Remember the first large-scale Mirai attack late last year? That was the one directed at IP cameras and took advantage of router configurations settings that many consumers never bother changing. The main culprit, though, was Universal Plug and Play or UPnP, which is enabled as a default setting on zillions of routers worldwide.
What is UPnP?
If you’ve ever plugged a USB keyboard into a laptop, you’ve lived the “plug and play experience”, but things are often not so straightforward with networked devices. How does a new printer, camera, coffee pot or toy know how to attach to your network and then configure your router to allow for port access?
Discover the Top 5 Remote Security Threats to your workforce with our free whitepaper
UPnP is a convenient way of allowing gadgets to find other devices on your network and if necessary modify your router to allow for device access from outside of your network. Via the Internet Gateway Device Protocol, a UPnP client can obtain the external IP address of for your network and add new port forwarding mappings as part of its setup process.
This is extremely convenient from a consumer perspective as it greatly decreases the complexity of setting up new devices. Unfortunately, with this convenience have come multiple vulnerabilities and large-scale attacks which have exploited UPnP.
UPnP: The Danger
However, this convenience factor provides an opening for hackers. In the case of Mirai, it allowed them to scan for these ports, and then hack into the device at the other end.
Hackers have now found an even more diabolical use of UPnP with the banking trojan Pinkslipbot, also known as QakBot or QBot.
Around since 2000, QakBot infects computers, installs a key logger, and then sends banking credentials to remote Command and Control (C2) servers.
Remember C2?
When we wrote our first series on pen testing, we described how remote access trojans (RATs) residing on the victims’ computers are sent commands remotely from the hackers’ servers over an HTTP or HTTPS connection.
This is a stealthy approach in post-exploitation because it makes it very difficult for IT security to spot any abnormalities. After all, to an admin or technician watching the network it would just appear that the user is web browsing — even though the RAT is receiving embedded commands to log keystrokes or search for PII, and exfiltrating passwords, credit card numbers, etc. to the C2s.
The right defense against this is to block the domains of known C2 hideouts. Of course, it becomes a cat-and-mouse game with the hackers as they find new dark spots on the Web to set up their servers as old ones are filtered out by corporate security teams.
And that’s where Pinkslipbot has added a significant innovation. It has introduced, for lack of a better term, middle-malware, which infects computers, but not to take user credentials! Instead, the middle-malware installs a proxy C2 server that relays HTTPS to the real C2 servers.
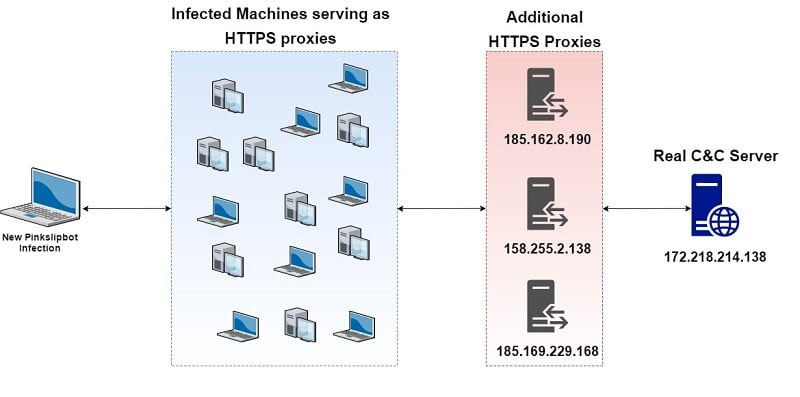
The Pinkslipbot infrastructure therefore doesn’t have a fixed domain for their C2 servers. In effect, the entire Web is their playing field! It means that it’s almost impossible to maintain a list of known domains or addresses to filter out.
What does UPnP have to do with Pinkslipbot?
When the Pinkslipbot is taking over a consumer laptop, it checks to see if UPnP is enabled. If it is, the Pinkslipbot middle-malware issues a UPnP request to the router to open up a public port. This allows Pinslipbot to then act as a relay between those computers infected with the RATs and the hackers’ C2 servers (see the diagram).
It’s fiendish, and I begrudgingly give these guys a (black) hat tip.
One way for all of us to make these kinds of attacks more difficult to pull off is to simply disable the UPnP or port-forwarding feature on our home routers. You probably don’t need it!
By the way, you can see this done here for my own home Linksys router. And while you’re carrying out the reconfiguration, take the time to come up with a better admin password.
Do this now!
Security Stealth Wars: IT Is Not Winning (With Perimeter Defenses)
Phishing, FUD malware, malware-free hacking with PowerShell, and now hidden C2 servers. The hackers are gaining the upper-hand in post-exploitation: their activities are almost impossible to block or spot with traditional perimeter security techniques and malware scanning.
What to do?
The first part is really psychological: you have to be willing to accept that the attackers will get in. I realize that it means admitting defeat, which can be painful for IT and tech people. But now you’re liberated from having to defend an approach that no longer makes sense!
Once you’ve passed over this mental barrier, the next part follows: you need a secondary defense for detecting hacking that’s not reliant on malware signatures or network monitoring.
I think you know where this is going. Defensive software that’s based on – wait for it — User Behavior Analytics (UBA) can spot the one part of the attack that can’t be hidden: searching for PII in the file system, accessing critical folders and files, and copying the content.
In effect, you grant the hackers a small part of the cyber battlefield, only to defeat them later on.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







-1.png)

