This blog will cover five Varonis reports that you can automatically generate for data owners to promote strong data governance practices. We will show you how to create, customize, schedule, and interpret these reports.
Why Data Owners Should Pay Attention to Their Data
Business users often don’t have any idea who can and does access the data relevant to their department. While IT often has tools to analyze permissions, grant and revoke access, and troubleshoot issues, data owners are left in the dark.
Data is a business asset, not an IT asset. We want our business users to grant/revoke access when appropriate, spot unauthorized or suspicious access and, help manage the data lifecycle—getting rid of stale, risky data that we no longer need.
Varonis reports are a great way to put actionable information in front of the users that are in the best position to make smart decisions to protect the organization’s data.
Get a Free Data Risk Assessment
The Reports
Here are the five reports in DatAdvantage that your data owners can use to meet the objectives we discussed above.
The key is to set the subscription delivery parameters to “Report Server Email (Data-Driven).” In this context, “Data-driven” means that the report contains results based on data ownership in Varonis. Varonis will create reports for each data owner about their data, so data owners only see results about the information they actually care about. That way, administrators can set up a single subscription in Varonis, and send out a copy of that report to each owner about their relevant data activity.
For all of the reports discussed, schedule a Data-Driven subscription and select the delivery format for the report. My personal preference is to export reports as Excel files so I can manipulate the data so find what I need to see as quickly as possible. Your users might prefer PDF reports, or .CSV files. For ease of managing subscriptions, you will probably just want to settle on one standard format.
There are different ways to schedule and configure subscription reports depending on the size of your organization, the number of Varonis monitored resources, and the number of data owners. We will go over two basic options, but please consult your Varonis Sales Engineer or Professional Services for more customized guidance.
The first option – for large shops – is to schedule different reports per monitored resource. This means you would set the file server filter to a specific resource at a unique time. Varonis will generate all the reports for each server during their scheduled run for each data owner on that server. Schedule the next server to run after the previous server completes.
The second option – for smaller shops – is to remove the ‘File server’ filter and run the report with the filter Affected Objects -> Assigned Owner -> Management Status = Managed. This will create a report for all managed folders across all monitored resources in a single batch.
Again, please discuss with the Varonis support teams to determine the best strategy for your organization.
2.a.01 Access Statistics
What does it do? The Access Statistics report lists all the users who perform any activity in a folder or server. It’s an aggregation of how many file events a user generates over a certain period.
What’s the business benefit? Data owners can look for any oddities in event usage over the past 30 days. Did one user create many more events than usual?
Recommended schedule: Monthy
Pro tip: Data owners can group the results by user with a pivot table to see the total events easily.
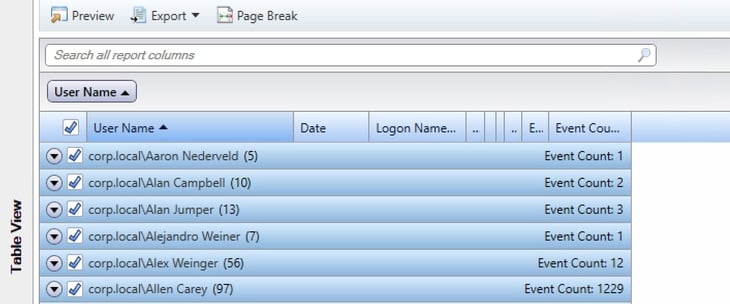
3.a.01 Group Members
What does it do? The Group Members report presents a list of users that are in each data owner’s group(s).
What’s the business benefit? Data owners can use this report to spot-check their group’s members between entitlement reviews.
Recommended schedule: Weekly
4.b.01 User or Group Permissions for Directory
What does it do? The User or Group Permissions for Directory report is a complete list of all permissions on the data owners’ file shares.
What’s the business benefit? Data owners can review this report to verify that there are no oddities in data access rights for each group on their file shares.
Recommended schedule: Weekly
Pro tip: Attackers add permissions to groups to move laterally across an organization and access more sensitive data.
4.g.01 Classification and Priorities
What does it do? The Classification and Priorities report shows the most recent (within the Relative Mode value) classification matches in the data owners’ file shares. Classification matches might exist in newly created files, new sensitive data in modified files, or matches from a previous scan.
What’s the business benefit? Data owners can review classified sensitive files in their shares to determine if they need to accept the risk as necessary for business use, and move, encrypt, or delete files that could become compliance risks.
Recommended schedule: Bi-monthly or Monthly
Pro tip: Add the Classification Results View role to data owners so they can use the DatAdvantage UI to see classification results in their shares.
7.b.01 Inactive Directories by Size
What does it do? The Inactive Directories by Size report will show data owners the folders in their shares that users don’t access.
What’s the business benefit? Data owners can use this report to determine if they can archive or delete data that their team no longer needs and has gone stale. Stale sensitive data is a treasure trove for attackers because people might not notice that they access it.
Recommended schedule: Monthly
Start The Varonis Operational Journey
Good data governance is not an accident. Organizations that take the necessary steps can get there. What we discuss here is a later stage of the Varonis Operational Journey. There are many steps that organizations must take to get to this level of data governance. You have to achieve least-privilege access, remediate Global Access, and then identify and assign data owners before implementing these reports.
Click here to schedule a meeting and start your Varonis Operational Journey so you can reach this level of data governance.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.











-1.png)