A critical SharePoint vulnerability chain—now being actively exploited in the wild—is giving attackers unauthenticated access to enterprise environments. Dubbed ToolShell, this exploit chain is not theoretical. It’s operational, it’s scalable, and it’s already being used to compromise organizations that haven’t patched. If your infrastructure still relies on on-prem SharePoint, this is a high-priority threat that demands immediate action.
Executive summary
Attack timeline and flow clarification:
On July 14 SharePoint RCE demonstration posted on X using two known vulnerabilities from May 2025; combining into a full RCE flow.
CVE-2025-49706 - Authentication Bypass in SharePoint: By setting a specific Referrer header (e.g., /SignOut.aspx), attackers can bypass authentication checks on certain SharePoint pages like /ToolPane.aspx.
Patched on July 8 but fuzzed and got a new CVE-2025-53770 + CVE-2025-49704 – Arbitrary File Write in SharePoint: Attackers can exploit this to write arbitrary files (like .aspx webshells).
Together, these two flaws allow attackers to:
- Bypass login (CVE-2025-53770). Crafted HTTP request to /ToolPane.aspx with a Referrer header set to /SignOut.aspx, a variant of CVE-2025-49706.
- Upload a malicious file (CVE-2025-49704). Using the unauthenticated access - upload a malicious .aspx to /LAYOUTS/15/. The web shell was probably created using SharpPyShell Tool a variant of CVE-2025-49704.
- Attacker sends a GET request to malicious ASPX file in “/_layouts/15/spinstall0.aspx” - Triggering the web shell to invoke internal .NET methods to read the SharePoint server’s MachineKey configuration, including the ValidationKey and DecryptionKey.
- Using stolen Keys - Attacker can generate valid and signed __VIEWSTATE Payloads using ysoserial tool, to be used as valid requests for SharePoint.
- The payload is deserialized by SharePoint, triggering arbitrary command execution (This usually includes PowerShell commands)
ToolPane exploit
CVE-2025-49704 POC as shared by kaizensecurity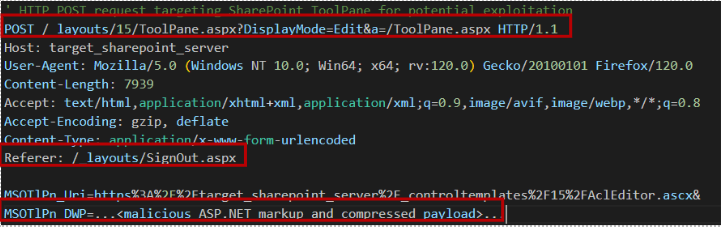
Spingstall0.aspx web shell
The following web shell is dropped and performing the following actions:
- Loads the System.Web assembly: This is the core ASP.NET library.
- Accesses the MachineKeySection: This section contains cryptographic keys used to:
- Sign and validate __VIEWSTATE
- Encrypt/decrypt authentication tokens and session data
- Uses reflection to bypass access restrictions: It calls a private method (GetApplicationConfig) to retrieve the current app’s cryptographic configuration.
- Prints sensitive keys to the HTTP response: This exposes:
- ValidationKey
- DecryptionKey
- Compatibility mode

What is the goal:
- Exposes cryptographic secrets
- Enables ViewState forgery: With the ValidationKey, an attacker can craft signed ViewState payloads that the server will trust — leading to unauthenticated RCE.
- Stealthy: The script doesn’t open a shell or beacon out — it just leaks secrets silently.
A realistic scenario
Imagine an attacker scanning your perimeter and finding an unpatched SharePoint server. Within minutes, they bypass authentication, drop a web shell, and silently extract your cryptographic secrets. No phishing. No brute force. Just a few HTTP requests and full control of your collaboration platform. From there, they can impersonate users, deploy malware, or pivot deeper into your network—all without triggering a single login alert.
Exposure and risk
Shodan and Censys scans have identified thousands of vulnerable SharePoint servers exposed to the internet. Many are hosted on Windows Server 2016 or earlier—platforms that are unlikely to receive timely patches. These systems are now being actively scanned and targeted, making them low-hanging fruit for attackers.
What makes ToolShell especially dangerous is its subtlety. The dropped web shell doesn’t beacon out or open a reverse shell. It simply leaks secrets—quietly, efficiently, and without raising alarms. By the time defenders notice, the attacker may already have persistent access and the ability to forge trusted requests.
Detection and mitigation
Organizations with AMSI (Antimalware Scan Interface) enabled are at a reduced risk, as AMSI can detect and block some of the malicious scripts used in this attack chain. Similarly, environments with EDR (Endpoint Detection and Response) solutions in place may detect suspicious process chains associated with dropped web shells or unauthorized PowerShell activity.
But detection alone isn’t enough. If your SharePoint environment is exposed to the internet and running an unpatched version, patching is non-negotiable. For systems that may have been compromised, rotating ASP.NET machine keys is essential to invalidate any stolen cryptographic material.

Indicators of compromise: what to look for
Several IOCs have been observed in the wild and can help identify whether your environment has been targeted or compromised. One of the most telling signs is the presence of a file named spinstall0.aspx located in the SharePoint layouts directory. This file acts as a web shell and is used to extract sensitive cryptographic keys from the server.
In addition to file-based indicators, several IP addresses have been linked to scanning and exploitation activity. These include 107.191.58[.]76, 104.238.159[.]149, and 96.9.125[.]147. Reviewing server logs for connections from these addresses may help identify attempted intrusions.
File hashes associated with known malicious payloads include:
- 27c45b8ed7b8a7e5fff473b50c24028bd028a9fe8e25e5cea2bf5e676e531014
- 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
- b336f936be13b3d01a8544ea3906193608022b40c28dd8f1f281e361c9b64e93
A compiled version of the web shell has also been observed with the hash 8d3d3f3a17d233bc8562765e61f7314ca7a08130ac0fb153ffd091612920b0f2.
Additional artifacts include a secondary web shell (4a02a72aedc3356d8cb38f01f0e0b9f26ddc5ccb7c0f04a561337cf24aa84030) and a forged payload (fa3a74a6c015c801f5341c02be2cbdfb301c6ed60633d49fc0bc723617741af7).
What you should do now
- If you're running SharePoint Server Subscription Edition, 2019 or 2016, install the latest patches right away.
- If you think your environment may have been exposed, rotate your machine keys and scan for known IOCs using tools like those from BlueFire RedTeam.
- On-prem SharePoint support ends in July 2026. As that date approaches, attackers are expected to increasingly target legacy systems.
- ToolShell may be the first of many exploit chains aimed at aging infrastructure—now is the time to plan your migration and strengthen your defenses.
- In a world where attackers move fast and legacy systems lag behind, Varonis helps you stay ahead.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








