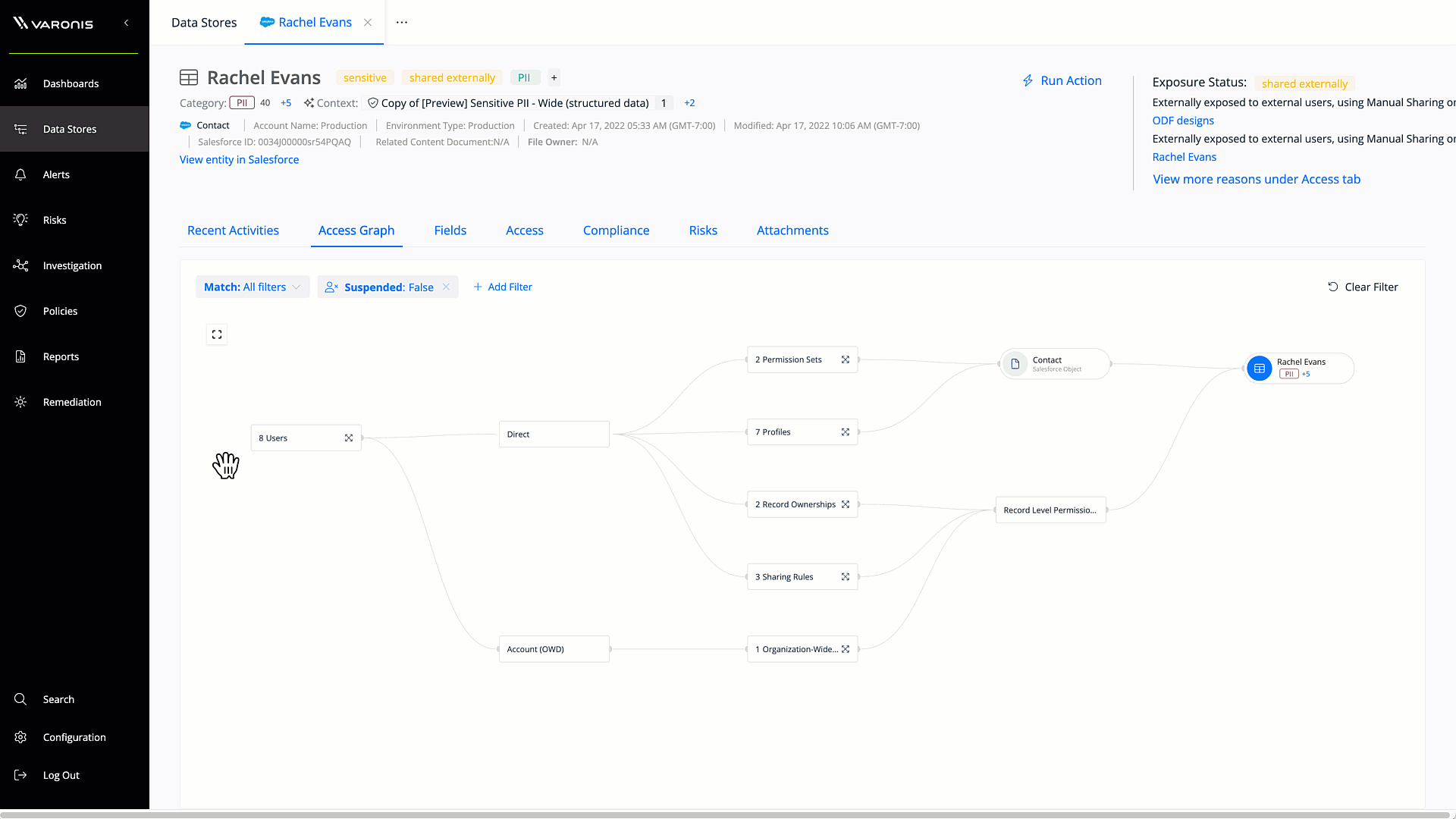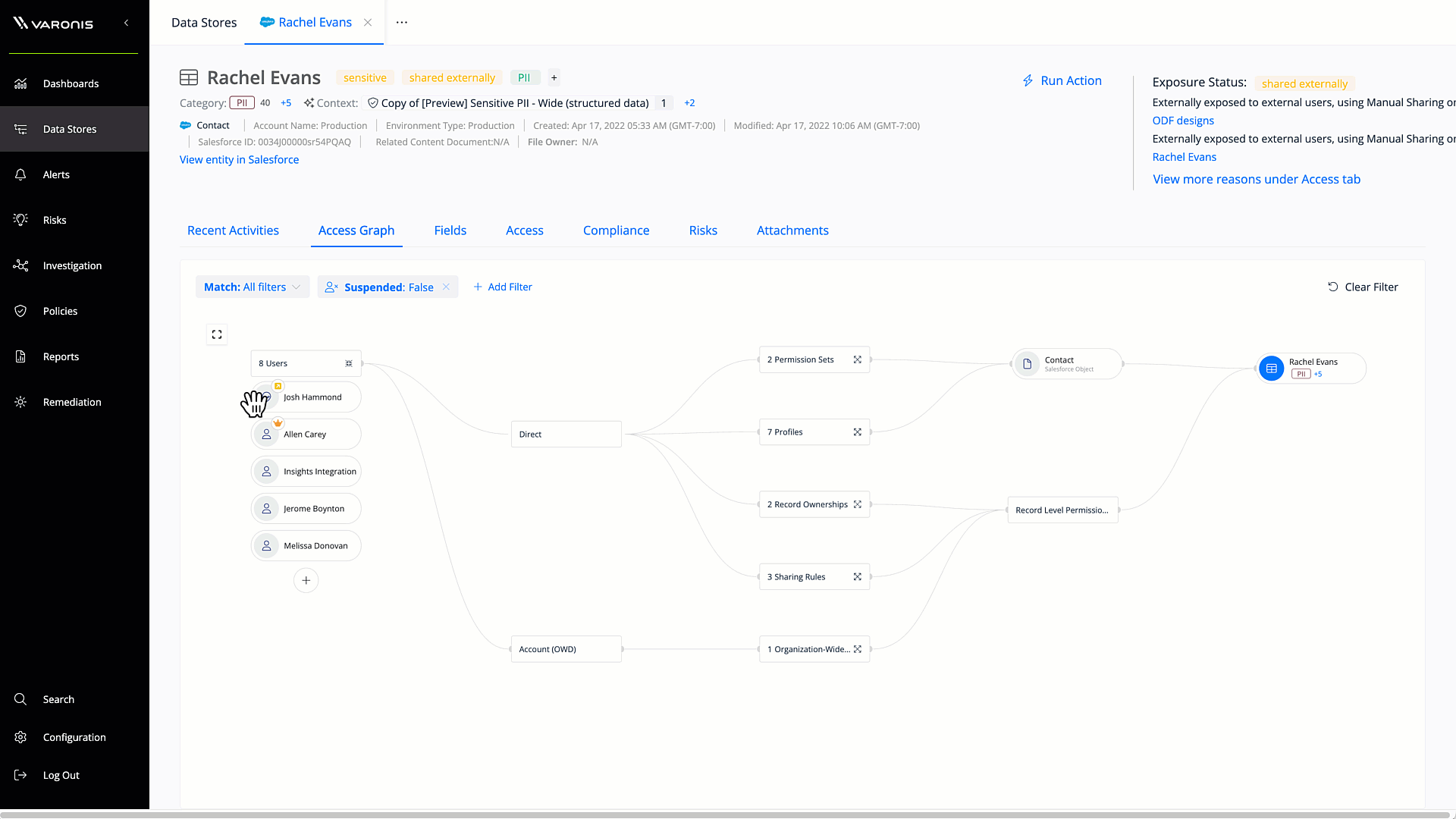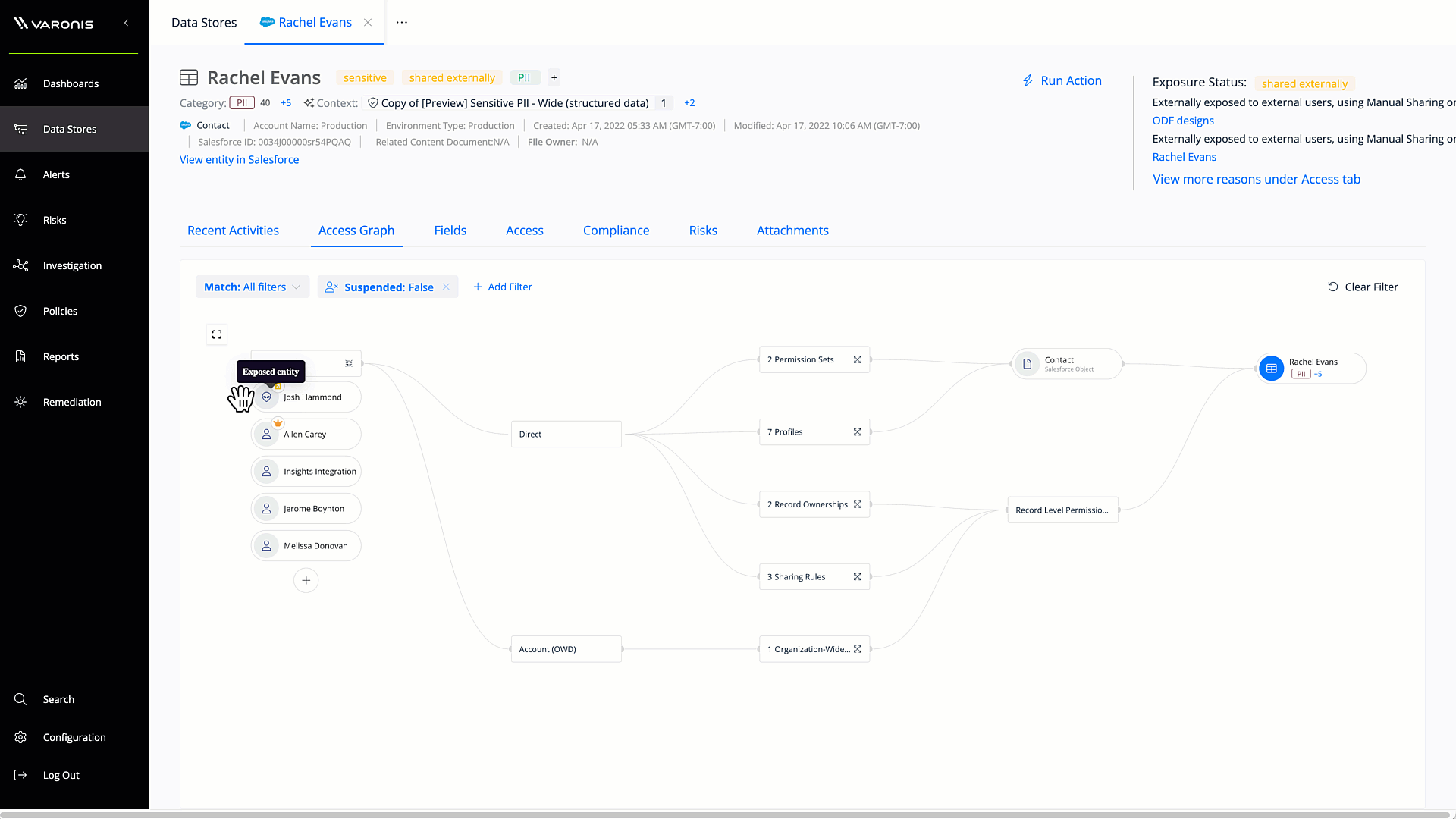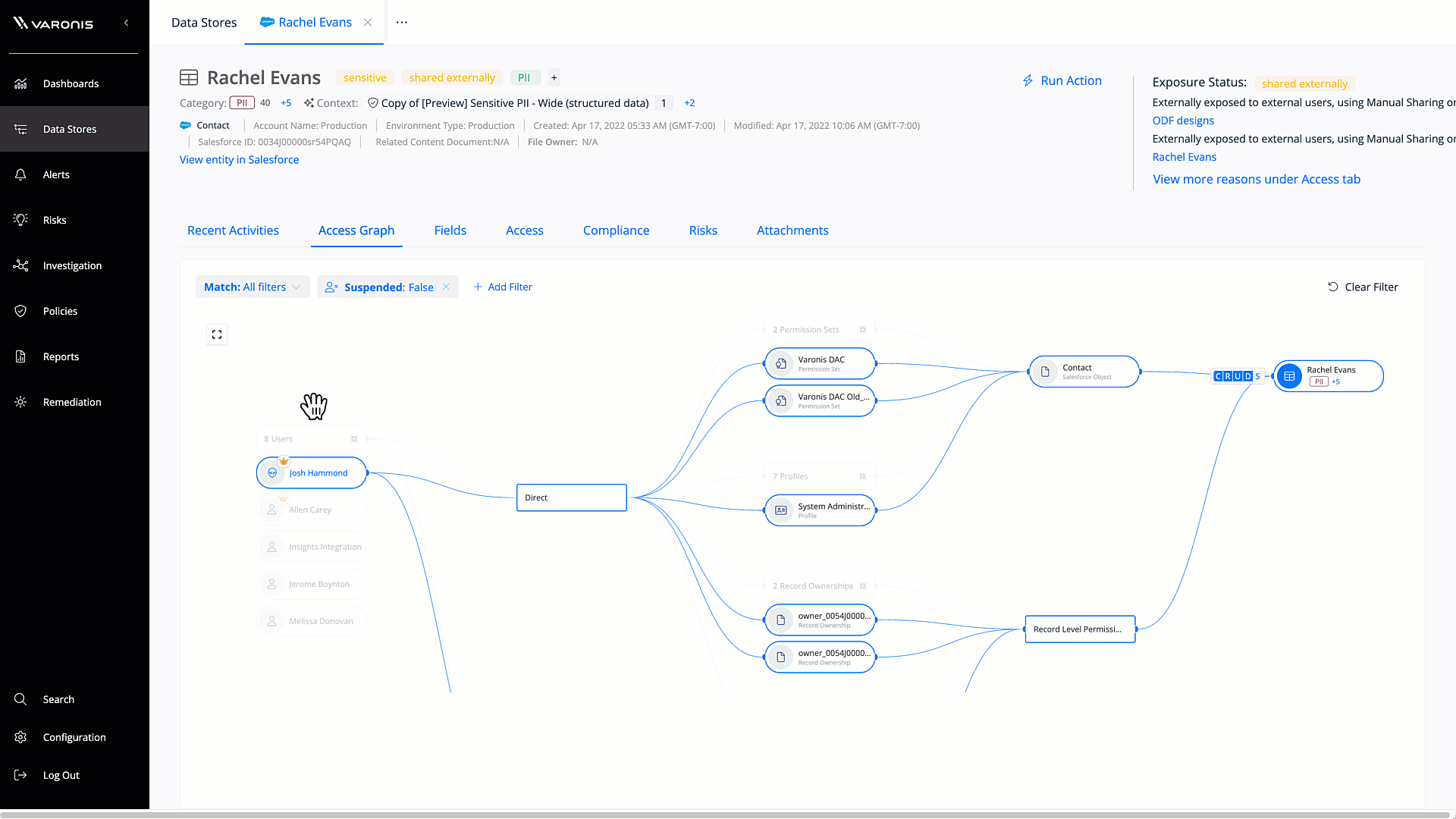
Visualize effective user permissions in Salesforce to quickly identify where data is exposed to risk.
Data Segmentation in Box and Google Workspace
Varonis now enables data segmentation in Box and Google Workspace. Users now only see data and activity within their assigned segments across the Varonis platform. Segments may include Google Org Units, Box Zones, full service accounts, and individual accounts.
Segments are defined by scopes, which can be as granular as:
- The entire service
- Specific accounts within the service
- Specific sub-units within the service
Activities and alerts are visible exclusively when the actor or one of the targets falls within the scope of the user's segment.
This enhancement gives organizations more granular control over separation of duties, ensuring users access only the information relevant to their roles and responsibilities — strengthening both security and operational clarity.
Configure and assign users to specific segments.
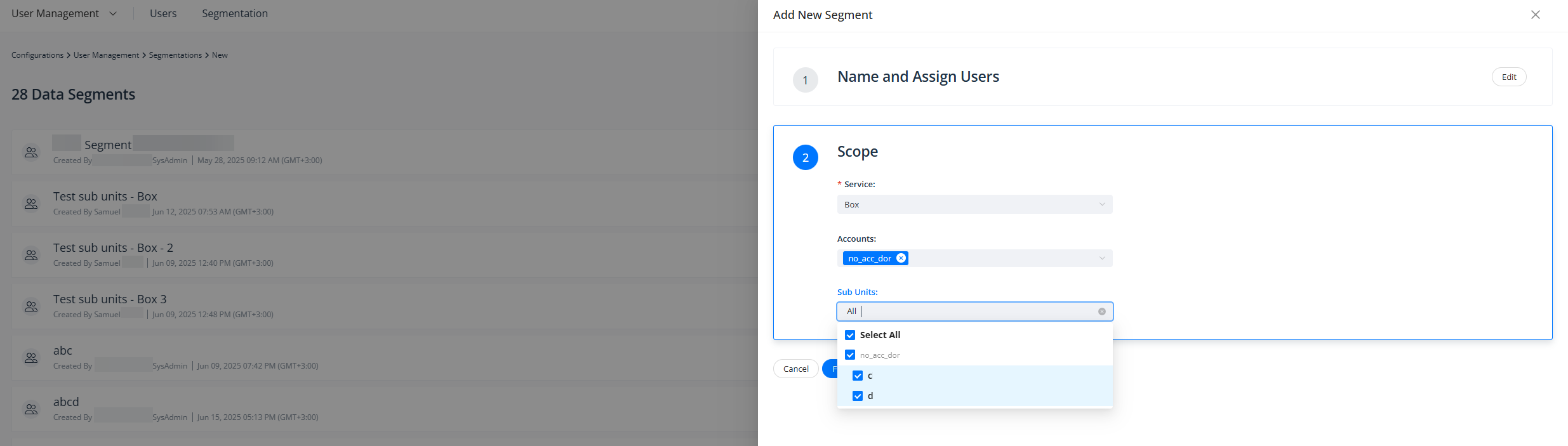
Configure and assign users to specific segments.
AWS GovCloud Support
Varonis now supports AWS GovCloud (US) — bringing our powerful Data Security Platform to the cloud environment purpose-built for sensitive government workloads.
With Varonis for AWS GovCloud, agencies can:
- Discover and classify sensitive data like CUI and PII across AWS resources
- Automatically eliminate unnecessary permissions and sensitive data risk
- Detect and respond to insider threats and cyberattacks with real-time alerting and automation
- Support Zero Trust initiatives and meet compliance mandates with ease
This expansion builds on Varonis’ existing FedRAMP® Moderate Authorization and Microsoft GCC/GCC HIGH support, ensuring that Varonis meets the U.S. government’s rigorous cloud security standards while delivering powerful data security wherever your data resides.
AWS Resource Control Policy (RCP) mapping
AWS recently introduced Resource Control Policies (RCPs), a new mechanism for managing permissions to resources within AWS accounts.
Varonis has strengthened its CIEM capabilities by incorporating the analysis of RCP policies into its effective access calculations. This provides a more complete and accurate view of identity access across AWS environments.
Keep up with the latest Varonis product releases
Varonis’ offerings move fast! Discover product updates you may have missed on our blog.
For more information, including release notes, customer training, and how-to videos, visit the Varonis Community.
See Varonis in action and request a demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.

.png)







