Phishing tactics have taken a creative turn with the abuse of SVG files, turning innocent-looking images into vehicles for high-impact attacks.
A simple “invoice” attachment can conceal sophisticated JavaScript, obfuscated in CDATA blocks, that decodes gibberish strings via XOR and launches redirects or overlays the instant someone opens it in a browser. This kind of attack is especially challenging because it lives where most security tools don’t look — in code executed by an image.
In this blog, we’ll unpack SVG threats, why attackers love them, and how Varonis Interceptor can help combat SVG-based attacks.
Unpacking a real-world SVG threat
A seemingly harmless email
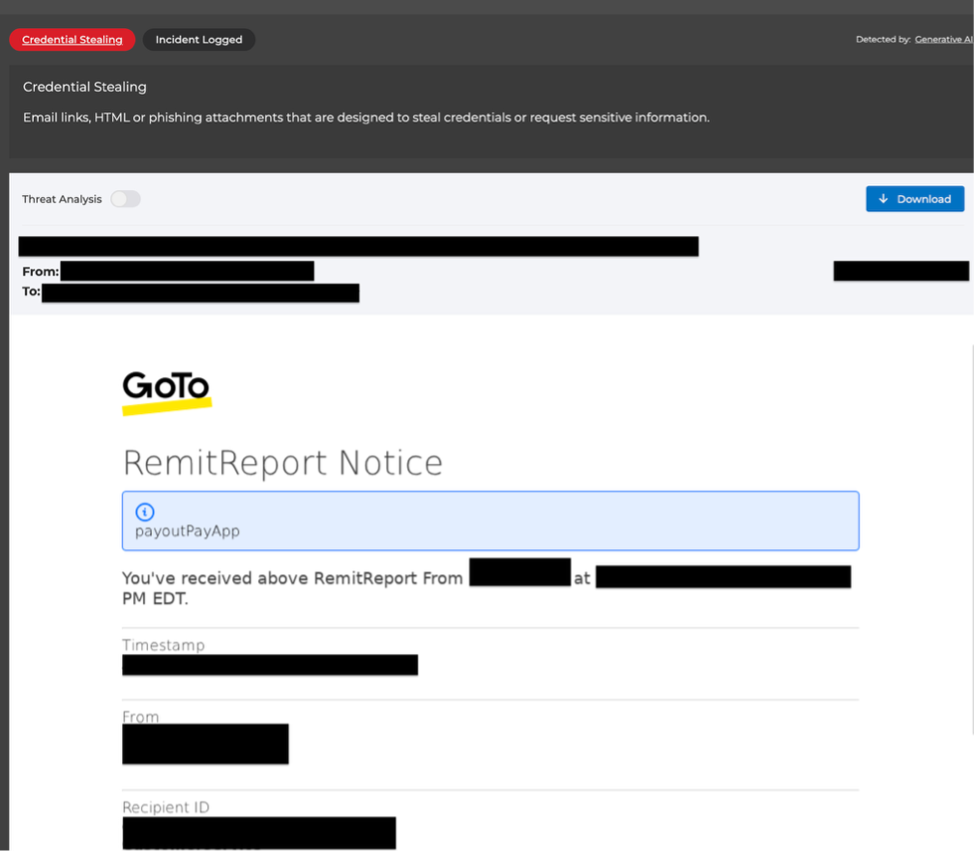
A seemingly harmless email
At its core, the SVG attachment looks like a logo or a document preview. Hidden inside, a script block wrapped in CDATA contains dozens of unreadable characters. With a clever XOR decoding trick and a single call to new Function(), the Javascript payload bursts into action, redirecting users or overlaying a fake sign-in prompt. Most legacy email filters only see “image/svg+xml,” giving the attack a free pass into the inbox.
Security teams must address this new threat as phishing evolves beyond simple link-based tricks.
This SVG appears safe, but a script block inside CDATA decodes an obfuscated payload and instantly executes credential-stealing logic.

This SVG appears safe, but a script block inside CDATA decodes an obfuscated payload and instantly executes credential-stealing logic.
Why “harmless images” are ideal for attackers
The text-based nature of SVG files means attackers can embed multi-layered payloads, hide malicious intent, and dodge detection at every step. These emails don’t come with scary red flags or obvious malicious links. Instead, they slip by with encoded scripts that evade signature and pattern-based blocking — all because they’re wrapped in an “image” format.
Legacy email security tools often fail here. While content filtering for documents and attachments has improved, SVGs sit in a grey area. This is because they’re rarely used for legitimate business and rarely scanned in depth. Attackers target this blind spot, launching brand-mimicking overlays and automated redirections from the moment the message is opened.
What smart sandboxing can see that others miss
Modern email security platforms rethink this problem, using cloud sandboxing and AI to look past file extensions and inspect the actual code and business context. The best protection doesn’t just scan attachments: it opens files in virtual browsers, parses embedded scripts, inspects for sideloaded logic, and applies Vision AI to detect stolen branding attempts.
This approach matches emerging tactics. Platforms built for today’s threats correlate sender and message patterns, check for contextual anomalies, and use natural language processing and visual cues to generate risk scores. By integrating advanced sandbox technology, these solutions prevent threats from ever reaching downstream users or applications, regardless of format, obfuscation, or delivery method.
The Varonis Interceptor difference
With advanced vision-driven sandboxing and message context analysis, cloud platforms can reveal attacks that pass undetected through traditional filters. Varonis Interceptor uses deep inspection to catch credential overlays, sideloaded JavaScript, and risky behaviors in real time — scanning across email, chat, and collaboration apps.
Varonis Interceptor evaluates the entire message, not just the file: is it coming from a trusted sender, does it match known patterns, is it part of a larger campaign? Context-aware defense allows Interceptor to decode overlays, check image branding with AI, and track conversation history for suspicious changes — all in milliseconds. This is where visibility meets action, and where organizations can finally get ahead of attackers.
Collaboration and action
What does SVG file abuse mean for the cybersecurity community? The shift to more contextual defense goes hand-in-hand with a culture of sharing stories and lessons.
The SVG exploits landing in inboxes today affect everyone; exposing these tactics and talking through changes on LinkedIn, in forums, or at conferences helps build a smarter and more resilient network of defenders.
Inviting colleagues, partners, and even vendors into the conversation about how image-based and multi-channel phishing is evolving brings clarity for the whole community. Sharing anonymized screenshots and SVG payloads not only educates, but arms others with the reality of what’s lurking beneath familiar graphics.
As organizations review their security stack, it’s worth asking: Are current solutions set up for code that masquerades as pictures? Is every message, from every channel, being seen for what it really is, and not just what it pretends to be?
A new approach to phishing defense
With attacks using increasingly sophisticated obfuscation to bypass everyday tools, security teams must be willing to adopt solutions that provide true visibility.
Investing in advanced sandbox technology and context-aware intelligence is no longer just “nice to have”— it’s the bedrock of trust for modern businesses and the future of security.
By opening these stories up for wider review, teams can work together to decode the techniques, flag suspicious messages, and build a layered approach that sees every threat for what it is, no matter how well it hides.
Ready to change how your organization sees and reacts to phishing? Start by sharing, engaging, and comparing approaches with other security professionals. Together, the community can set the standard and push attackers back into the shadows.
If you’re looking to take advantage of deep inspection to combat attacks, schedule a demo of Varonis Interceptor today.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.



-1.png)