The state of Illinois has recently passed several key pieces of legislation designed to bolster the data privacy rights and protections of residents. Illinois privacy law seeks to achieve similar goals as international regulations like the EU's General Data Protection Regulation (GDPR) and US privacy laws such as the California Consumer Privacy Act (CCPA).
Discover your weak points and strengthen your resilience: Run a Free Ransomware Readiness Test
To better protect natural persons residing in the state, the Illinois Personal Information Protection Act (PIPA) was signed in June of 2005 by the state legislature and took effect on January 1, 2006. In 2017, PIPA was then updated to consider changes in technology and data collection methods, such as biometrics.
This article will give you the necessary background on PIPA, who it applies to, and how to best position your organization from a compliance standpoint.
- What is the Personal Information Protection Act?
- Who is Affected by PIPA?
- Key Components of the Illinois Privacy Act
- What Data Does PIPA Protect?
- What Can I Do to Comply with PIPA?
- Who Do I Contact If I Suspect a Breach?
What is the Personal Information Protection Act?
PIPA was introduced to protect Illinois residents from the mishandling, misuse, or abuse of their personal information. The act imposes a variety of requirements on companies and other organizations that collect, handle, or store non-public personal information. PIPA also spells out the steps that businesses must take in the event of a security breach.
Moreover, businesses and organizations that possess the personal information of Illinois residents must implement and maintain reasonable security measures to protect said data from unauthorized access, use, or modification. Organizations also need to include data protection provisions in contracts with third parties with which data is stored or transmitted.
Since its introduction - and subsequent update - PIPA's goal is to ensure that personal, sensitive information of Illinois residents is handled, stored, and protected properly.
Who is Affected by PIPA?
PIPA applies to any businesses, organizations, or entities that operate as data collectors in Illinois. This includes for-profit companies, government agencies, non-profits, universities, and any other entity that deals with non-public personal information. These entities may or may not be legally based in Illinois, but if you collect or handle private, non-public data of Illinois citizens, then you're subject to PIPA.
A variety of companies across industries should be aware of - and compliant with - PIPA. Whether you're a healthcare or insurance company that collects private customer data, or a marketing entity that uses data for targeted ads, if any of your users are in the state of Illinois you'll need to become PIPA compliant at some point.
Key Components of the Illinois Privacy Act
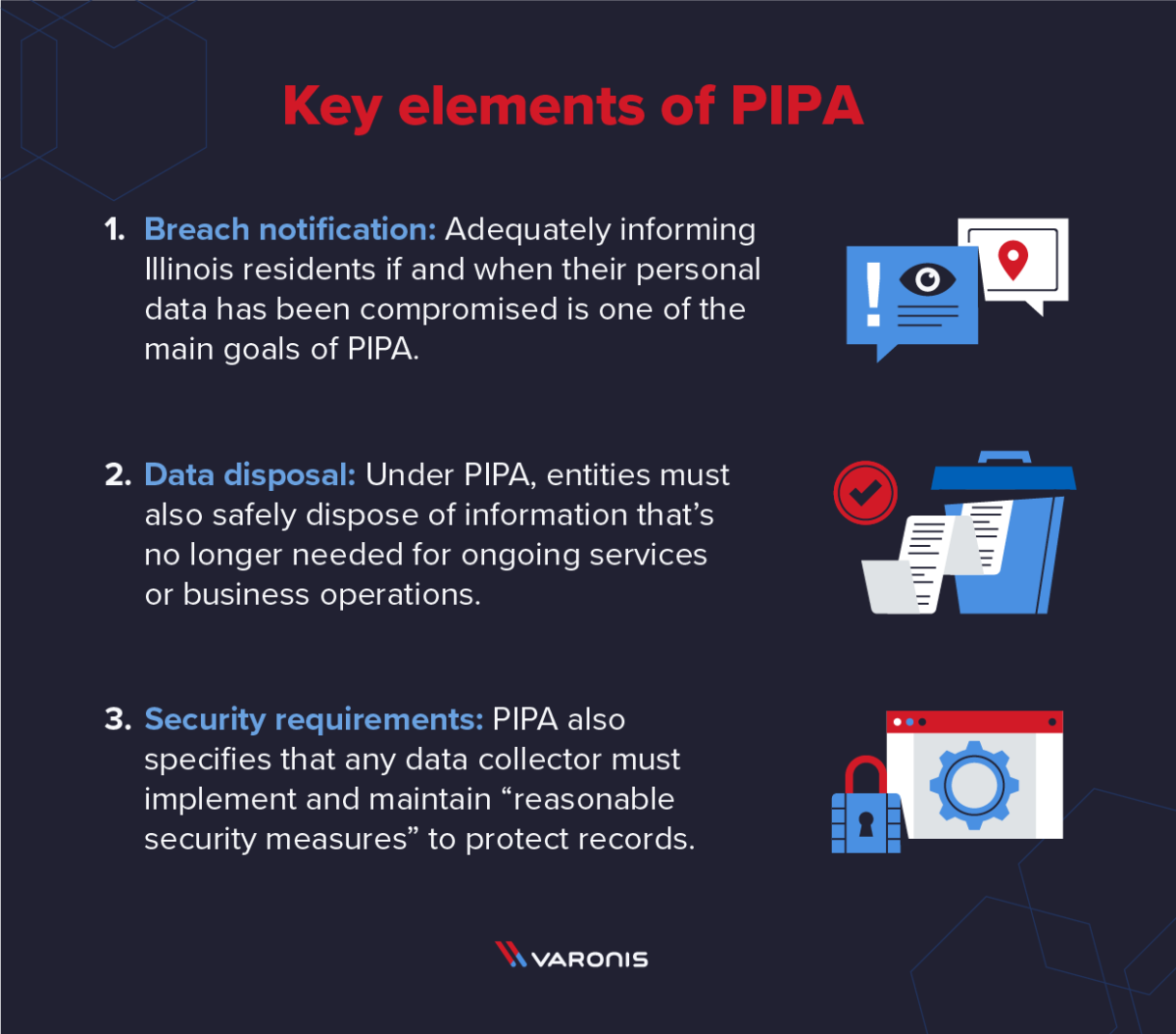
The PIPA Illinois privacy act contains several key elements that organizations collecting and handling data of Illinois residents should know about.
1. Breach Notification
Adequately informing Illinois residents if and when their personal data has been compromised is one of the main goals of PIPA. If a data breach does occur, the entity is required to notify affected consumers "in the most expedient time possible, without reasonable delay," according to the statute. Data collectors must notify persons via written or electronic notice - or if these avenues are unavailable - a general notification via statewide media outlets may suffice.
2. Data Disposal
Under PIPA, entities must also safely dispose of information that's no longer needed for ongoing services or business operations. This includes either paper or electronic documents containing the personal information of Illinois persons. Paper records must be properly burned, shredded, or otherwise disposed of, and electronic records must be rendered unreadable and unrecoverable. This ensures the long-term data safety and privacy for Illinois consumers.
3. Security Requirements
PIPA also specifies that any data collector must implement and maintain "reasonable security measures" to protect records from unauthorized access, acquisition, destruction, use, modification, or disclosure. While PIPA doesn't spell out specific measures, organizations can meet these standards by complying with applicable federal or state data protection standards such as HIPAA.
What Data Does PIPA Protect?
The following data types are the main forms of personal data that falls under the purview of PIPA protection:
- Social security numbers
- Driver's license or state ID number
- Federal passport number
- Medical account numbers
- Financial account numbers
- Credit card or debit card numbers
- Account passwords or security codes
What Can I Do To Comply With the Illinois Personal Information Protection Act?

Complying with the Illinois PIPA doesn't have to be incredibly complex or difficult. By taking a few basic steps, you can ensure that the data collection, storage, and disposal processes of Illinois citizens are safe and fully PIPA compliant.
1. Review Administrative Processes
One of the best things you can do to comply with PIPA is review your entire administrative processes surrounding confidential information collection and overall data privacy of Illinois citizens. Take a close look at how you gather data, and which types fall under PIPA jurisdiction. By mapping out the entire process, you can gain a clear picture of what gaps to fill.
2. Implement Breach Notifications
Adequately informing Illinois persons in the event of a breach is one of the most critical aspects of PIPA. In addition to reviewing administrative processes, also take a look at what your documented best practices for breach notifications are. Ensure that you're able to quickly notify people via email or snail mail, and have media contacts to announce breaches to cover those persons whose direct contact you may not have.
3. Encrypt All Communications
In particular, encrypting email communications is a key step towards preventing data breaches and ensuring ongoing PIPA compliance. Email encryption is becoming standard practice and requirements for it are increasing in both international and US privacy laws. Implementing encryption technology can help prevent breaches so that you won't have to ever deal with PIPA's notification requirements in the first place.
4. Delete Confidential Information
Deleting private information is standard data security best practice, and is an important pillar of PIPA compliance. Make sure that your data collection and security plan has detailed and thorough processes for deleting data, whether it be physically or digitally. As mentioned, this includes shredding or burning paper documents and rendering digital records unrecoverable. If you don't need the private data to provide services or operate your business, get rid of them ASAP.
Who Do I Contact If I Suspect a Data Breach?
If you do suspect a data breach, you should contact the proper parties to ensure you're PIPA compliant and avoid any fines and penalties. Utilizing the Varonis Data Security Platform is helpful because you'll be able to monitor your systems and detect breaches as soon as they happen, so you can be sure to notify the right parties within the PIPA specified window.
Here are the people, parties, and entities you should contact if you suspect an Illinois data breach:
- Illinois State Police Cybercrime Unit. +1 217 782 6637
- Chicago Sun Times Legal Notices. +1 312-321-2345
- State of Illinois Attorney General. 1-800-243-0618
- Varonis for PIPA Compliance Assistance. 1-877-292-8767
Closing Thoughts
Regulations like the California Privacy Rights Act are spurring other states like Illinois to adopt similar standards and practices - hence the passage and update of PIPA. But PIPA compliance is more than just about notifying the right people when a breach takes place. The best thing you can do is protect Illinois citizen data and prevent breaches from happening in the first place. By using technologies like email encryption and advanced threat detection, you can reduce the chances of breaches significantly and maintain PIPA compliance over the long haul.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.




-1.png)



