Have you ever had your lunch interrupted by a sudden barrage of security alerts? That’s exactly what happened to one of our clients when a frantic call from their Security Operations Center revealed a flood of suspicious emails. The culprit? A brand-new cyberattack mimicking the notorious Black Basta group’s latest technique — and it hit with lightning speed.
Normally, you’d expect employees to ring the alarm when they spot anything odd. But this time, there was only silence. Curious, our client checked their Secure Email Gateway (SEG) and confirmed a surge of suspicious traffic, which was the very thing that triggered the SOC’s warning. Then, they opened Varonis Interceptor and quickly pinpointed hundreds of phishing messages hitting a small group of users.
Within 90 minutes, the attackers had blasted 1,165 emails at 22 target mailboxes—over 50 messages per user, dropped in quick bursts. These rapid-fire attacks aimed to overwhelm inboxes and spark panic-clicking. But thanks to early detection from the Varonis platform, the client spotted the threat forming and moved fast to keep it from spreading.
Figure 1: Targeted campaign stats
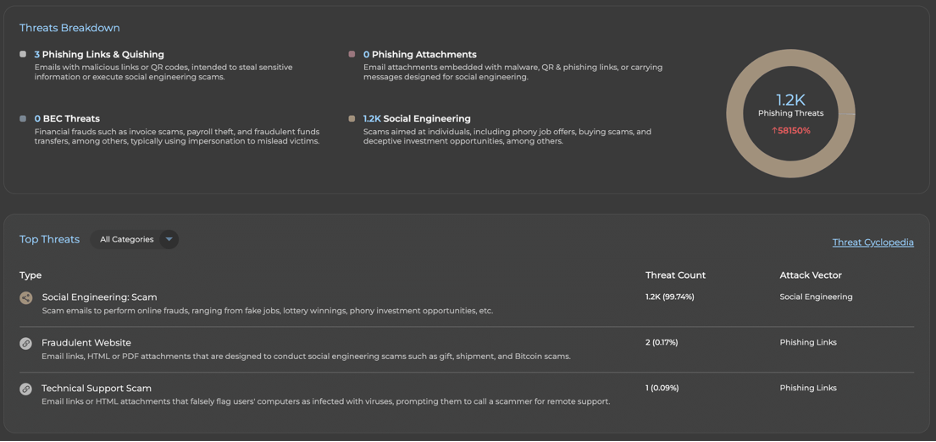
Figure 1: Targeted campaign stats
What’s the real goal of this attack?
We’ve seen a surge in ‘Black Basta’-style tactics, a fresh ransomware scam that fools employees into handing over remote control of their computers. First, they flood inboxes with legitimate emails, like newsletters or payment notices. These pile up, making it hard to tell which ones are safe. Then, when people feel overwhelmed, the attackers swoop in via phone calls or Microsoft Teams messages, posing as company tech support with a simple fix.
They speak with confidence to gain trust, directing users to install remote-access software like TeamViewer or AnyDesk. Once that software is on a device, attackers slip in quietly. From there, they can spread harmful programs or sneak into other areas of the network, clearing a path straight to sensitive data.
How Interceptor stopped an "undetectable" attack
Spanning 2024 and 2025, there has been a continued surge of phishing campaigns across the internet with similar markers. Even though others eventually catch them, Varonis was the first to deliver an automated AI-powered defense that could handle it in real time.
As new but similar campaigns are launched each month and a new wave of dangerous emails hits customers’ mailboxes — Varonis Interceptor spots and stops each within minutes rather than days. Below, we’ll show you the details of this specific attack and our approach.
The attack
Within 90 minutes from the start of the attack mentioned above, our systems intercepted a focused phishing campaign targeting businesses around the globe. Many emails pretended to be from familiar platforms like WordPress, using names like “Account Confirmation” or “Subscription Notice” to trick people into clicking malicious links. Attackers added urgency by including phrases like “Your account has been created” or “Please confirm your subscription.”
Figure 2: Examples of ‘Your account has been created!’ subject language
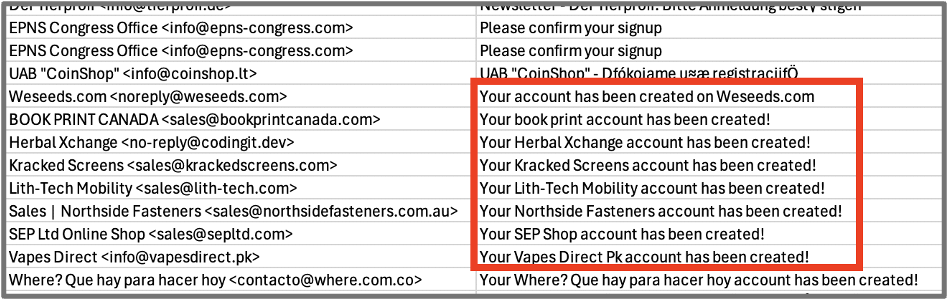
Figure 2: Examples of ‘Your account has been created!’ subject language
They even slipped in foreign languages or odd characters like “Confirmación de la cuenta de cliente” or “Votre compte sur Perle Dorée a été créé” which are intended to bypass simple keyword filters. The result? A flurry of convincing emails that could fool unsuspecting users into giving away their information.
Unveiling the strategy
When we investigated this phishing wave, we noticed five standout tactics that attackers used to fool people:
Platform impersonation
Criminals posed as big‑name platforms like WordPress and Shopify, even using real‑looking domains like “g.shopifyemail.com.” They sent fake account creation and subscription emails that seemed genuine at first glance.Sneaky domains
Many messages came from places like genomelink.io, mandrillapp.com, epgn.com, and thefreeadforum.com. These domains looked harmless on the surface but were cleverly chosen to slip past simple filters. Our top ten domains from this campaign included: gmail.com, epgn.com, thefreeadforum.com, genomelink.io, mandrillapp.com, vivianapetshop.com.ar, lawyerist.com, ecusoftservice.com, softmaker.de, canoncommunity.com
Figure 3: Sample of the types of rapid-fire scams
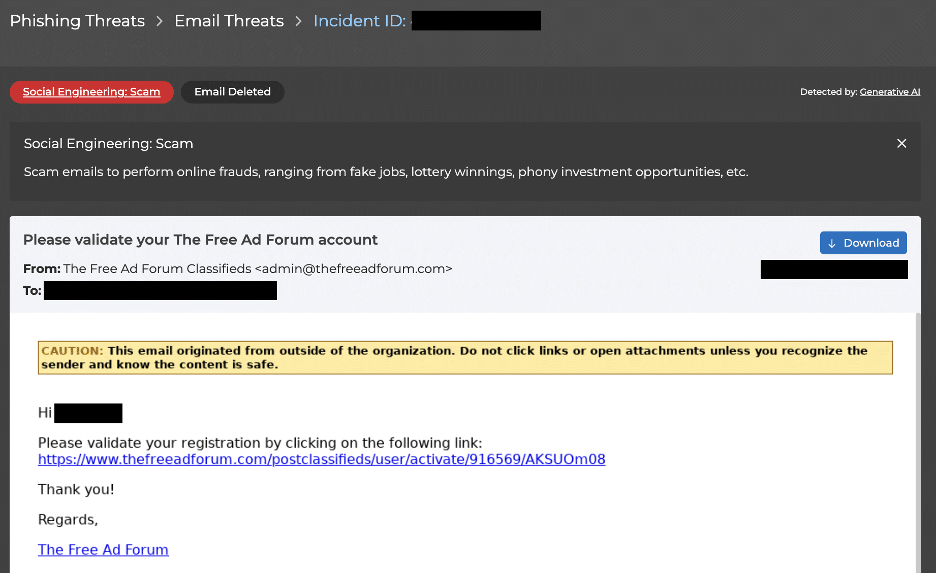
Figure 3: Sample of the types of rapid-fire scams
Character obfuscation
Subject lines were sprinkled with unusual letters (like é or ó) or small changes that made them look authentic. This tactic helped attackers dodge basic keyword checks and confuse busy readers.Varied account types
The emails referred to different user roles, from admin accounts to shopping subscriptions, so there was a better chance of catching someone’s attention or curiosity.Psychological triggers
By using urgent phrases like “Your account has been created” or “Please confirm subscription,” attackers created a sense of panic. In the rush to protect their accounts, some users clicked without thinking.How Varonis Interceptor mitigated the threat
At Varonis, we use a state-of-the-art phishing sandbox to go beyond ordinary filters. Rather than checking old lists or simple keywords, Interceptor’s phishing sandbox looks at how each email behaves in real time. This means that even if attackers hide malicious links behind strange symbols or encoded text, Interceptor can detect them. By testing links in virtual environments, we catch dangerous emails before they ever reach your inbox.
During this campaign, our system saw patterns like:
- URLs leading to fake login pages: Attackers hoped people would enter passwords on these sites.
- Domain spoofing: Criminals used subdomains to appear legitimate or trustworthy.
- Encoded URLs: When clicked, they secretly launched harmful software.
By focusing on behavior, not just appearances, Interceptor flagged each suspicious email and blocked it in real-time, keeping users safe.
Key takeaways from this attack
- WordPress impersonation: Attackers used WordPress branding to trick people, so it remains a hot target for scams.
- Subscription scams: Fake account creation or subscription emails are rising — always verify before you click.
- Unusual characters: Weird accents or foreign words in subject lines often signal trouble.
- Rapid execution: These scams happen fast, highlighting why real-time detection matters.
At Varonis, we don’t just react to threats — we redefine email security. Our AI-based approach delivers speed, accuracy, and continuous innovation so businesses can stay protected without slowing down.
Can our technology help your organization? Stay ahead with us and learn more about novel email phishing campaigns. Fill out the contact form to learn how we address these challenging techniques and see Interceptor in action.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.





-1.png)