Easily monitor your file shares for suspicious activity, find sensitive data, enforce least privilege, and more, with Varonis.
- Cloud-native
- Petabyte scale
- Cross-platform

Partner with the leader in data security.
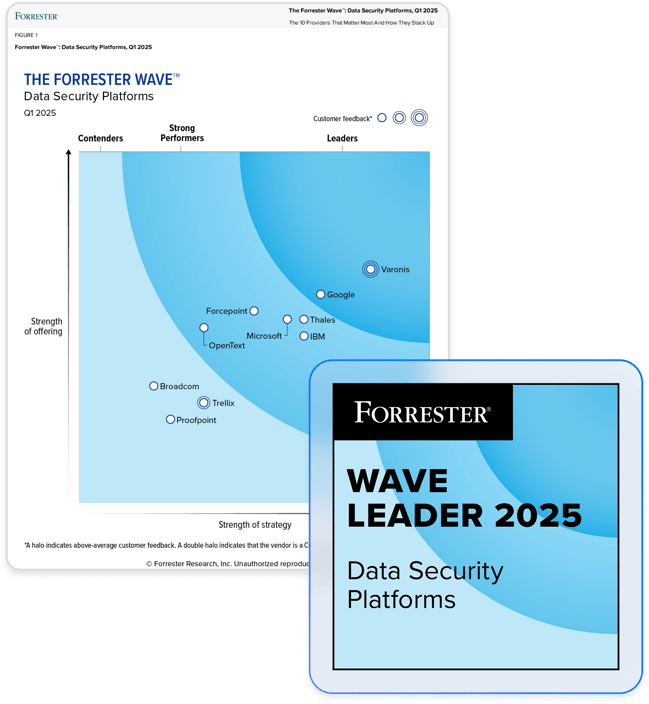
Go beyond native capabilities.
Discover and protect sensitive data.
Varonis automatically discovers and classifies sensitive data hidden in Windows file shares and NAS devices and shows you where you’re at risk. Our automated remediation policies determine who needs access and who doesn’t and then automatically replace high-risk groups with tightly managed groups.
Stop attackers and rogue insiders.
Varonis detects suspicious activity – such as accessing an unusual number of records, escalating privileges, or encryption of multiple files – that could put your file shares at risk.
Fill gaps in native auditing.
Varonis monitors SMB/CIFS shares without requiring native auditing. We capture all the critical events you need — like read, move, modify, and delete — accelerating cross-platform security investigations for cloud and on-prem environments.
"Pre-Varonis, we would have run around, scouring our servers, and spent tons of wasted hours looking through event logs to try and get a handle on what was happening. With Varonis, we have alerts that allow us to quickly understand and resolve situations."
Security Engineer
Large U.S. Regional Healthcare System
Read case studyVaronis solves common Windows and NAS data security challenges
Sensitive data discovery and loss prevention
- Varonis continuously finds and classifies sensitive data hidden in your Windows and NAS files shares
- Pairs classification results with permissions to reveal where sensitive data is overexposed
- Finds and fixes files that have been misclassified by end users or not labeled at all
Managing entitlements, permissions, and stale accounts
- Varonis gives you a clear view of effective permissions, including what users can do, and how they got that access
- Decipher complex permission structures like nested groups and inheritance
- Easily limit access change permissions to a small group of admins, archive and delete stale users to enforce least privilege, or correct org-wide permissions associated with sensitive files
Gaps in native auditing
- Varonis provides a comprehensive audit trail to answer key questions that can’t be determined using only the event log, such as when a file is created vs. modified or when someone failed to access a file
- Process millions of events per hour and monitor everything you need with minimal server and network overhead
- Accelerate cross-platform security investigations for cloud and on-prem environments
Protect your data, wherever it lives.
One platform for complete data security across multi-cloud, SaaS, hybrid, and AI.
Windows and NAS security resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital