The ESP8266 microcontroller is a cheap, powerful IoT module with embedded Wi-Fi, which can be programmed in a number of popular languages. On the Security Tools podcast, we explore some of Stefan Kremser’s popular Wi-Fi hacking tools based on the ESP8266.
Download the full Netcat cheatsheet
What is the ESP8266
If you’ve ever bought an off-brand smart light bulb, power switch, or IoT camera, you probably already have an ESP8266 microcontroller. A Chinese semiconductor company called Espressif created the ESP8266 to be an affordable platform for easily making Wi-Fi connected smart products. The tiny microcontrollers have surprising functionality in a durable and inexpensive package, becoming even more popular after hackers ported the beginner-friendly Arduino IDE language to the ESP8266.
Easily prototyping Wi-Fi security tools was made possible by the creation of development boards featuring an esp8266 microcontroller mounted on a printed circuit board with a USB interface for easy programming. These include the NodeMCU and the D1 mini, arguably the most popular ESP8266 development boards. These boards are easy for beginners to work with using popular languages like Arduino, MicroPython, and Lua.
How to Program the ESP8266
Microcontrollers like the ESP8266 lack many of the features found on full-fledged computers like the Raspberry Pi. The biggest difference is that a microcontroller has no operating system. Instead, we need to program what we want the microcontroller to do and then upload it to run in a loop.
You don’t have to be a programmer to use it – you can load and try out tools other people have written without understanding how the programming behind it works.
To get started, download the Arduino IDE, add the ESP8266 to the list of boards, and connect the ESP8266 board via USB. Next, select the development board you’re using and flash the code you downloaded to it, for example, Stefan Kremser’s Wi-Fi deauther.
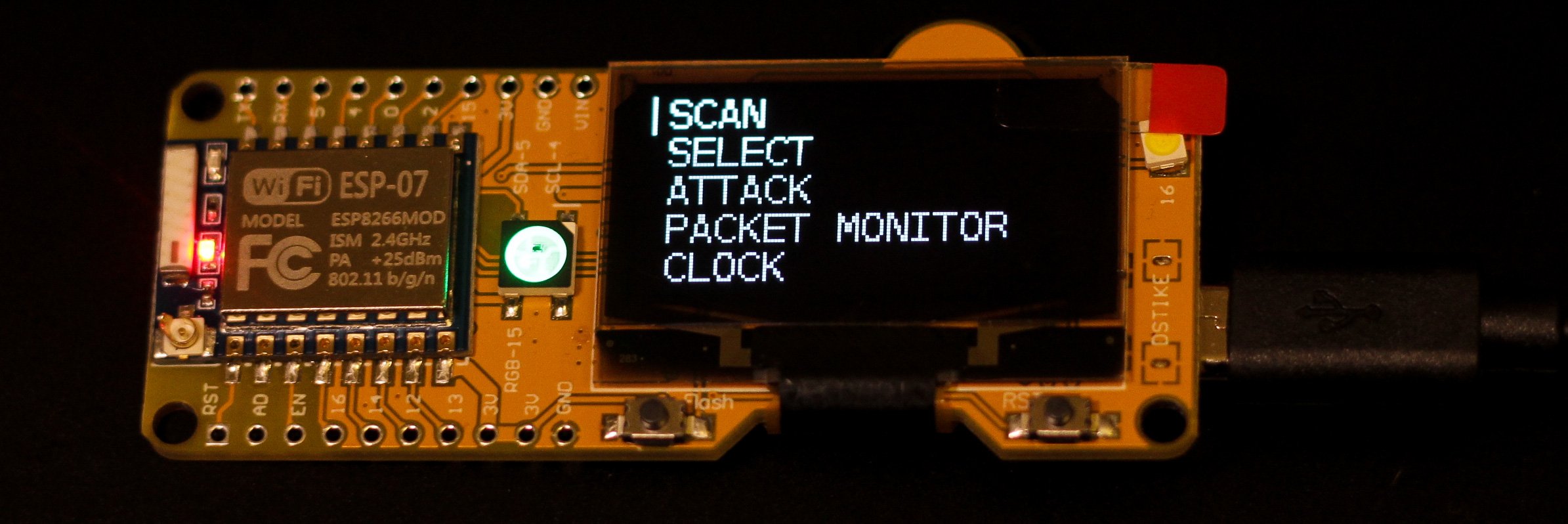
ESP8266 De-Authentication attacks
One of the most powerful abilities of the ESP8266 is to write nearly any type of Wi-Fi packet from scratch. Stefan Kremser used this tactic to build a series of security tools that take advantage of serious flaws in the WPA2 Wi-Fi standard.
Wi-Fi routers can send a message called a de-authentication packet to any connected device to terminate the current Wi-Fi connection. Similarly, a disassociation packet tells a device to disconnect when it leaves the coverage area of the WI-FI network. Stefan’s Wi-Fi Deauther uses the ESP8266 to fake these messages, which can disable any targeted device within range from connecting to Wi-Fi.
Hackers can use the Deauther to control Wi-Fi attacks from a slick mobile-friendly web interface baked into the design. If a hacker wants to gather WPA handshakes to try bruteforcing the Wi-Fi network password, the Wi-Fi Deauther can generate a handshake to capture from any WPA2 network with clients connected.
When de-authentication and disassociation packets are sent continuously, Wi-Fi devices like laptops and IoT security cameras will stop being able to connect at all. This is effectively a protocol based jamming attack, but unlike jamming attacks that rely on raw signal strength to overpower a connection, the ESP8266 is simply a valid (although spoofed) packet that happens to cause any nearby Wi-Fi link to be repeatedly disrupted. The upcoming WPA3 standard fixes this by making de-authentication packets impossible to spoof, but until the new standard is in widespread use, most networks remain vulnerable to this flaw.
Packet Sniffing
In addition to broadcasting over Wi-Fi, the ESP8266 can also listen. Stefan’s Arduino PCAP library can read basic information about nearby networks with Wireshark by using the ESP as a network adapter. While the ability to sniff packets isn’t perfect, Stefan was still able to use the more limited packet data made available to create a number of useful sniffing tools.
You can use the packet sniffer and The Deauth Detector to warn you if a de-authentication attack is underway by sniffing for a suspicious amount of de-authentication packets. If someone starts using a tool like the Deauther against a device on your network, the Deauth detector would detect the flood of spoofed packets and alert you that your network was being targeted.
The ESP8266 can also be used to monitor all packets flowing around you with the Wi-Fi Packet Monitor. This tool can monitor the number of access points and devices transmitting on every channel, as well as the number and type of packets being sent.
One thing the ESP8266 can’t do is capture the 4-way WPA2 handshake we need to crack a Wi-Fi password. The packet data the ESP8266 accesses is truncated and doesn’t contain the information we would need to mount a cracking attempt with tools like Aircrack-ng. We can, however, still learn about the manufacturer of a router and any devices using Wi-Fi nearby, including information about the types of packets being sent.
Beacon Spoofing
Stefan programmed the ESP8266 to spoof a beacon packet, which is the type of packet used by a Wi-Fi access point to announce its name and basic information to anyone in range. These packets are what cause a device to list a network in the “nearby networks” list that is displayed when you’re looking for a network to join. By spoofing these beacon packets, the ESP8266 can fake the appearance of any network to any devices in range.
Stefan’s tool, called the Beacon Spammer, can easily create up to a thousand fake networks at the same time, allowing you to define which network names it should create. A hacker adding the most common open Wi-Fi network names to this list and activating the Beacon Spammer would cause nearby smart devices to stop using MAC address randomization while trying to connect to the familiar-looking fake networks.
This means two things. The first is that the ESP8266 can cause nearby devices to stop using privacy-protecting randomized MAC addresses, which makes them vulnerable to tracking. The second is that the ESP8266 can identify which network names are most likely to allow an attacker to take over a device’s data connection by trying out many possibilities and waiting for a reaction from the targeted device.
Small Package, Big Potential
For such a small and low-cost device, it’s pretty remarkable that this microcontroller can probe nearby devices for the networks they will automatically connect to, deny a device from connecting to a network at all, or even detect a Wi-Fi attack in progress. These abilities continue to make the ESP8266 an exciting platform for hackers to push what Stefan has created even further, developing tools that redefine how cheap an attack can be.
Whether you want to detect hackers targeting your network with the Deauth Detector or start hacking networks yourself with the Deauther, a D1 Mini or NodeMCU development board based on the ESP8266 can get you started for far less than even the cheapest Raspberry Pi.
Stefan has turned this microcontroller into a series of both offensive and defensive hacking tools for anyone interested in exploring the problems lurking in everyday Wi-Fi security. Before you pick one up, you should be aware that they are not compatible with 5 GHz Wi-Fi devices and always remember that targeting devices you don’t have permission to test is illegal and considered a denial of service attack, which can get you in trouble.
If you want to follow Stefan’s projects creating hacking tools with the ESP8266 and Arduino, you can check out his work or pick up one of his custom boards on his website, Spacehuhn.com.
Live session on May 14
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.




-1.png)



