The LAPSUS$ cybercrime group made headlines recently after taking credit for high-profile attacks on major companies including Microsoft, Okta, Samsung, Ubisoft, and NVIDIA (confirmed by Microsoft and Okta). This group's goal, like many others, is to steal sensitive data, threaten to leak it, and extort their victims.
U.K. police arrested seven people, between the ages of 16 and 21, as part of an investigation into the LAPSUS$ group.
Methods of operation
Unlike your standard ransomware groups that deploy malicious payloads to mass encrypt and exfiltrate data, the LAPSUS$ group uses simple yet effective social-engineering techniques to infiltrate environments and steal sensitive data.
According to Microsoft:
"Their tactics include phone-based social engineering; SIM-swapping to facilitate account takeover; accessing personal email accounts of employees at target organizations; paying employees, suppliers, or business partners of target organizations for access to credentials and multifactor authentication (MFA) approval; and intruding in the ongoing crisis-communication calls of their targets."
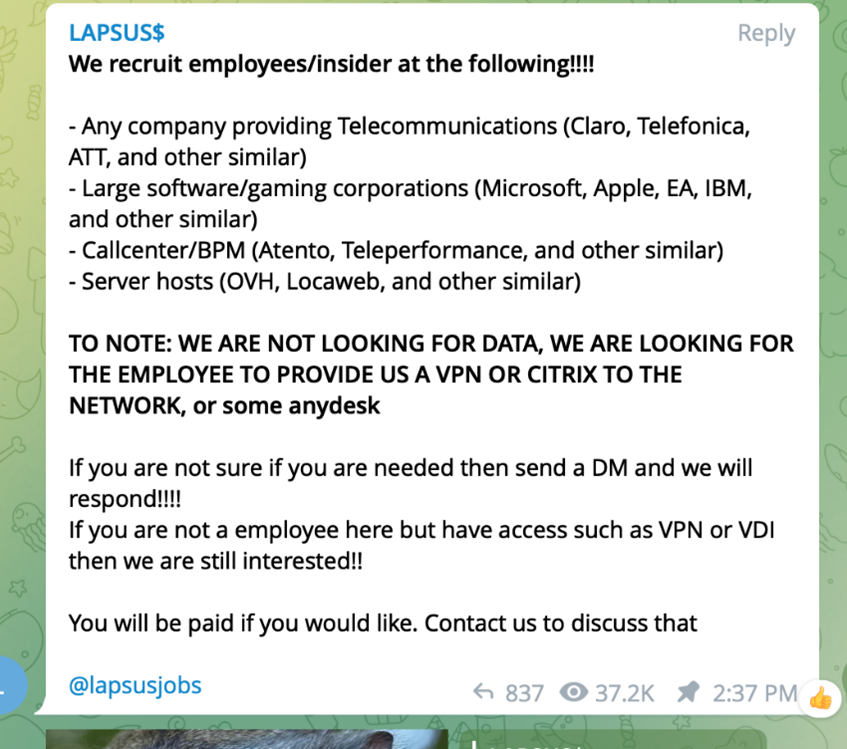
In addition to these social engineering methods, LAPSUS$ employs tools to crawl public code repositories that identify exposed credentials or open RDP ports, as well as "redline" password-stealing software that gets them directly from the user.
Once they steal credentials and bypass MFA, they infiltrate your private network and public SaaS applications to begin searching for sensitive data. As a part of their attack path, they head to private GitHub repositories and collaboration platforms like Google Drive and Microsoft 365 to find additional credentials (preferably privileged users and admins) to escalate their privileges and expand their reach.
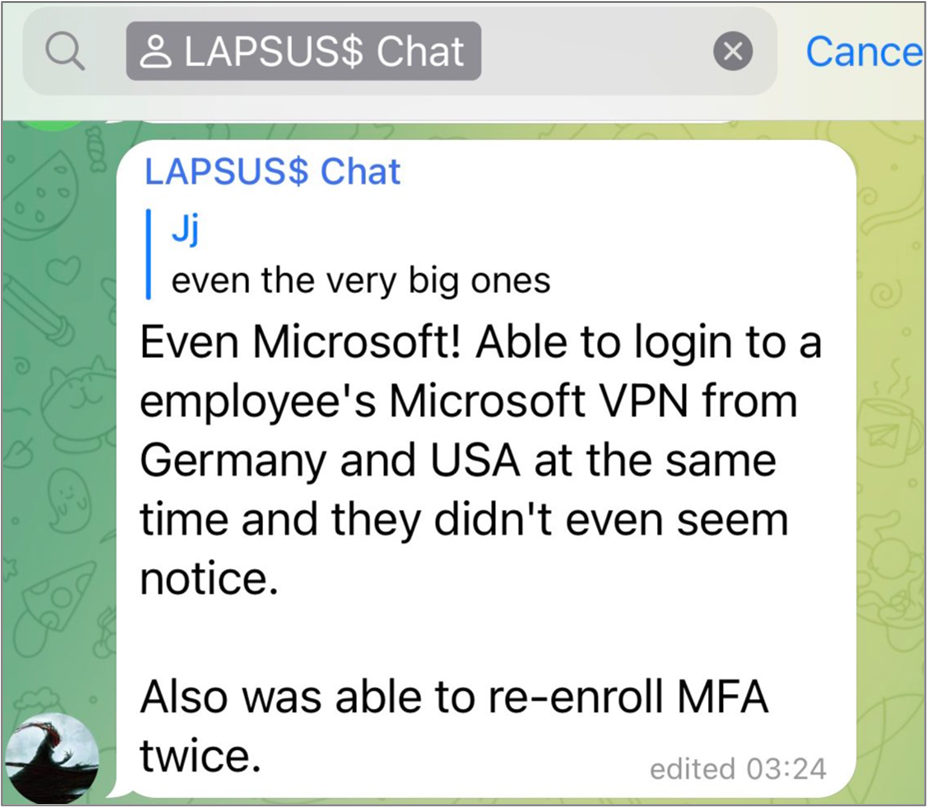 LAPSUS$ publicly touts their Microsoft hack via Telegram.
LAPSUS$ publicly touts their Microsoft hack via Telegram.
Rather than encrypting data before exfiltration, they directly download the data through a VPN or virtual machine. After which, they attempt to destroy the organization’s original copies of the data, leaving no choice but to pay to get their data back or risk the hackers selling or leaking it online.
Intrusion timeline
Security researcher Bill Demirkapi obtained a copy of the Mandiant investigation report with a detailed timeline of the techniques used in a recent LAPSUS$ intrusion.
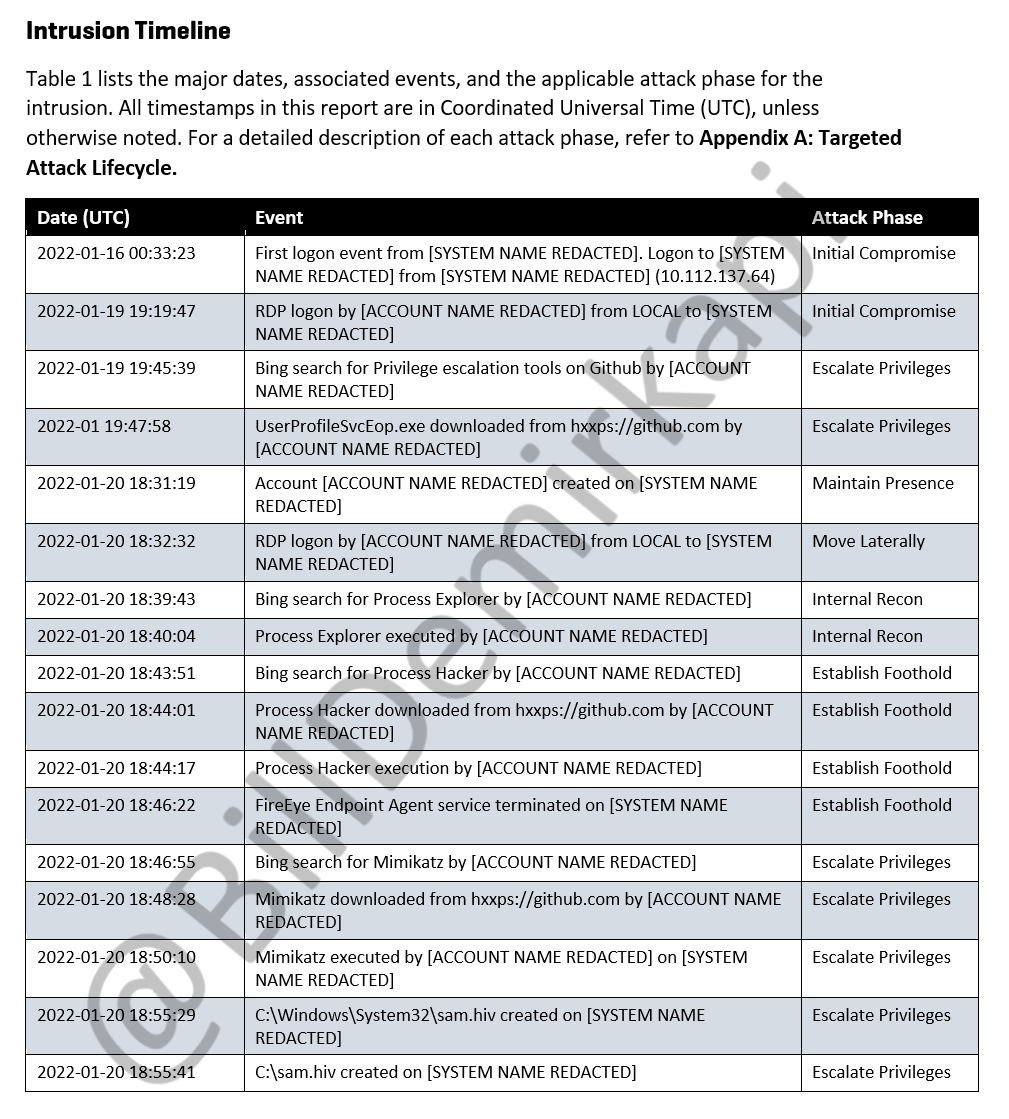 Timeline and methodology used by LAPSUS$ in a recent intrusion. (Source: Bill Demirkapi)
Timeline and methodology used by LAPSUS$ in a recent intrusion. (Source: Bill Demirkapi)
LAPSUS$ showed a lack of OPSEC sophistication post-intrusion—searching Bing and Google from the victim’s machine for off-the-shelf hacking tools and downloading them directly from GitHub.
According to Mandiant’s report, they used ProcessHacker, Process Explorer, and Mimikatz to perform recon, establish a foothold, disable FireEye’s endpoint agent, and escalate privileges.
The attackers compromised a user’s Microsoft 365 account and began searching for sensitive files. They found an Excel file named DomAdmins-LastPass.xlsx in a shared location. The file presumably contained clear-text admin credentials, allowing the attacker to create additional accounts, add the accounts to a group called “tenant administrators,” and setup email auto-forwarding rules to BCC email sent to sykes.com inboxes outside of the organization.
Detecting and mitigating SSO, IAM, and SaaS attacks
LAPSUS$ style threats can be hard, if not impossible to detect with traditional perimeter and endpoint security alone. They spend very little time on the endpoint before pivoting to cloud applications with stolen credentials or cookies.
The defender’s job can be difficult when there aren’t specific hashes, registry keys, and other static IOCs to trigger alerts. We recommend treating LAPSUS$-style attacks like you would treat an insider threat. Assume breach of the perimeter, limit access, and watch for abnormal deviations from baseline behavior.
Right-size access and reduce exposure
The end goal of most cyberattacks is to steal or encrypt valuable data. Knowing who has access to which data and remediating overexposure is key to reducing your blast radius. In the event a single account is compromised, you want to ensure the attacker must get elevated access to do meaningful damage.
Right-sizing access starts with permissions visibility. The low-hanging fruit is to inventory your super admins across your different cloud apps. Depending on the app, determining who has privileged access can be difficult. For example, in Salesforce you can create a custom user profile that mimics an admin account but is named something innocuous like “Sales Users.”
 Varonis identifies all of the privileged entities in your cloud environment
Varonis identifies all of the privileged entities in your cloud environment
You should have policies setup to alert you when a user is added to a privilege group or given super admin privileges. In most organizations, this action should be extremely rare, so the alerts have high fidelity.
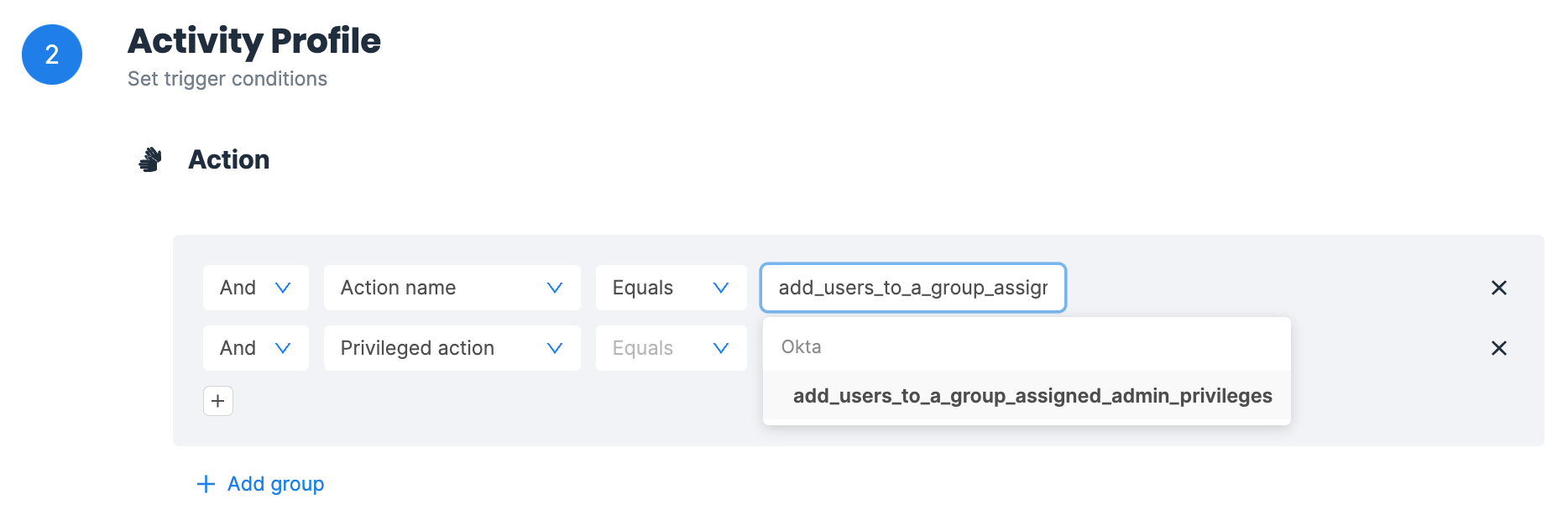 Varonis alert triggered when new admin privileges are granted in Okta.
Varonis alert triggered when new admin privileges are granted in Okta.
Another way to drastically reduce risk is to proactively identify where sensitive data is exposed publicly, to guest users (like contractors), or to all users in your organization. Limiting sensitive data that is accessible to large swaths of users will make it more difficult for groups like LAPSUS$--who often use credentials found in publicly exposed GitHub repositories or pay contractors for access--to find data worth stealing.
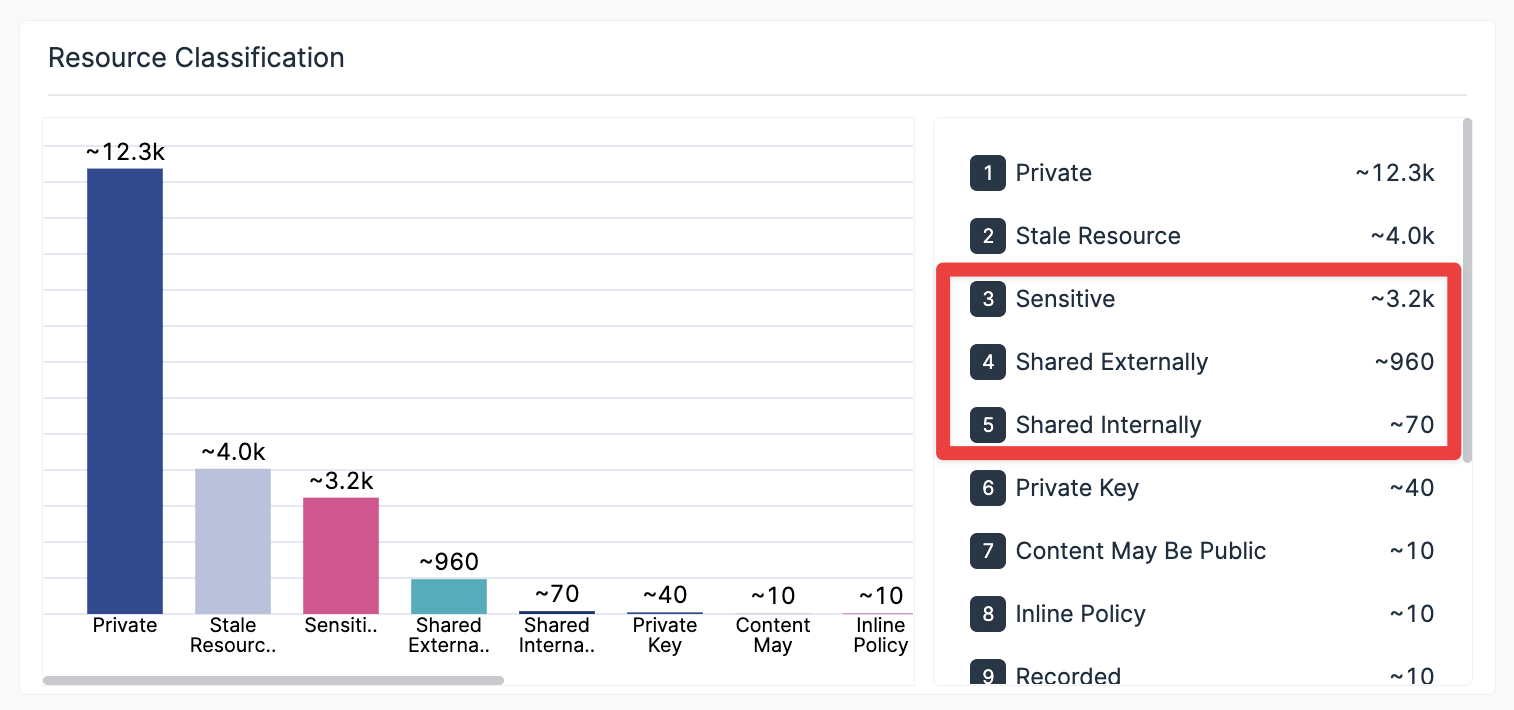 Varonis classifies sensitive data and shows you how much of it is exposed externally or internally.
Varonis classifies sensitive data and shows you how much of it is exposed externally or internally.
When you can pinpoint a user’s entitlements quickly across multiple SaaS apps and data stores, answering “What could this person possibly have accessed?” can make investigation, response, and disclosure faster and more conclusive.
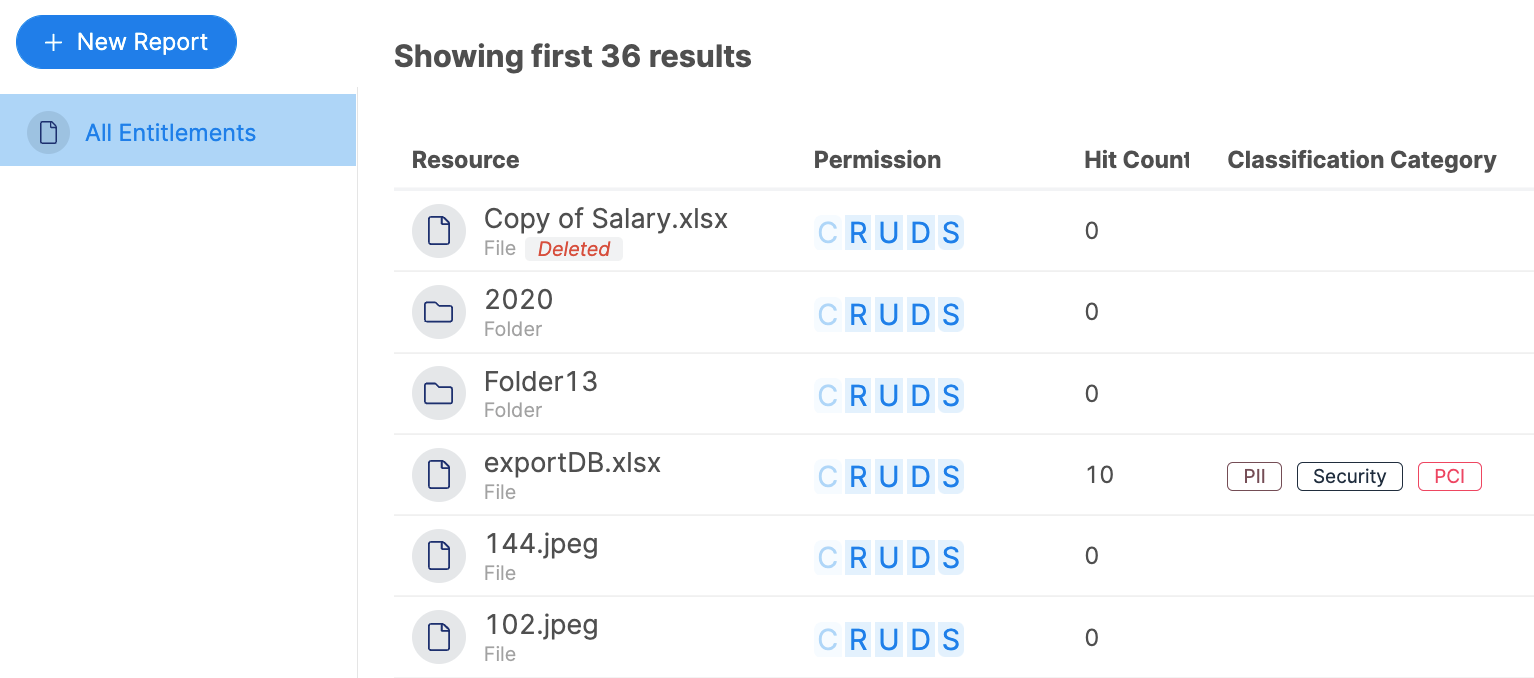 A cross-cloud map of what a particular user of interest has access to and whether it is sensitive.
A cross-cloud map of what a particular user of interest has access to and whether it is sensitive.
On multiple occasions, LAPSUS$ gained access to an employee’s virtual desktop where the user was already logged into multiple SaaS applications like GitHub and Jira. Since a person can be represented by multiple user accounts in a multi-cloud environment, it’s essential to be able to link these identities automatically so you can assess the potential access and easily aggregate the log events from that person.
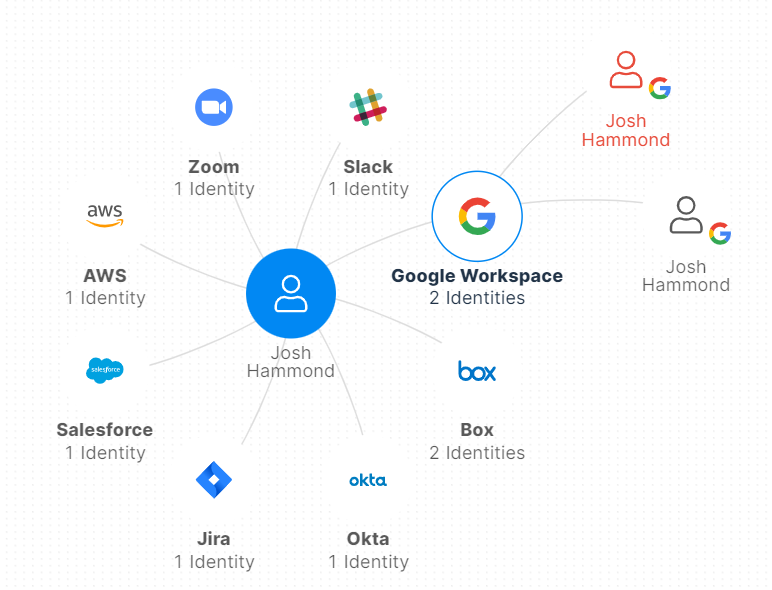 Varonis automatically links identities across your cloud apps.
Varonis automatically links identities across your cloud apps.
Monitor user behavior across different apps and systems
Monitoring endpoints and identifying potential perimeter breaches is a must for any organization, but what happens when attackers bypass your endpoints altogether?
Analyzing user behavior and data activity is one of the best ways to identify a threat actor impersonating one of your users and stop them before it's too late.
Even if a group like LAPSUS$ performs significant research and reconnaissance on the user they’ve compromised, they still cannot perfectly mimic their behavior, especially as they move through your environments accessing and downloading large amounts of data.
It's essential to baseline behavior across all your users and all your critical apps and data:
- Profile which files/folders they typically use across M365, Box, Google, etc.
- Profile which websites/apps they connect to (Slack, Zoom) and what they typically do inside them
- Profile the devices/IPs/geos they use to connect to the VPN/cloud apps
- Profile AD/IdP/IAM activity--logins, permissions changes, password resets
Once you have rich peace-time profiles, sophisticated machine learning algorithms can detect even subtle deviations that could indicate compromised or malicious insiders.
LAPSUS$ is a prime example – they may have your credentials, phone number, recovery email, and IP address, but they still can't be you. As they move through the environment, they're searching, opening, and downloading data in patterns that don’t match yours.
Varonis monitors user and data activity to alert on any suspicious or abnormal behavior that occurs across your sanctioned cloud applications. Using proprietary threat models and policies, you will receive detailed alerts on suspicious activity detected in your environment that may be putting your organization at risk.
These alerts include activities such as:
- When a user accesses or downloads an abnormal amount of sensitive data
- When sensitive data is shared publicly
- If a user logs in from an unusual or blacklisted country.
- If MFA has been disabled
- Excessive password/MFA reset requests
- If a contractor or stale account becomes active after a long period of inactivity
These are just a few of our many alerts generated by our threat models which we are constantly (and automatically) updating and evolving based on research from Varonis Threat Labs.
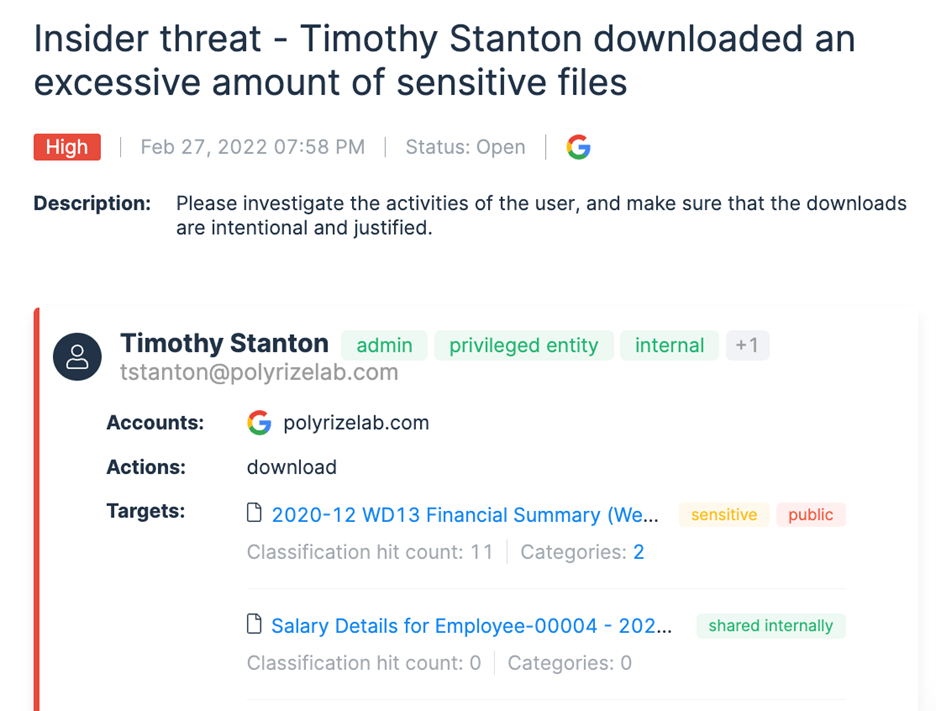 Varonis alert triggered when user Timothy Stanton starts meaningfully deviating from his typical data access patterns.
Varonis alert triggered when user Timothy Stanton starts meaningfully deviating from his typical data access patterns.
Identify org-wide misconfigurations and protect admin accounts
While attackers are after your data, they are also looking to identify which accounts will give them the widest access to sensitive data and organization-wide misconfigurations or weak configurations that they can exploit.
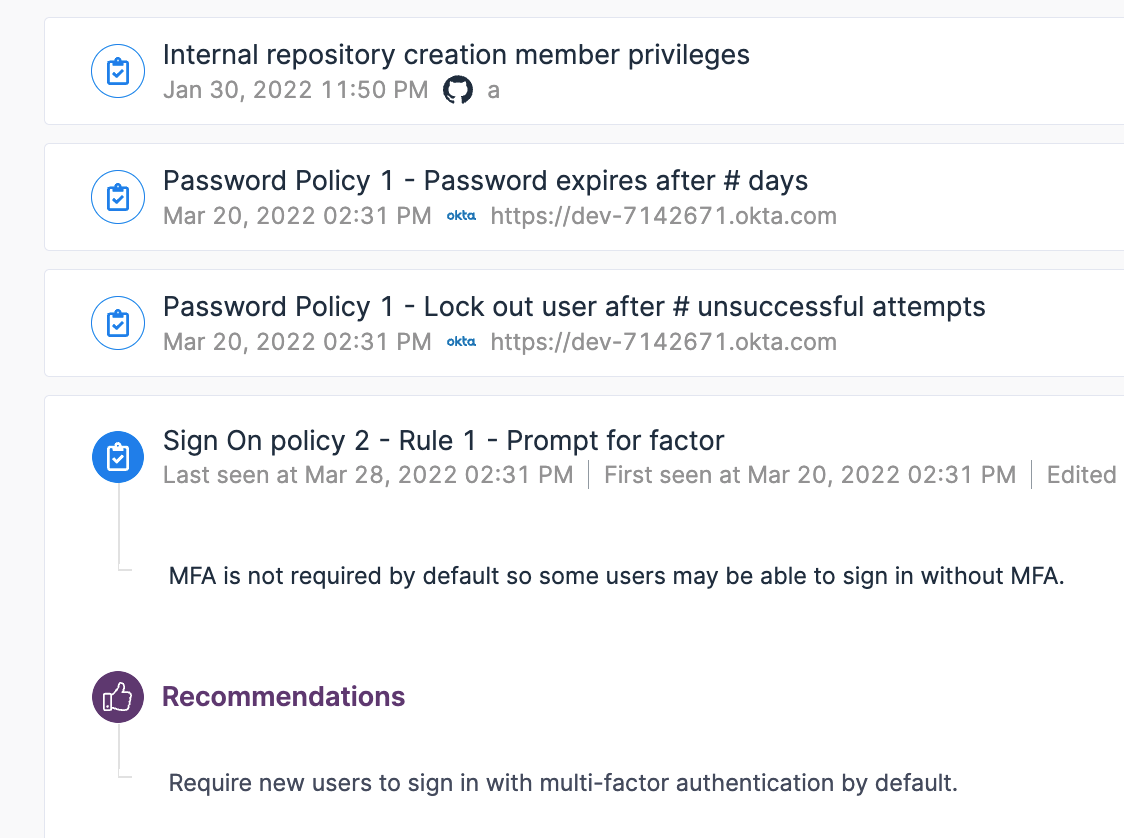 Varonis Insights feature scans your SaaS apps and highlights misconfigurations or out-of-policy configurations.
Varonis Insights feature scans your SaaS apps and highlights misconfigurations or out-of-policy configurations.
Hackers will target your privileged and admin accounts as they not only have access to more data but also have the rights to change configurations within the cloud platform that will make it easier to steal sensitive data without being caught.
Ensuring that you configure admin accounts correctly and constantly monitor their activity is vital. Suppose you spot an admin performing suspicious actions, like changing SSO settings, removing the need for MFA, changing passwords, granting increased access to other accounts, or other risky privileged activity without the knowledge of others. In that case, that may be a sign of a threat.
It is also considered best practice to have your admins only use their privileged accounts to perform administrative task and use a different unprivileged users for daily actions such as accessing their files. This will help reduce the severity of an attack in a case where an admin account is breached.
Cross-cloud monitoring
Lateral movement has evolved in the cloud to include hopping from one cloud service to the next to maximize the impact of attacks. Threat actors often use credentials found in one cloud application to gain access to another—as seen with LAPSUS$—so it is critical to monitor all your cloud data stores and track how your users move across them so you can spot this type of lateral movement.
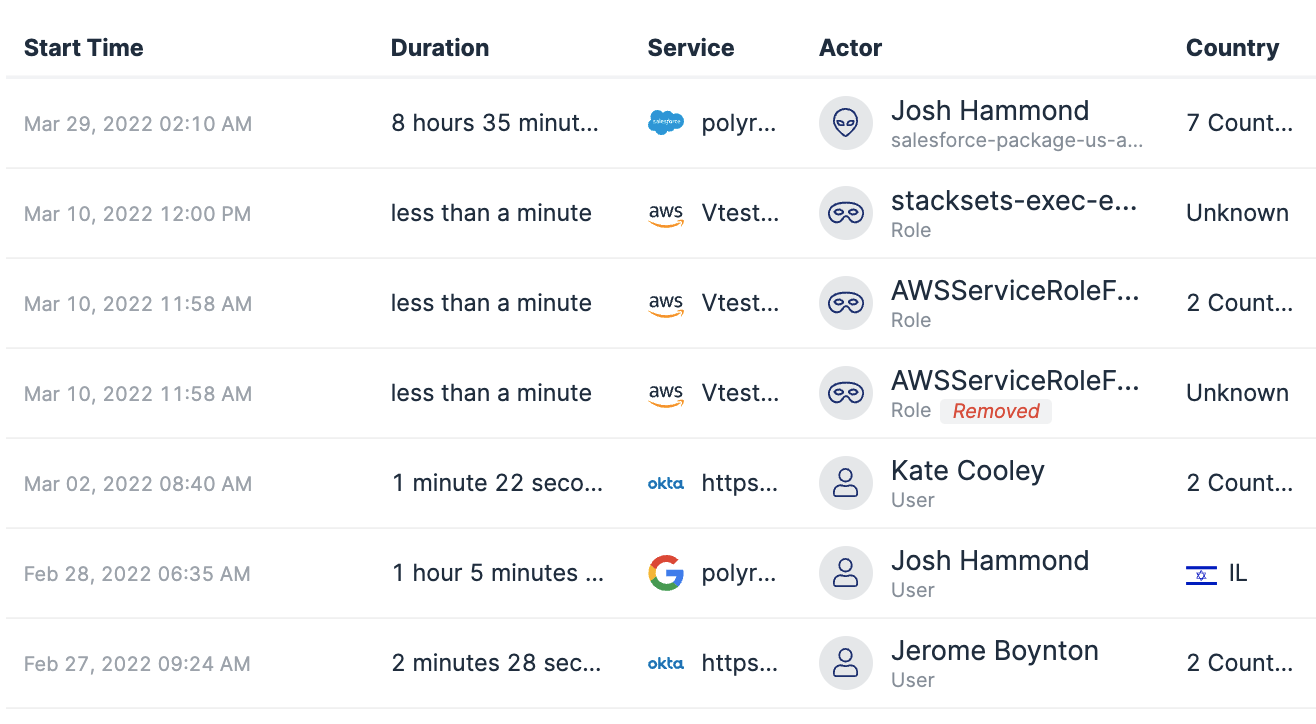 Forensics log in Varonis to investigate activity performed by users across different SaaS apps.
Forensics log in Varonis to investigate activity performed by users across different SaaS apps.
Takeaways
LAPSUS$ has shown us that it’s never been easier for novice threat actors to do significant damage in a short period of time. As cybercrime becomes more lucrative, technical talent will continue to be drawn into the dark side and insiders will be tempted to sell their access. For defenders, it’s absolutely critical to evaluate your cloud visibility and behavior-based detections—two things that have proven to be necessary to detect and prevent LAPSUS$-style intrusions and data exfiltration.
If you wait for a breach to occur, it's too late. Strengthen your cloud security today and stay ahead of emerging threats with Varonis. Learn more about our comprehensive cloud security solutions and take advantage of our free Data Risk Assessment to help you safeguard your digital assets.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








