When it comes to password hacking, most organizations are quite familiar with brute force attacks, where cybercriminals continually guess passwords via computer algorithms tens of thousands of times in seconds until it finds the right one.
However, password spraying is now emerging as an alternative to brute force attacks, skirting login attempt lockout settings that many systems and devices now employ.

With password spraying, hackers take common, non-complex passwords and "spray" them across an entire organization, hoping that a single user might be using something like "abc123," "password," or any one of the most utilized passwords that are publicly available. In this article, we'll explain the basics of password spraying, how a spraying attack takes place, and what you can do to guard against one.
- What is Password Spraying?
- Password Spraying vs Other Password Attacks
- How Password Spraying Attacks Work
- Three Password Spraying Detection Signals
- Three Steps to Remediate a Password Spraying Attack
- How to Prevent Attacks from Password Spraying Campaigns
- Password Spraying FAQs
What is Password Spraying?
Password spraying differs from brute force attacks in that it takes a volume approach, rather than targeting specific users, devices, or accounts. The attacker usually starts with one common password that they hope just one user in the organization is using. If that first attempt is unsuccessful, the hacker will move on to another password and conduct another spraying effort.
Because hackers aren't repeatedly trying to log in to accounts many times over a short span of time, they avoid getting locked out due to an excessive number of attempts. This is why password spraying is also known as the "Low and Slow" method of password hacking. Cybercriminals target low-hanging fruit in the form of common passwords, spraying slowly and continually over a longer period of time until they gain access.
Once access to one machine or account is gained, the goal is to leverage that to access other areas of the system. For example, hackers might enter a user's cloud drive seeking passwords for other accounts or administrator permissions. So while password sprayers might not gain the access to their ultimate target, they effectively get their foot in the door for the purposes of conducting even more malicious activities.
Because over half of all Americans only change their password when they forget it, password spraying is quickly becoming a popular method targeting users who have chosen a common password and never feel the urgency or need to change it.
Password Spraying vs Other Password Attacks
Today, cybercriminals employ a wide variety of password-based attacks to gain unauthorized access to devices, systems, and networks. Here's how password spraying differs from some of the other common varieties of password attacks.
Brute Force Attacks
Brute force attacks employ programs that will continually try thousands of password combinations in an attempt to login to a single account or machine. On the flip side, password spraying only tries to gain access with one password at a time. Brute force attacks can work even with complex passwords - given enough attempts - while spraying targets simple ones. The anatomy of a brute force attack is typically more complex than a spraying one.
Keylogger Attacks
In this type of attack, malicious actors gain access to a user's password by monitoring their physical keystrokes on their computer. This is typically done with malware installed on a machine unbeknownst to the user, but can also be conducted with physical hardware monitoring devices. While password spraying is simply a guess, keylogging attacks pinpoint the exact password as the user is typing it.
Credential Stuffing
In a credential stuffing attack, hackers gain access to a list of compromised accounts or credentials from previous hacks. These credentials can typically be found or purchased on the dark web or amongst hacker circles. Hackers then take a brute force approach to guessing the passwords of accounts already known to be compromised, as opposed to spraying which targets all accounts regardless of any previous compromise.
Phishing Attack
Hackers may also try to harvest a user's password through direct interaction with the individual. The attacker may impersonate a legitimate third-party or service, directing them to a false link and webpage in which the user is prompted to enter their password credentials to what looks like their bank, medical account, or other services. Password spraying involves no such immediately obvious efforts, taking place behind the scenes and unbeknownst to the organization and users.
Traffic Interception
Another way hackers discover passwords is through monitoring data and traffic via wifi networks. Things like messaging apps or email correspondence are targeted and malicious actors attempt to find communications containing passwords. Unsecured wifi connections that don't employ HTTP encryption are particularly vulnerable. Traffic interception requires much more technological overhead and effort, which often makes spraying a more attractive option for malicious actors.
How Password Spraying Attacks Work
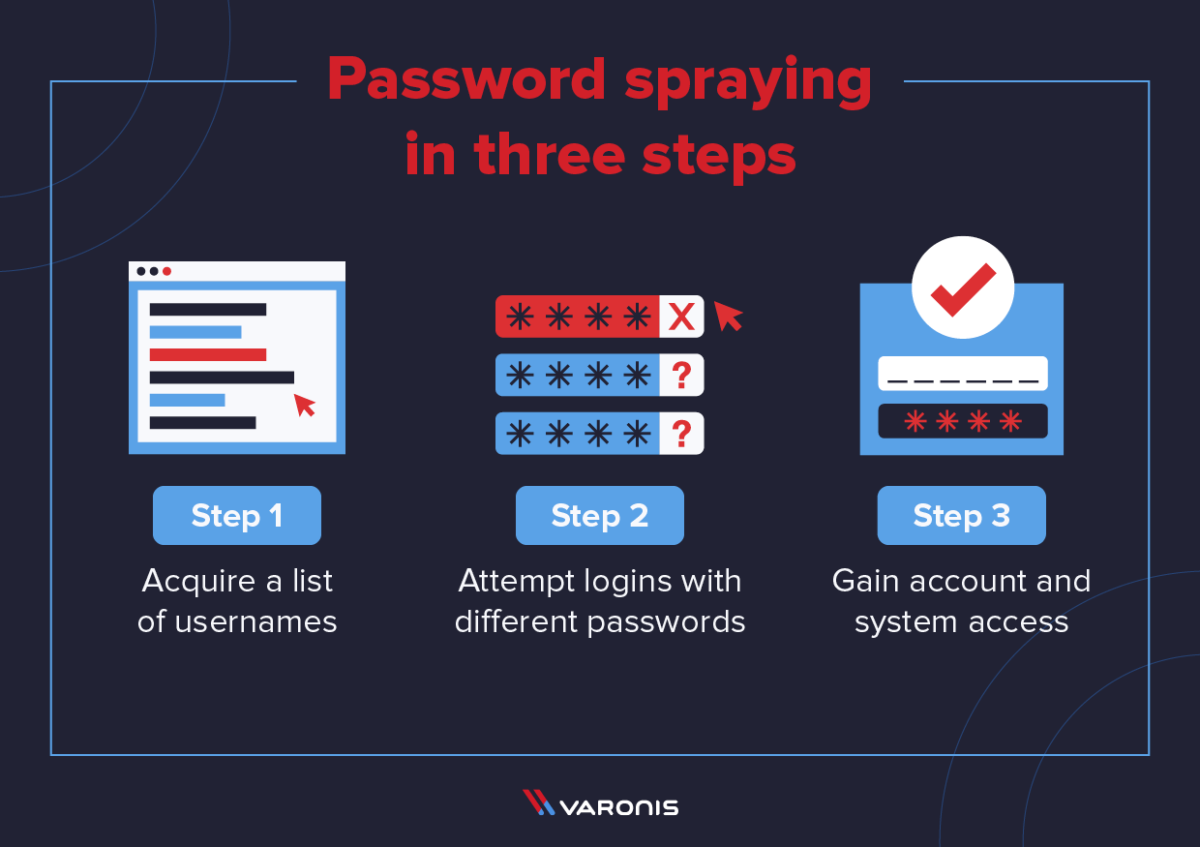
Password spraying attacks typically take place in the following three common sequential steps:
1. Acquire List of Usernames
Gaining a list of username accounts for an organization is often easier than it actually sounds. Most companies have a standardized, formal convention for emails that double as account usernames, such as firstname.lastname@company.com. They can then use software to validate the accuracy of usernames that they think exist. Alternatively, username lists can also be purchased online via the dark web. Sometimes usernames and corresponding email addresses are even readily available on the company's site or user's online profiles.
2. Begin Spraying Passwords
Locating a list of commonly used passwords is also extremely easy. The top passwords each year can be found with a simple Google or Bing search, and are even published on Wikipedia. While these can be good choices for spraying, hackers may also take regional differences into account. For an organization located in Dallas, for instance, hackers may choose a popular sports team such as "Cowboys," since a great many users take this simplistic, easy-to-remember approach for their passwords. After they've sprayed the first password, attackers will wait at least 30 minutes to try the next one to avoid triggering a timeout.
3. Gain Account & System Access
In many cases, one of the common passwords will indeed work against a single account in the organization. If only one user isn't following password tips and best practices, the spraying attack is successful. Once access is granted, the hacker can then access a myriad of accounts and services for that individual. The attacker then uses that access to do internal reconnaissance, target deeper networks, or gain access to other accounts with elevated privileges. The breadth of access that a spraying attack can grant makes the effective and complex generation of passwords much more critical for organizations.
Three Password Spraying Detection Signals
One of the best things you can do to prevent falling victim to password spraying attacks is proper detection. Here are three signs to look for that indicate your systems and organization may be in the midst of a password spraying attack.
1. Sudden Spike in Failed Logins
Since password spraying covers so many accounts within an organization at once, a high number of failed login attempts within a short time span is one indication of password spraying.
2. High Number of Locked Accounts
Password spraying avoids timeouts by waiting until the next login attempt. However, if you see an unusually high number of locked accounts this could be a clue that hackers have sprayed once, gotten locked out, and are waiting to try again soon.
3. Unknown or Invalid User Attempts
Hackers conducting password spraying aren't likely to have a completely accurate list of username credentials. They're either guessing or have purchased an outdated list online. If you see old employees or invalid usernames trying to log in, it might be password spraying.
Three Steps to Remediate a Password Spraying Attack
If you do manage to detect a password spraying attack in progress, follow these steps to protect vulnerable accounts and strengthen your defenses against future password spraying efforts.
1. Change Organizational Passwords
The first thing you'll want to do is alert all personnel within the organization to change and update their passwords. Inform them not to use common passwords or simple phrases and combinations. Give them guidelines on how to create a sufficiently complex password or provide them with a password generation tool.
2. Implement and Audit Incident Response Plan
Every company should have a cyber incident response plan of some kind. If you suspect a password spraying attack, then you should begin implementing the steps you have outlined immediately. Once you feel like your user accounts are secure, you'll want to review and audit the plan to make sure that remediation activities specific to password spraying attacks are included.
3. Configure Security Password Settings
If your organization utilizes a Security Logging Platform, ensure that it's configured to identify or detect failed login attempts across all systems. This will help you detect those tell-tale signs of password spraying attacks in the future as well as any that are currently ongoing. It will also increase your investigation capacity by gaining visibility into all failed login activities.
How to Prevent Attacks from Password Spraying Campaigns
Now that you're fully aware of what password spraying attacks are and what actions to take if you detect one, you'll want to put the right infrastructure in place to prevent future spraying efforts from being successful.
Enable Active Directory Password Protection
Many systems, like Microsoft Azure, for example, allow administrators to eliminate common or easily guessed passwords from being used altogether. If you have this option, you'll want to enable it. By banning passwords most prone to spraying attacks from the get-go, you head hackers off at the pass. You can also include custom lists of common passwords that might be relevant to your specific industry, company, or region. If your company is in the software industry, for instance, you might want to ban a password like "SteveJobs123."
Conduct Simulated Attacks or Pen Testing
Whether you conduct one yourself or with the help of your cybersecurity partner, a simulated password spraying attack will help gauge how vulnerable your organization's password measures are. For example, some attack simulation software will let you pick a list of common passwords and report back on how many users in your company have that. Simulating spraying attacks will also allow you to test various region or industry-specific passwords, and decide which ones should be included on your customized ban list.
Implement Passwordless User Access
One of the most sure-fire prevention measures against spraying is to eliminate the use of passwords in your business altogether. This means implementing technology such as biometric or voice-activated user access, which is extremely difficult for hackers to steal, duplicate, or log in with (for now). At the very least, you should enable multi-factor authentication (MFA) so that a password alone isn't sufficient to gain system or device access. But ultimately, a fully passwordless infrastructure may be the ultimate defense against password spraying.
Use Varonis Solutions to Your Advantage
Password spraying is one of the many data security risks posed by hackers today. Once inside, an attacker can gain persistent access, exfiltrate sensitive data, and unleash ransomware. Threat detection and response solutions like Varonis DatAlert can help organizations protect their mission-critical data from cyberattacks before damage is done.
Varonis utilizes behavior-based threat models to detect early signs of compromise, like password spraying from a single source or an unusual number of account lockouts. We monitor data activity to spot potential threats like abnormal access to sensitive data. Alerts can also trigger automated responses like terminating affected users' sessions or changing passwords to help stop an attack in its tracks. With a human-readable audit trail, Varonis can also help reduce overall investigation times to password spraying attacks by upwards of 90% according to a study by Forrester Research.
Beyond detection, Varonis enables you to visualize your risk and dramatically reduce your attack surface by eliminating excessive access to sensitive data automatically.
Want to learn more? Schedule a time to speak with our team.
Password Spraying FAQs
What Systems do Password Spraying Target?
Password spraying campaigns usually target single sign-on (SSO) cloud-based applications that utilize federated authentication protocols. Targeting these protocols and platforms makes it easier for hackers to mask malicious traffic. Moreover, taking aim at SSO applications maximizes access to key information and intellectual property if the attack is a success.
What is an IMAP-based Password Spraying Attack?
An attack targeting an Internet Message Access Protocol (IMAP) is designed to avoid multi-factor authentication hurdles. Because IMAP is a legacy internet technology, password spraying hackers are more likely to target IMAP. Many systems that rely solely on IMAP can't enable account lockouts after multiple attempts, making cloud-based accounts easier to compromise.
How Can I Detect Password Spraying Attacks?
An unusually high number of login attempts or accounts locked out at any given time are the most obvious ways to detect a password spraying attack. Increasing the velocity of login attempts - faster than any human could enter manually - is also an easy way to tell that a password spraying attack is underway. Make sure your systems are configured to monitor for these suspicious activities.
Is it Possible to Prevent a Password Spraying Attack?
Yes. Because password spraying targets commonly used passwords, setting organization-wide password guidelines and banning commonly used passwords is an extremely effective prevention measure. You can also consider switching to the sole use of biometric access authentication, completely eliminating passwords from your organization altogether. This renders password spraying all but impossible.
Closing Thoughts
Using common phrases or combinations is akin to simply giving away your passwords to would-be hackers for spraying attacks. That's why it's critical to have the right password policies - as well as threat detection and response technology - to prevent hackers from going after what they perceive as low-hanging fruit. If you're just now finding out about the dangers and prevalence of password spraying, make sure to connect with an experienced cybersecurity partner like Varonis to help get passwords like "abc123" out of your organization for good.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.