Monitor and automatically alert on leading identity threats, along with signs of a compromised user or machine account.
- Cross-platform
- Automated
- AI-powered


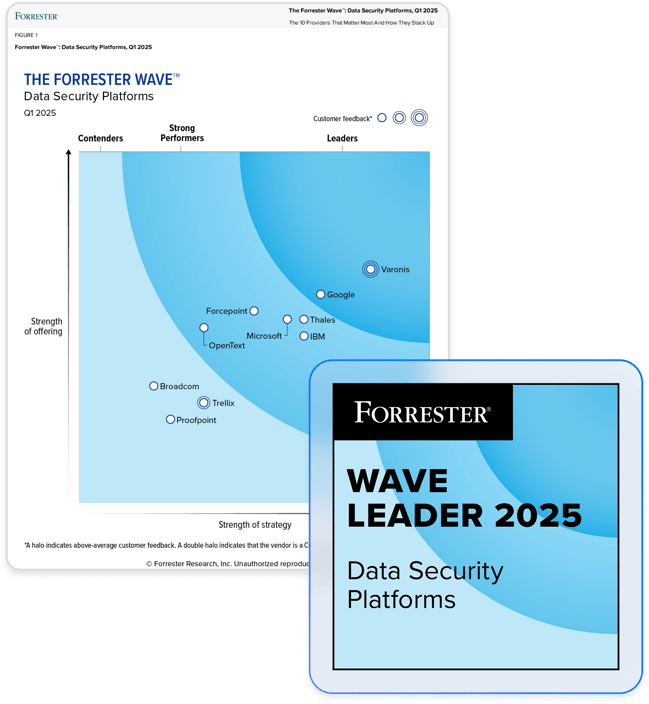
Partner with the leader in data security.
Observe and swiftly act on identity threats.
Visualizing identity threats across dozens or hundreds of information systems in cloud, SaaS, and hybrid environments can be challenging. Security teams must understand when an identity is compromised and quickly discern what the user, service account, or agent can access.
Complete the threat picture
See identities and respective threats that span identity providers and local accounts created in cloud applications. Uncover hidden activities across human and machine identities alike.

Detect abnormal behavior and insider threats
Correlate identity and data activity in real time. Pinpoint and track threats with a full forensics log - including authentication events, permissions changes, and subsequent data actions.

Mitigate AI threats

Varonis Identity Threat Detection and Response continuously monitors identities to proactively stop breaches.
Effortlessly understand the blast radius
- Visualize identity relationships and privileges at a glance.
- Identify lateral movement and privilege escalation.
- Correlate identity and data activity for precise threat detection.
Automate alerting with
AI-powered policies
- Surface patterns like failed login attempts and password resets.
- Notify of changes to authentication and authorization policies like MFA.
- Alert on brute force, password-spray, and other threats aligned to the MITRE ATT&CK framework.
Detect attackers using legitimate credentials
- Detect abnormal behavior and insider threats.
- Expose compromised accounts and privilege misuse.
- Correlate identity with UEBA analytics.
Our customers have spoken.
Protect your data, wherever it lives.
One platform for complete data security across multi-cloud, SaaS, hybrid, and AI.
Identity Threat Detection and Response Resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital