One morning, you decide to purchase from a seemingly reputable online store. The website displays a familiar checkout interface resembling Stripe's payment process.
You enter your payment details, feeling confident in the website’s legitimacy:
- Credit card number
- Expiration date
- CVV
- Billing address
You even enter a one-time password (OTP) sent to your phone, believing it ensures your transaction’s security. Little do you know, you’ve fallen victim to a new WordPress plugin found on a Russian cybercrime forum: PhishWP.
PhishWP is a WordPress plugin built by cybercriminals. It creates fake payment pages that look just like trusted services, such as Stripe. Threat actors use it to steal sensitive information such as credit card numbers, personal data, and browser metadata.
PhishWP even connects with Telegram, sending stolen data to attackers when a victim hits “enter.” This makes phishing attacks faster and more efficient.
Attackers can either compromise legitimate WordPress websites or set up fraudulent ones to install it. After configuring the plugin to mimic a payment gateway, unsuspecting users are lured into entering their payment details.
The plugin collects this information and sends it directly to attackers, often in real time. PhishWP also uses advanced tricks, like stealing the special OTP sent during a 3D Secure (3DS) check during the checkout process. 3DS is a safety measure that sends a short code to your phone or email to prove you’re the cardholder. By grabbing this code, attackers can pass themselves off as you, making their fake transactions look completely real.
Official advertisement for PhishWP
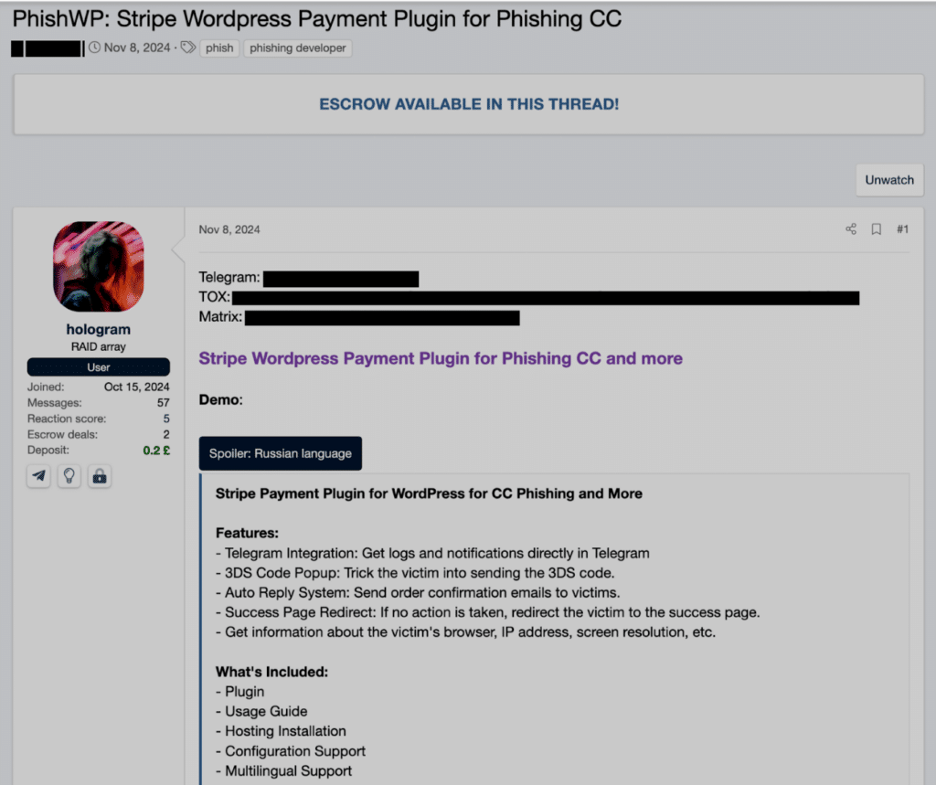
Official advertisement for PhishWP
Key features of PhishWP
How does PhishWP collect your card details, the special code your bank sends you, and a friendly confirmation email — all before you realize you sent your private information straight to a hacker? Let’s look at the specific features PhishWP uses that make it effective in phishing campaigns:
- Customizable checkout pages: Simulate payment processors like Stripe, creating compelling fake interfaces.
- 3DS code harvesting: Tricks victims into entering one-time passwords (OTPs) via pop-ups, bypassing authentication layers.
- Telegram integration: Instantly transmits stolen data to attackers for real-time exploitation.
- Browser profiling: Captures details such as IP addresses, screen resolutions, and user agents to replicate user environments for future fraud.
- Auto-response emails: Send fake order confirmations to victims, delaying suspicion and detection.
- Multi-language support: Enables global phishing campaigns by accommodating multiple languages.
- Obfuscation options: Provides an obfuscated version of the plugin for stealth or source code for advanced customizations.
PhishWP’s features make fake checkout pages look real, steal security codes, send your details to attackers immediately, and trick you into thinking everything went fine. This is why staying alert and using strong security tools is more important than ever.
Example of a phishing attack using PhishWP
Let’s walk through an example. Imagine an attacker creating a fake e-commerce website advertising high-demand products at discounted prices. Using PhishWP, they replicate Stripe payment pages to deceive users.
The attack unfolds as follows: first, users are directed to a convincing fake checkout page where they enter their payment and personal details. Next, a 3DS code pop-up requests an OTP, which users unwittingly provide, believing the site is legitimate.
Meanwhile, the plugin transmits all collected information, including card details and OTPs, to the attacker’s Telegram account in real time. Finally, the attacker exploits the data for unauthorized purchases or sells it on dark web marketplaces.
Example of what the attacker views after a successful attack
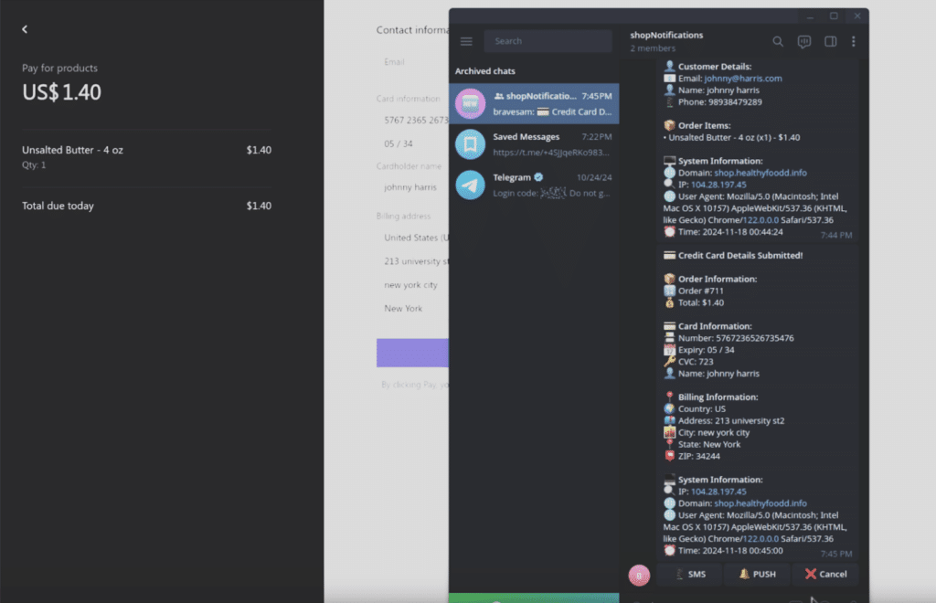
Example of what the attacker views after a successful attack
Here’s the step-by-step breakdown of how attackers put PhishWP to work:
- Set up on a WordPress site: Attackers break into a trusted WordPress site or create their own fake one.
- Copy a real payment service: They use PhishWP to make checkout pages look like a real payment processor (like Stripe), adjusting the design and language so nothing seems off about the branding, fields, or language.
- Lure victims in: Victims arrive at the site through carefully planned phishing emails, social media ads, or sneaky search results. Everything looks normal, so they enter their payment and personal details without a second thought.
- Steal the data: PhishWP scoops up all the sensitive information—credit card numbers, addresses, even special security codes—and instantly sends it to the attacker, often via Telegram.
- Cover the tracks: The victim receives a fake confirmation email, making them believe their purchase went through. Meanwhile, the attacker uses or sells the stolen info in secret online markets.
Get protection with Varonis
Phishing campaigns are getting smarter, faster, and harder to detect. Once credentials are compromised, your sensitive data is wide open. Varonis protects what matters most by automatically finding and fixing exposures, detecting threats in real time, and reducing risk without the busywork.
See how Varonis stops threats before they become breaches — request your demo today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








-1.png)