Centralize access control and effortlessly eliminate identity-based risks by right-sizing access.
- Cross-platform
- Automated
- Effortless


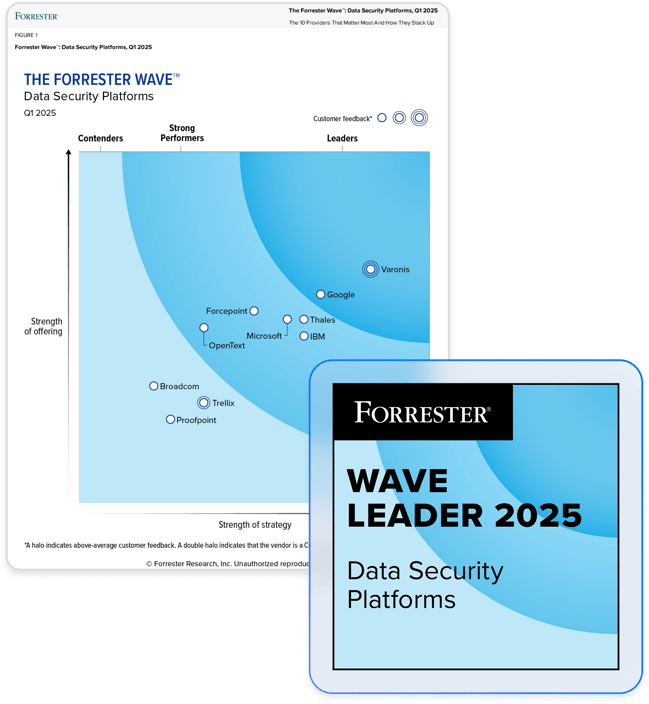
Partner with the leader in data security.
Effortlessly eliminate identity-based risk.
Map identity relationships
Varonis maps identities and users across cloud, SaaS, and hybrid environments, gaining full visibility into the continuous changes to permissions, configurations, memberships, roles, and more.

Access intelligence
Know who has access to your sensitive data at all times. The Varonis access graph factors in entitlements, group memberships, sharing links, muting permissions, and more, giving you the most accurate view of data risk on the planet.

Effortlessly reduce the blast radius
Effortlessly eliminate stale users, excessive permissions, and misconfigured roles, groups, and policies to effortlessly reduce the blast radius and achieve least privilege. Automate remediations rather than generating tasks or tickets.

Detect identity-based threats
Varonis uses UEBA to detect identity-based threats and anomalies, automatically alert and respond, and provide full forensic logs to pinpoint and track actions—streamlining investigation and accelerating response.

Varonis secures identities across cloud and hybrid environments.
Effortlessly reduce the blast radius.
- Visualize identity relationships and privileges at a glance
- Navigate an interactive access graph to uncover risk
- Correlate identity and data activity for precise threat detection
Enforce least privilege for all entities.
- Right-size access for human and non-human users and agents
- Detect orphaned, duplicate, and stale accounts
- Identify excessive permissions and privilege escalation paths
Detect attackers using legitimate credentials.
- Detect abnormal behavior and insider threats
- Expose compromised accounts and privilege misuse
- Correlate identity with UEBA analytics.
Our customers have spoken
Protect your data, wherever it lives.
One platform for complete data security across multi-cloud, SaaS, hybrid, and AI.
Identity Protection Resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital