Salesforce holds a wealth of customer data — and Salesforce audits are becoming a priority for organizations that want to ensure that information is kept secure and within the guardrails of privacy law.
Audits are serious business, so you'll need a game plan. In this post, I'll walk you through what a Salesforce audit is, how permissions work, and provide tips on how you can prepare.
Discover your weak points and strengthen your resilience: Run a Free Ransomware Readiness Test
What's the purpose of a Salesforce permissions audit?
A Salesforce audit allows internal and independent auditors to gain a comprehensive view of an organization's Salesforce instance for security and compliance purposes.
If auditors conduct a Salesforce permissions audit, it's usually part of a larger ongoing project to ensure that proper governance and security policies are in place to safeguard critical consumer and financial information. Audits could also be part of mandatory reporting requirements under GDPR, HIPAA, PCI-DSS, and SOX regulations.
Salesforce permissions: an overview
Salesforce provides a robust data-sharing model that lets you control two primary aspects:
- Which users get to see what data within your Salesforce instance
- How users can interact with the data they can access
To help illustrate Salesforce permissions within this data-sharing model, picture a three-pronged approach comprised of profiles, permissions, and permission sets.
Profiles
Profiles help you define what a Salesforce user can do. When you create a Salesforce user, you also assign a profile to that user that provides a packaged set of access settings and permissions. Depending on your Salesforce edition, several standard profiles may be available out of the box, or you can create custom profiles based on your requirements.
Each Salesforce user can have only one profile. Profiles typically set permissions to users based on their primary job function, for example, marketing or sales.
Permissions
Permissions determine what a user can view and edit in your Salesforce instance. Each user profile has one or more permissions that regulate what information the user can access and what they're allowed to do (create, read, update, delete, etc.). You can set up permissions for standard Salesforce apps and custom apps.
Maintaining these permissions for every profile and scenario in Salesforce could become cumbersome, so permission sets come in handy.
Permission sets
Because each user can only be assigned one profile, Salesforce provides permission sets that can extend a user's access without changing their profile. Salesforce provides various permission sets out of the box, or you can create your own by cloning a standard set.
To give users access to data, Salesforce recommends using a combination of profiles and permission sets. Start by providing users with the bare minimum permissions to do their jobs. Then, extend the user's access as needed, using one or more permission sets.
For example, suppose a user needs to access managed password policies, but that permission is not enabled in their profile — but access is available in a permission set. If the user has this permission set assigned to their profile, they will still be able to manage password policies.
This table provides examples of the types of permissions and access settings available and where they can be enabled. For a more comprehensive guide on protecting your data at various levels within your Salesforce org, read this Guide to Salesforce Data Protection. 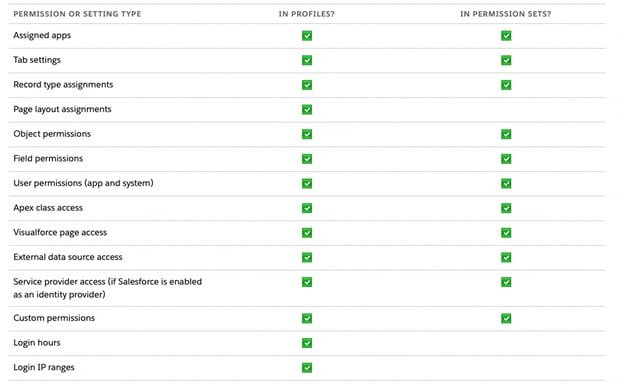
Now let's look at what happens during a typical Salesforce audit and determine how you can prepare.
Elements of a Salesforce audit
1. Custom object and Apex development audit
Salesforce audits can require additional time if your organization has done a lot of custom development. If you created many custom objects and devoted a significant amount of effort to tweaking workflows, approvals, or page layouts, these customizations could be heavily scrutinized. The amount of detail uncovered will increase if you use a lot of Apex-based triggers and validation rules. Combine these with custom reports, and you might be spending a lot of time explaining and justifying these adjustments in your audit.
2. Metadata and configuration data tracking audit
Every audit team will go through the recorded history of all the changes in your Salesforce instance. Salesforce lets you view audit trails at multiple levels, from login history to admin setup changes, to tracking field history for standard and custom objects. The field audit features work behind the scenes with metadata API to define the retention policies for multiple reporting requirements.
Salesforce also lets you configure a setup audit trail for changes made at the administrator level during the past 180 days in profiles, permission sets, and development.
3. Security model audit
Auditors could spend considerable time reviewing how you've set up your profiles and permission sets to understand what data users can view and edit. Auditors typically compile a permissions report comparing profiles and permission sets within your instance to determine what each Salesforce user can access.
Auditors compile this information by exporting all profile and permission set data, including querying the data and the metadata API. Be prepared to spend time working with the audit team to produce artifacts related to the profiles, permissions, and permission sets within your Salesforce instance.
Preparing for a Salesforce audit
Depending on the level of custom development in your Salesforce instance, the mere mention of a Salesforce audit could be concerning. The following steps can help you prepare for an upcoming audit.
Keep the principle of least privilege in mind
The principle of least privilege requires that a user (or process) access only the minimum information and resources needed to do their job. In Salesforce, the least-privilege approach mandates companies ensure a particular user can access records only when necessary, under specific conditions, to reduce risk from overexposure.
To get started on the road to least privilege:
- Block all pathways to data as needed for APIs, Salesloft Community, and third-party apps, and only open pathways selectively for specific profiles and permission sets.
- Use a combination of session-based permission sets and additional controls on the record level to tighten up security for internal user requirements.
Tidy profiles with permission sets
Profile settings can restrict usability, so combining profiles with multiple permission sets may be necessary. Companies should maintain as few permission sets as possible within their instances. As your instance grows, it's easy to lose track of why permission sets were created in the first place. Continuously monitor your permission sets and clean up unused profiles and sets in your instance to reduce access and close gaps.
Use permission set groups wisely
Permission set groups bundle permission sets based on a shared job function. For example, your marketing team could conduct different activities, including reporting, lead management, and campaign execution. Each activity might have its own permission set, but this permission set group can be assigned to marketing users in your org so they can run all these activities.
To save time in the long run, make sure you genuinely need to build any new permission set groups and trim existing ones down to a manageable list.
Conduct an access control self-assessment
Best practices dictate periodic self-assessments of your entire security model setup. Salesforce provides a security baseline assessment, Health Check. This baseline is not restricted to permissions only but applies to your overall setup across org-wide policies. Suppose you are only looking to analyze your permissions configuration. In that case, this assessment may be broader than needed. Still, it's wise to use the standard baseline in your Salesforce instance from time to time to dive deeper and button-up possible channels that could make you vulnerable.
As your organization grows and regulations change, it can be challenging to prepare for audits. Continue to assess your permission sets and profiles periodically. Once you do, you'll be ready to pass every audit with flying colors.
👋When it comes to protecting your sensitive data, knowing where it exists, who can access it, and what they’re doing with it are all critical questions to answer. Only Varonis is integrating all these critical data security capabilities into one platform.
If you’re curious to see what risks may exist in your SaaS environment, reach out to start a trial. In minutes, we can have you up and running.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.