Data-centric UEBA
Protect your data against stealth attacks and insider threats with hundreds of machine learning-powered threat models and a world-class incident response team.
- Real-time
- Cross-platform
- High-fidelity






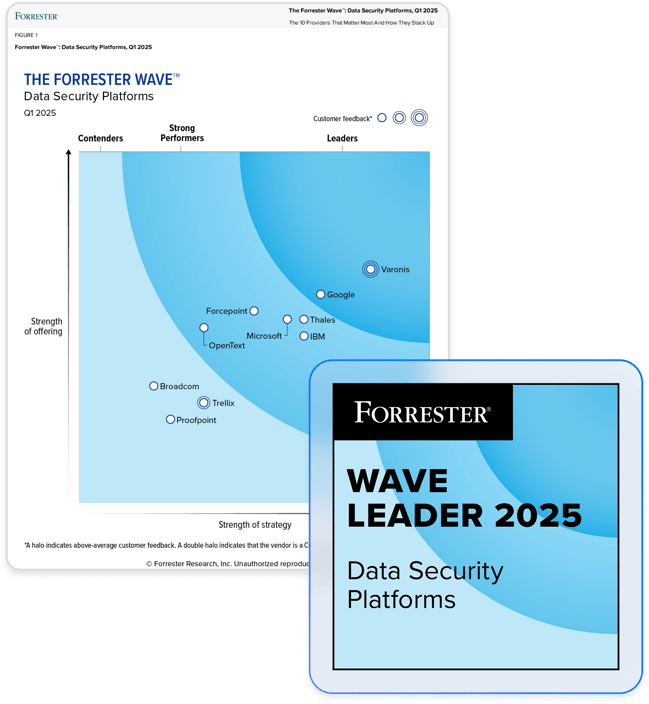
Partner with the leader in data security.
Real-time data-centric threat detection.
Extend your team with MDDR
- Varonis’ expert team monitoring your data
- 24x7x365 data detection and response
- Industry-leading 30-minute SLA on ransomware
Stop insiders, ransomware, and APTs
- Hundreds of threat models and behavioral analysis
- Complete cross-platform risk monitoring
- Track abnormal access, lateral movement, and privilege escalation
Prevent data exfiltration
- Detect file uploads, downloads, link sharing
- Reveal C2 traffic in DNS, web proxy, and VPN traffic
- Lockdown threat actors and protect sensitive data
Varonis has meant a lot for our organization. They were able to detect an incident that happened in our environment where other tools that we had in place did not detect it.
Continuous data monitoring
Varonis continually monitors your data, activity, and events to detect threats like APTs, malicious insiders, and public exposures and lock down access before a breach occurs. Our unique data-centric telemetry and UEBA catch threats before they escalate.
Data detection & response
Varonis combines sophisticated threat models with a world-class incident response team to detect and respond to stealth and insider threats. We also offer the option to extend your team with our 24x7x365 Managed Data and Detection (MDDR).
User & entity behavior analytics
Varonis uses machine learning to develop user behavior profiles and baselines for every user and device in your environment. This allows us to detect abnormal user activity, such as unusual file access, email send/receive actions, permissions changes, geo-hopping, and more.
Threat hunting
Our global team of cybersecurity experts watches your data, user activity, and network for threats and surfaces true incidents that require your attention, saving your team time and strengthening your security — all without needing additional resources from your team.
Managed data detection and response (MDDR)
Unlike traditional MDR services that are endpoint- and network-centric, MDDR focuses on threats to data. Our global team of elite threat hunters, forensics analysts, and incident responders investigate and respond to your alerts 24x7x365.
SIEM and SOAR integrations
Configure auto-response actions in Varonis or integrate Varonis with your existing SIEM/SOAR through any one of our connectors (Splunk, QRadar, Palo Alto Cortex XSOAR, Google Chronicle SOAR) or via syslog/SNMP.
Our customers have spoken
One platform for multi-cloud, SaaS, and on-premises data.
Varonis protects enterprise data where it lives — in the largest and most important data stores and applications across the cloud and behind your firewall.
DATA-CENTRIC THREAT DETECTION
Go beyond data-centric threat detection.
Varonis tackles hundreds of use cases, making it the ultimate platform to prevent data breaches and ensure compliance.
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital








