For most organizations, right-sizing permissions is challenging.
Users frequently join, leave, and change roles, and new data sets are continually created and require new permissions. This creates a tangled web of access that IT and security teams struggle to manage. Native tools, like Active Directory, lack the context and control needed to enforce least privilege, leaving organizations exposed to risk and compliance gaps.
With Varonis, data owners are empowered to make informed decisions about who should have access to their data and for how long without needing IT involvement.
Varonis simplifies entitlement management and reduces IT burden by offering end-users an intuitive web interface to request access to data, applications, and security groups directly from data owners. It empowers data owners by allowing them to control access to their data, automate entitlement reviews, support just-in-time access, and enforce the principle of least privilege.
Read more to learn how Varonis can streamline entitlement management for your organization.
Self-service access requests
Varonis enables end-users to easily send access requests to a wide range of assets — from SharePoint Online sites and Active Directory groups to on-prem file shares — directly to the data owner, all from an intuitive web UI. This self-service approach reduces the burden on IT teams and speeds up the access approval process. Data owners can set start and end dates for access to enforce just-in-time access controls, ensuring that access is granted only for the necessary duration.
Enable end-users to easily request access to data and groups.
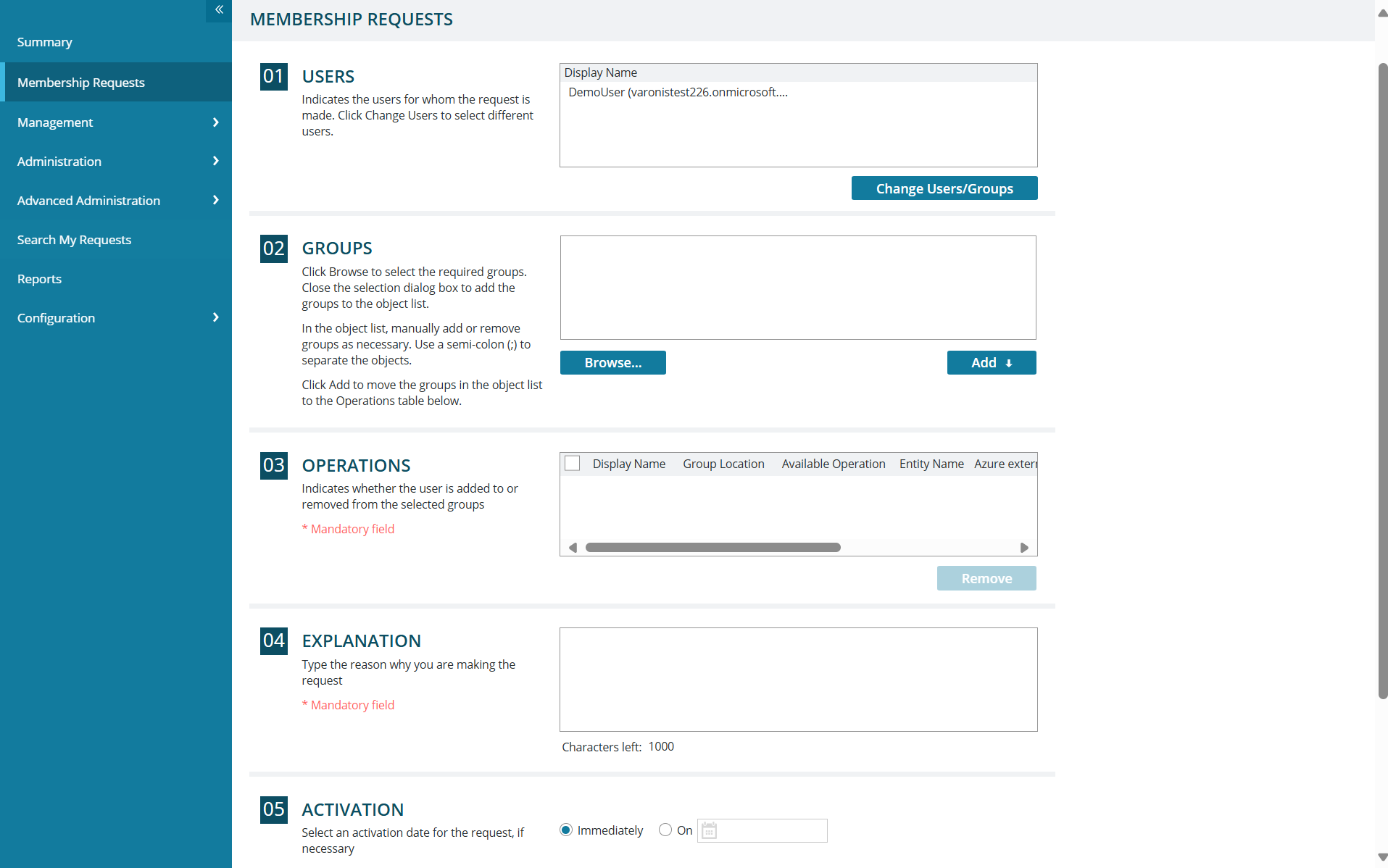
Enable end-users to easily request access to data and groups.
Empower data owners
Who understands data better than the people who own it? IT and security teams are often tasked with managing data access, yet they frequently lack the operational context needed to make informed decisions about who truly needs access.
To compensate, they typically rely on role-based access control (RBAC), which assigns permissions based on static job roles.
However, in today’s dynamic, cross-functional environments, RBAC alone often falls short. It doesn’t account for the fluid nature of project teams, evolving responsibilities, or ad hoc collaborations that don’t align neatly with predefined roles. This mismatch can lead to both over-permissioning and unnecessary access barriers, undermining both security and productivity.
Effectively determining data access requires visibility into the specific tasks, projects, or data needs of individual users.
Varonis enables administrators to identify and assign data owners and trusted approvers. These individuals, who are closest to the data, can grant or deny access directly from Varonis’ UI or even from their email, ensuring a seamless and efficient workflow.
Streamline access reviews with context
Varonis helps data owners make informed decisions on who should have access by presenting them with the classification and sensitivity of the data they are granting access to, as well as the user's domain, department, and affiliation. This comprehensive view allows data owners to assess potential risks and make decisions that align with organizational policies and security standards.
Make informed decisions on access with details on the user and data.
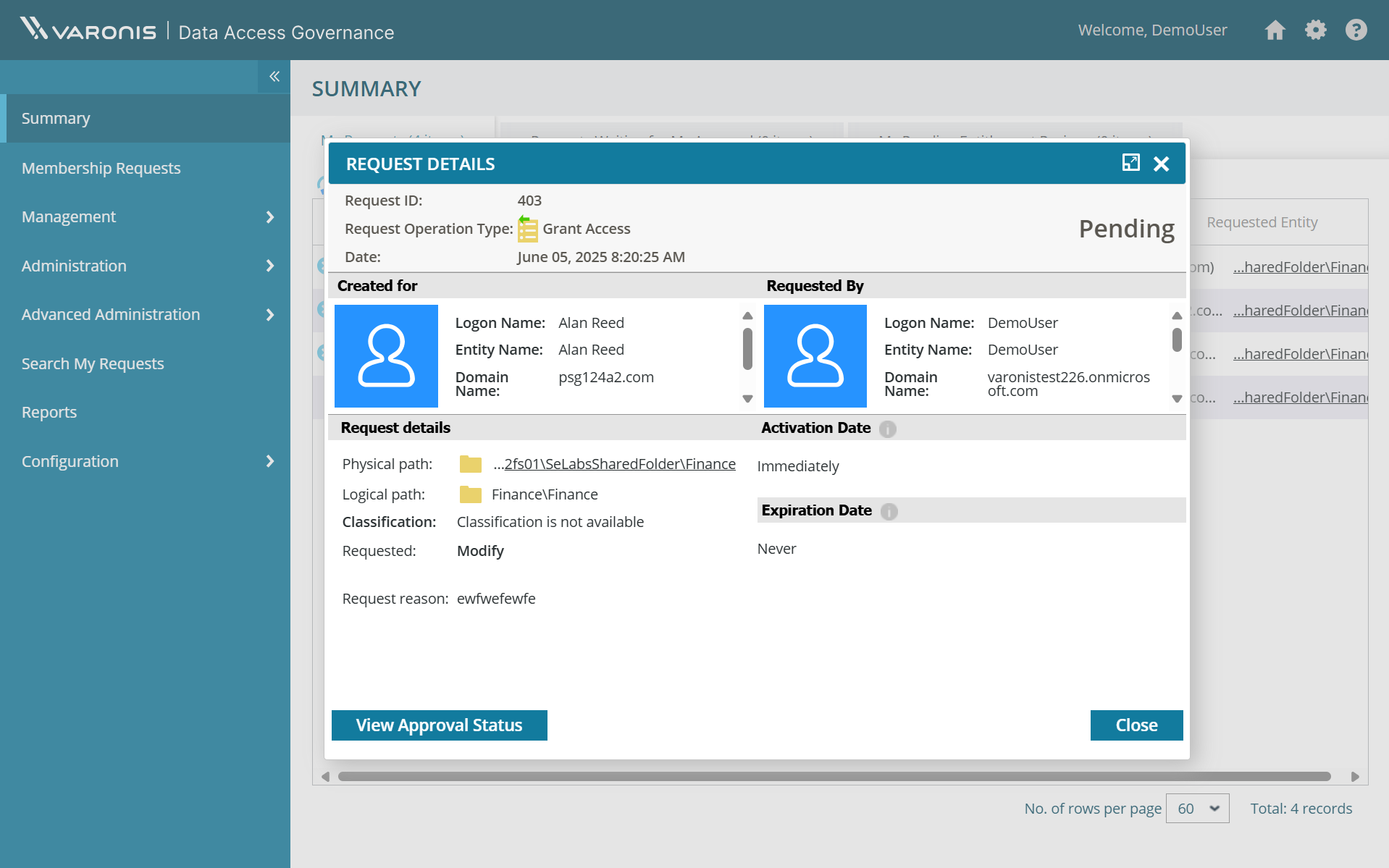
Make informed decisions on access with details on the user and data.
When a request is made, data owners are prompted to review the requests via UI or email and given the full breadth of Varonis context on the requested data and the user. Regular access reviews help maintain a secure environment by continuously monitoring and adjusting entitlements.
Schedule regular access reviews based on organizational policies.
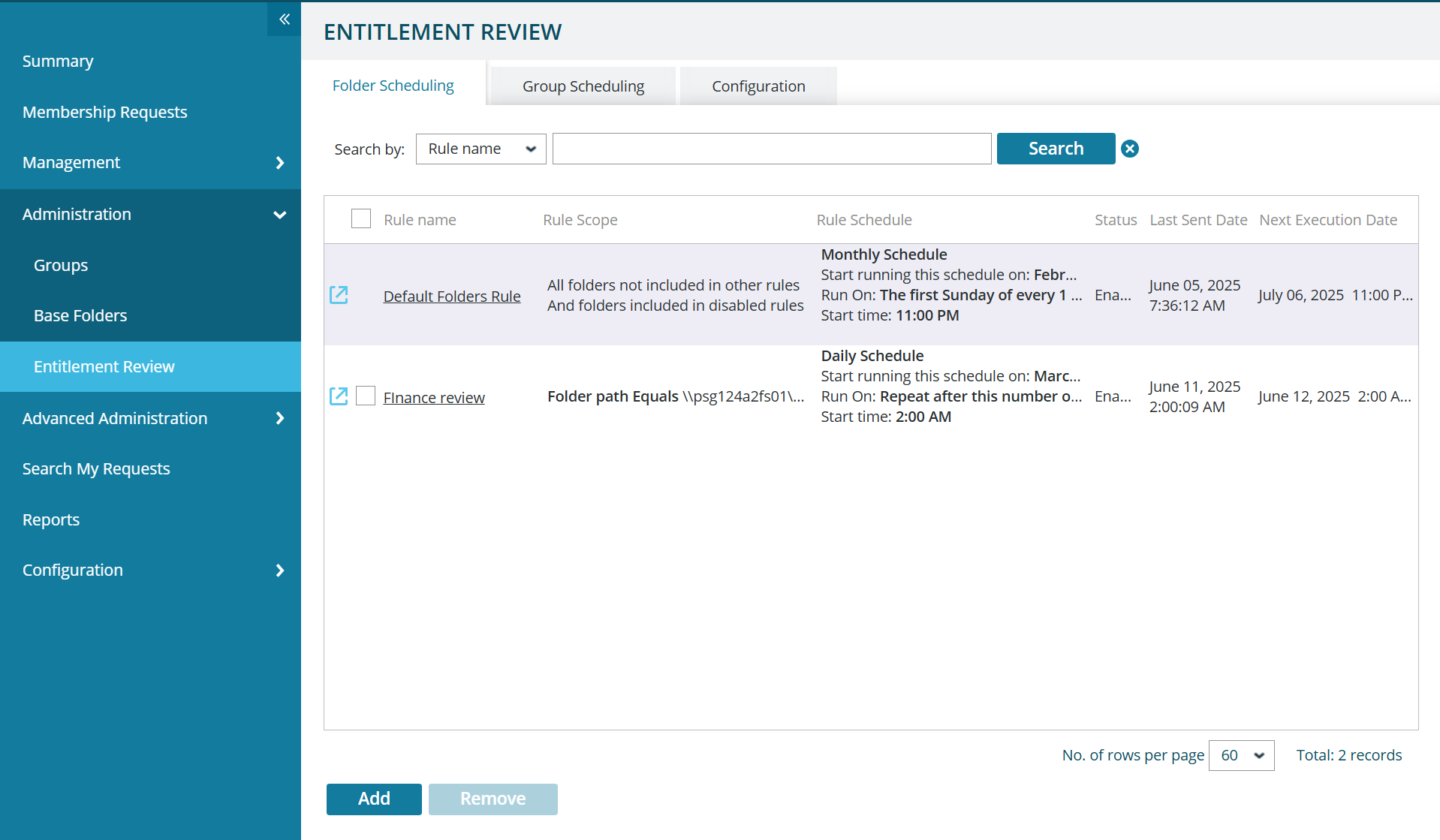
Schedule regular access reviews based on organizational policies.
Automate access authorization
With constant organizational changes, IT, security, and data owners struggle to keep up with who needs access to what. To address this, admins can use Varonis to create automated authorization rules that will grant or revoke access to data and groups based on different attributes such as domain, department, location, email, or even a specific name or user.
These rules streamline the access management process and ensure policy-driven access control without manual intervention. For example, you can configure Varonis to automatically grant users in the finance group access to the finance folder and the SharePoint Site.
Streamline data access governance with automated authorization rules.
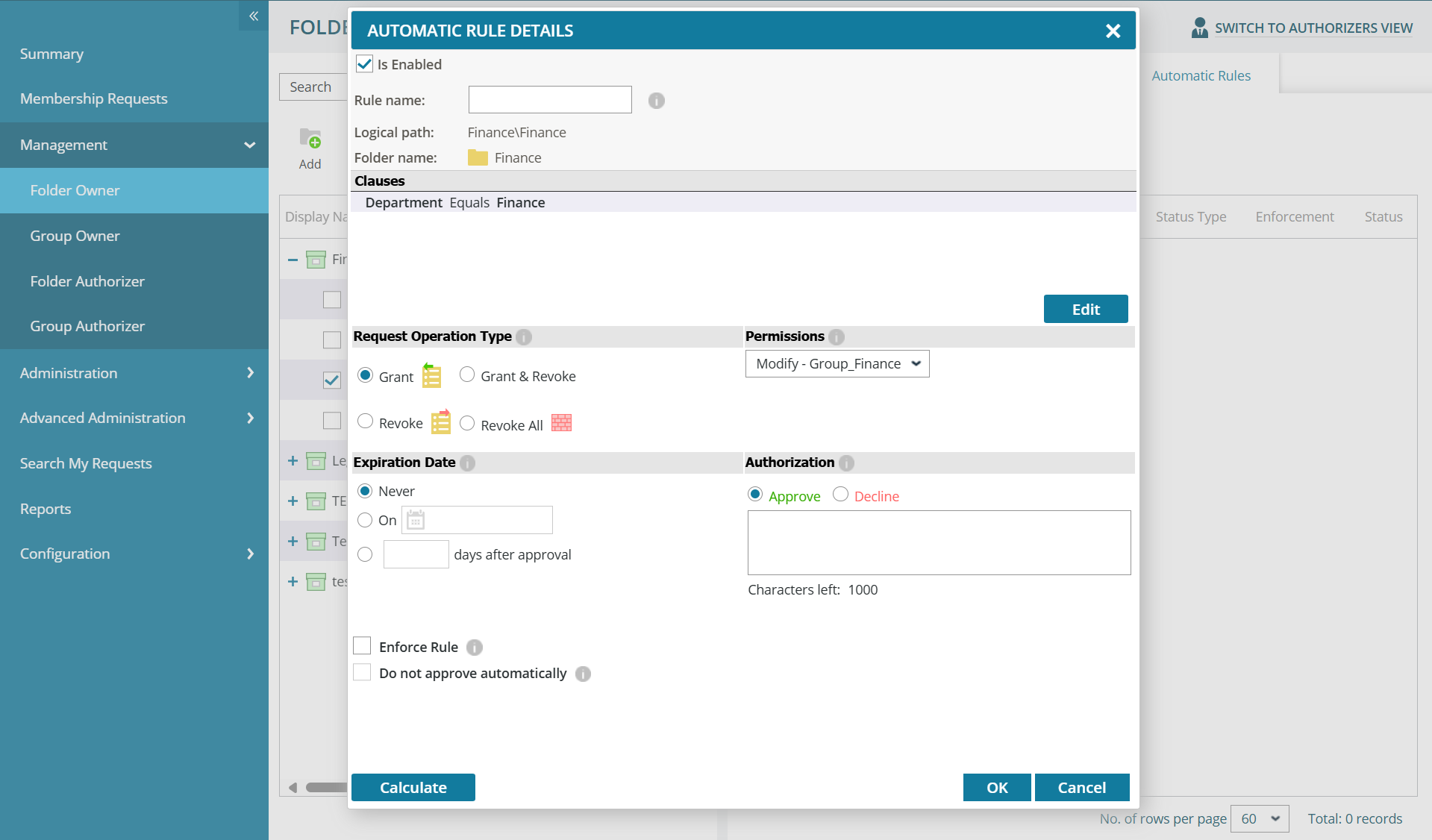
Streamline data access governance with automated authorization rules.
Comprehensive data security
Self-service access requests and automated entitlement reviews are just one part of Varonis' broader data access governance controls, which allow organizations to manage entitlements to data and automatically remediate exposure risks at scale.
Varonis can automatically remove sharing links, quarantine data, and remove stale permissions, drastically reducing your blast radius with minimal effort from you. By integrating access governance with data security, Varonis ensures that sensitive information is protected from unauthorized access and potential breaches.
Ready to empower your data owners and take control of your data? Request a demo to see how Varonis can streamline your data access governance, enforce security policies, and protect sensitive information.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.

.png)







