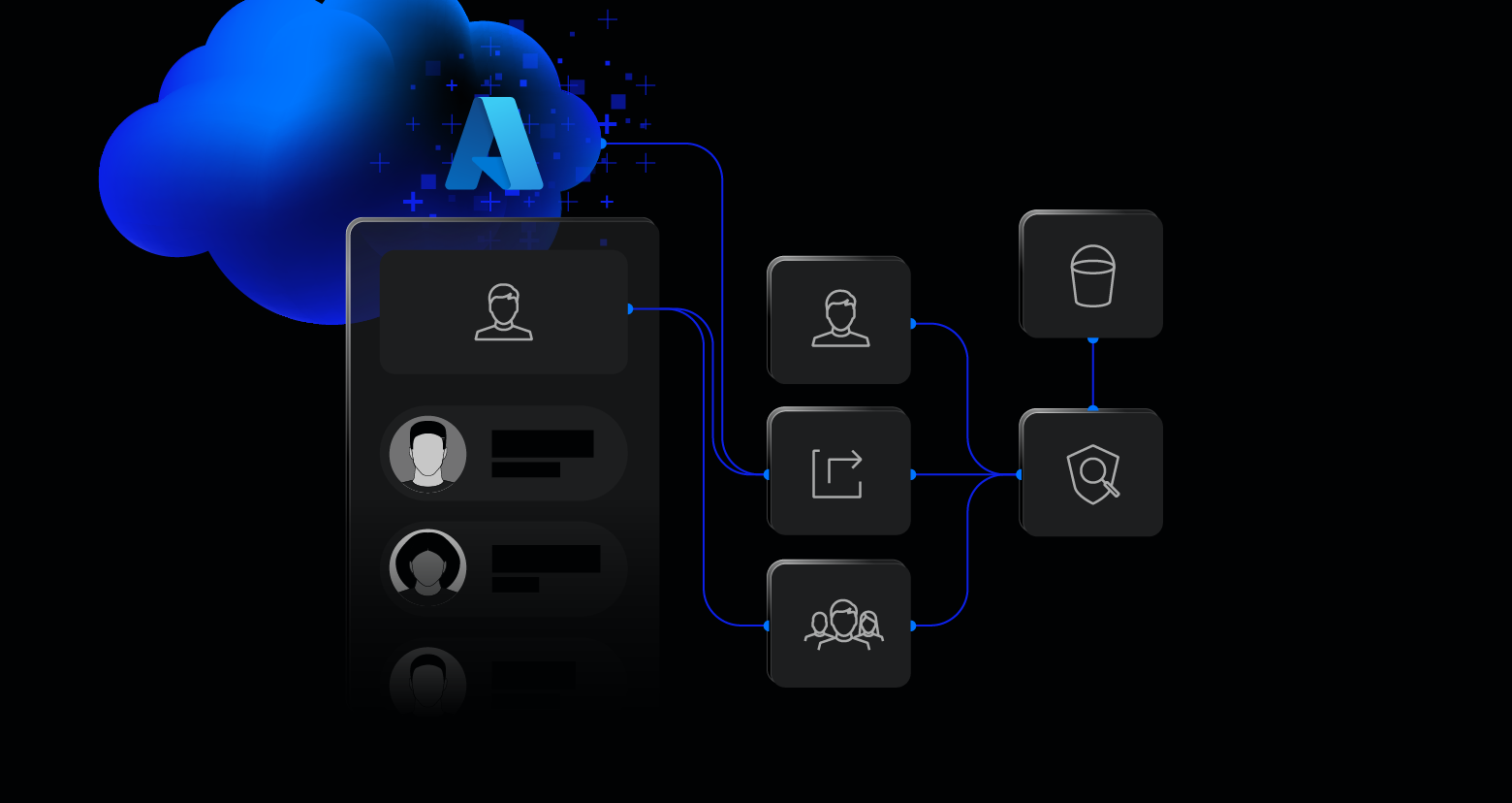
Seamlessly map identities across cloud and hybrid environments to enforce least privilege and reduce risk.
- Cross-platform
- Visibility
- Control


Partner with the leader in data security.
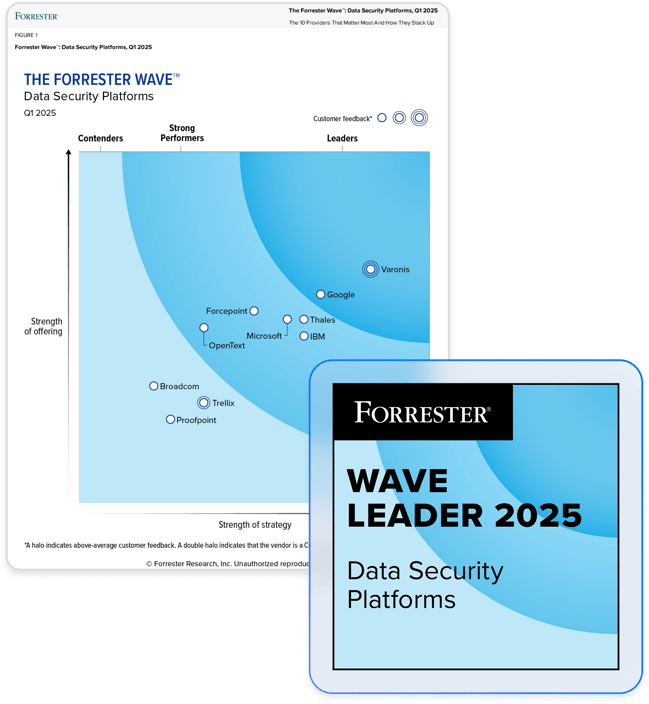
Untangle the identity web and enforce least privilege.
Organizations today are a complex web of users, agents, and non-human entities. Varonis seamlessly maps identities and users across cloud and on-prem environments, untangling the web, and making it possible to enforce least privilege.
Visualize identity relationships
Varonis visually maps identities and users across cloud, SaaS, and hybrid environments, providing full visibility into what accounts have access to critical data and why.

Enable least privilege
Varonis shows which users and identities are privileged, executive, service, external, or non-human. This enriched identity information is correlated with data activity to pinpoint risk.

Discover and catalog agents
Automatically discover and catalog agents, like Agentforce AI agents, including their topics, actions, deployment status, and permissions with unified visibility.

Varonis secures identities across cloud and hybrid environments.
Gain complete visibility into identities
- Clearly visualize relationships and privileges.
- Explore an intuitive, interactive access graph.
- Correlate identity with data activity to pinpoint risk.
Enforce least privilege for all entities
- Map human and non-human identities to right-size access.
- Detect orphaned, duplicate, and stale identities.
- Identify excessive permissions and privilege escalation.
Control AI agent access
- Monitor the data access and actions of AI agents.
- Automatically flag agents with unnecessary permissions.
- Identify unused or risky AI agents without disrupting operations.
Our customers have spoken
Protect your data, wherever it lives.
One platform for complete data security across multi-cloud, SaaS, hybrid, and AI.
Identity Protection Resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital