You don’t normally talk philosophy and IT when considering Bash and Powershell, but if it’s one thing I’ve learned over the past 20 years of sysadmin work it’s that whether you’re an Empiricist, Nihilist or Young Hegeliansist, if you’re serious about doing your job you don’t spend your day clicking on buttons, you run your network from a command line.
I bring this up because the first thing anybody writes is that PowerShell and Unix shells have a “different philosophy”. Mostly this boils down to PowerShell pushing around structured data. Unix shells push around globs of text.
Get the Free PowerShell and Active Directory Essentials Video Course
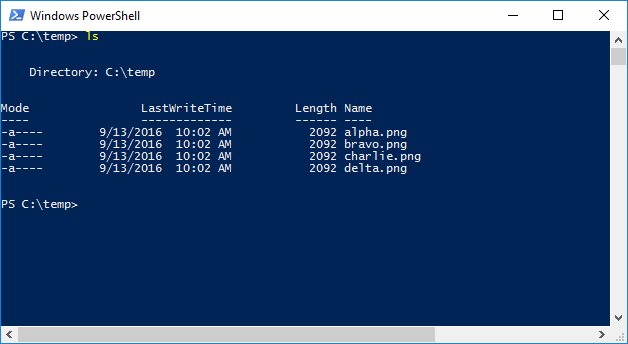
An example–list the files in the current directory:
With PowerShell:
PS C:temp\> ls
/temp/ls
So, what you’re seeing above may look like just a list of files, but they are both exercises in responsibility. Who is responsible for how the output is structured. PowerShell’s philosophy is “We’ll handle this for you” and returns the files as a series of objects, that are file objects – the objects have properties like size, created date, etc.
Bash takes the philosophy that you, the sysadmin, are all powerful and can make the determination of what you want to do with this set of strings (that happen to be text representations of filenames).
Both of these work against the third (and sadly still far too widespread) philosophy which is: “I’m not going to learn either of these and will instead just double click the folder to see what’s inside.”
Writing shell scripts is like building something with Lego (or your preferred brand of architectural, interlocking brick system), one brick is underwhelming, but put enough together and you have a miniature Mt. Rushmore cluttering up your basement.
This is why the seemingly trivial aspect of whether it’s objects or a bunch of text you get back is so important. It’s not because you really care as an end result what you get, but more that everything you do with scripting deals with the data that’s returned. It’s less a “script” and more of a data transformation pipeline made up of a bunch of smaller scripts passing data around.
Command Equivalents
| Bash Command | PowerShell Command | Notes |
|---|---|---|
| = != | -eq -ne -ceq -cne | Compares short snippets of text like file or user names. |
| grep | select-string | Finds lines matching a pattern |
| sed | -replace | Performs string substitution. |
| echo | Write-Host | Outputs the value to the screen (good for debugging) |
| var=3 | $var = 3 | Create a variable for $var. |
Credit: https://engineering-computer-science.wright.edu/
Expanding Your Knowledge
Whether you end up using Bash or PowerShell, we highly recommend doing so in as practical a setting as possible. Trying to memorize commands and only working with tiny, isolated scripts never really gives you a chance to put all the pieces necessary together.
We felt so strongly about this that we commissioned a course that embodied this teaching style. It’s 3 full hours of video, costs you nothing and you’ll walk away knowing how to build an Active Directory security utility with PowerShell from the ground up.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.