The Department of Defense (DoD) handles some of the most sensitive and mission-critical data in the world, including classified information, operational intelligence, and PII on service members. In compartmentalized environments, a single misconfiguration or overlooked user privilege can be catastrophic.
Data-centric security shifts the focus from securing the boundaries of the network to securing the data itself, wherever it resides within the network. This approach answers three critical questions:
- Where is the data?
- Who has access to the data?
- What is happening to the data?
Without this level of visibility and control, it’s impossible to enforce Zero Trust principles or mitigate insider threats effectively. Since the DoD must comply with frameworks like the NIST Cybersecurity Framework and the DoD Zero Trust Strategy, data-centric security is not just important; it’s the key to effective cybersecurity.
In this article, we will showcase how Varonis protects complex environments utilizing various approaches to secure the most important aspect of a DoD environment: Data.
.webp?width=1337&height=1059&name=DRA-conversion-panel-image%20(1).webp)
Where traditional tools fall short
Many cybersecurity tools focus on logs, endpoints, or network traffic. While these areas are important, they don’t provide insight and context into the data itself.
For example, a firewall will not tell administrators if a user accessed classified documents in which they do not have a need-to-know requirement. An endpoint detection tool won’t flag a misconfigured folder that exposes thousands of sensitive documents with open access. Varonis, a unified Data Security Platform, provides administrators with current, contextual, and complete information on the sensitive data being secured.
Even within well-managed Active Directory environments, nested group permissions and legacy access rights make it nearly impossible to track data exposure manually. Agencies need automation, context, and continuous monitoring.
How Varonis solves the problem
Varonis brings automated, intelligent, and scalable data-centric security to the DoD. Here's how it addresses the department’s most pressing needs:
Comprehensive data discovery and classification
Varonis automatically scans file systems, email, and cloud platforms for sensitive content such as PII, PHI, and classified materials. Our platform identifies stale data, overexposed files, and data that violates compliance mandates. Varonis discovers many of these use cases out of the box, and it can also create custom rulesets tailored to an environment’s specific needs.
In a DoD environment where spillage or unauthorized disclosure can have national security implications, knowing exactly where the sensitive data lives is the first step.
Access intelligence and least privilege enforcement
Varonis continuously monitors and maps who has access to what data, and how they are granted these permissions, down to the individual file or folder. It visualizes complex permissions and nested groups, helping IT and security teams move toward a true least privilege model.
By automating access reviews and suggesting entitlement removals, Varonis reduces insider risk and minimizes the attack surface within a DoD environment.
Real-time threat detection and response
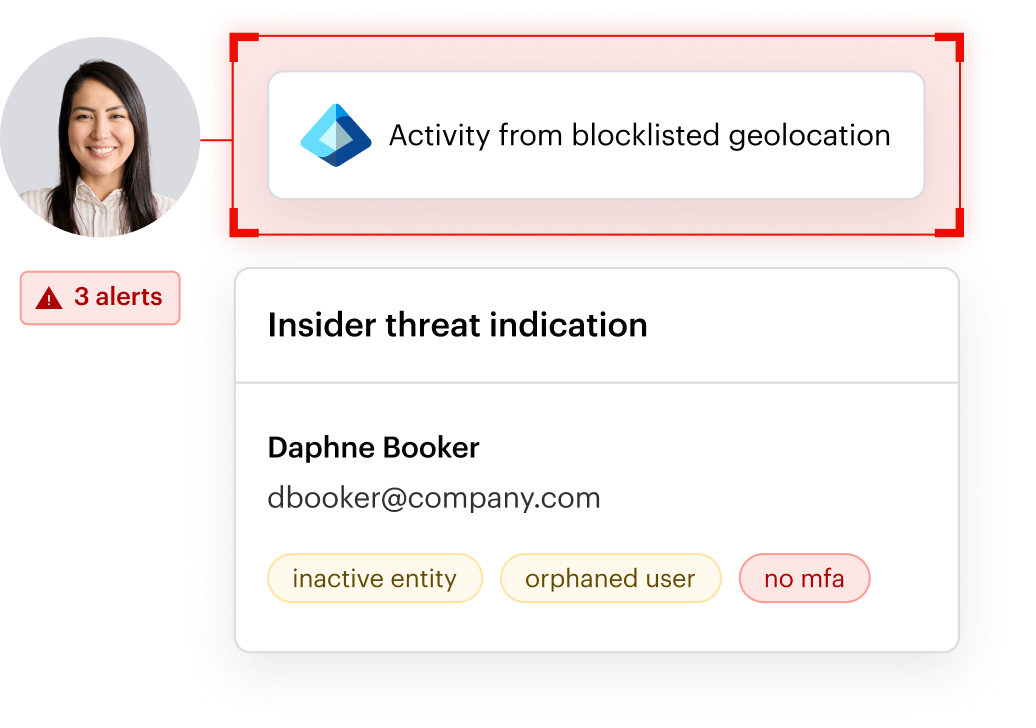
Varonis applies machine learning to detect abnormal behavior, such as bulk file downloads, encryption activity, or access from unusual locations. When a threat is detected through User and Entity Behavior Analytics (UEBA), Varonis can trigger alerts, quarantine accounts, and shut down risky behavior automatically without needing for manual administrative activity.
Real-time, behavior-based responses are critical when dealing with insider threats, Advanced Persistent Threats (APTs), and other malicious entities.
Audit readiness and compliance
Whether it's an audit, insider threat investigation, or a Zero Trust compliance check, Varonis provides a full audit trail of file activity, permission changes, and access history. With it, security teams can quickly produce forensics reports or prove adherence to DoD security controls.
Fit for DoD Environments
Varonis supports most data stores and filers and can operate within air-gapped networks or classified environments. Varonis’ architecture is designed to work without relying on external cloud services, making it a practical fit for sensitive and classified DoD deployments.
Furthermore, Varonis integrates well with SIEMs and SOAR platforms commonly used in defense operations, enabling correlation of file activity with broader network and endpoint data for holistic threat visibility.
Future-proof your classified data
The DoD cannot afford blind spots around data. As adversaries become more sophisticated and data volumes grow exponentially, perimeter defenses alone are not enough to secure data.
A data-centric security model is needed, and Varonis delivers the visibility, automation, and control required to protect sensitive data within DoD networks.
Defense agencies that are navigating the Zero Trust mandate, safeguarding sensitive information, and maintaining operational readiness need a data-centric solution to safeguard their data.
Trusted by the DoD to protect their most sensitive and targeted information, Varonis is the answer to the data security challenges faced by any defense organization. Get started today with a free Data Risk Assessment.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.