On May 1st 2024, Dropbox disclosed a cybersecurity breach in which hackers abused a service account to gain access to Dropbox Sign’s production environment and access customer data.
While there is no evidence that attackers accessed Dropbox customer payment information, agreements, or templates, they did access customer data including emails and usernames. In some cases, phone numbers, hashed passwords, and other authentication-related details like OAuth tokens, MFA keys, and API keys were also accessed.
For Dropbox Sign customers who enabled API access to other applications, the theft of these authentication tokens could allow a threat actor to connect to another connected application, potentially exfiltrating sensitive data.
What does this mean for my organization?
Any breach of accounts with access to other applications could provide attackers with access to connected SaaS platforms, posing a risk to affected Dropbox Sign customers.
Dropbox Sign is a product provided by Dropbox, allowing users to sign documents and contracts. One unique feature of Dropbox Sign is the ability to integrate with many popular SaaS platforms, such as Google Drive, Microsoft Office365, Salesforce, and Slack for document signing.
An attacker could use API or OAuth access tokens compromised in this breach to authenticate with SaaS applications connected to Dropbox, executing API commands depending on the scope and permissions of the stolen tokens. Because Dropbox Sign allows users to sign documents from those SaaS applications, there is a risk these exposed tokens might allow attackers to read sensitive files, which may lead to data exfiltration.
To address this, Dropbox has taken several steps to mitigate the impact of this breach including:
- Resetting user passwords
- Logging users out of any devices they had connected to Dropbox Sign
- Rotating all API keys and OAuth tokens
We advise Dropbox Sign customers to:
- Rotate relevant keys used by integrations with Dropbox Sign.
- Look for anomalous user or resource creation by OAuth applications related to Dropbox Sign integrations.
- Review actions performed by integration keys and credentials used for Dropbox Sign integrations.
This is not the first time Dropbox has suffered the abuse of credentials, as in 2022 Dropbox disclosed a security breach after attackers stole over 100 code repositories by breaching the company's GitHub account by using stolen employee credentials.
Non-Human Identities are Driving Breaches
In the last several months, breaches involving non-human identities have captured the spotlight as many large companies like Microsoft, Okta, and Sisense experienced breaches involving such identities.
These non-human identities are targeted by attackers because they are commonly used in integrations with third-party applications, have access to sensitive environments, and often have no easy way to monitor these identities for suspicious behavior.
Securing and monitoring non-human identities is critical. If these non-human identities are compromised, threat actors may easily gain wide access to the breached environment without anyone noticing.
How Varonis can help
Varonis provides a complete and centralized overview of the third-party applications connected to your SaaS applications and the risks they pose. With Varonis, security teams can:
- Proactively identify risky apps in their environment
- Understand which users are connected to each app and the permissions they grant them
- Monitor application activity for suspicious or risky behavior that could indicate a threat
- Remove third-party applications from each user or entirely from the environment.
Varonis’ centralized third-party application risk dashboard enables admins to see the total number of apps in your environment, whether active or stale, the level of risk they pose, and if they have been verified by admins — along with other key risk indicators.
Gain a centralized overview of the third-party applications in your environment and the risks they pose.
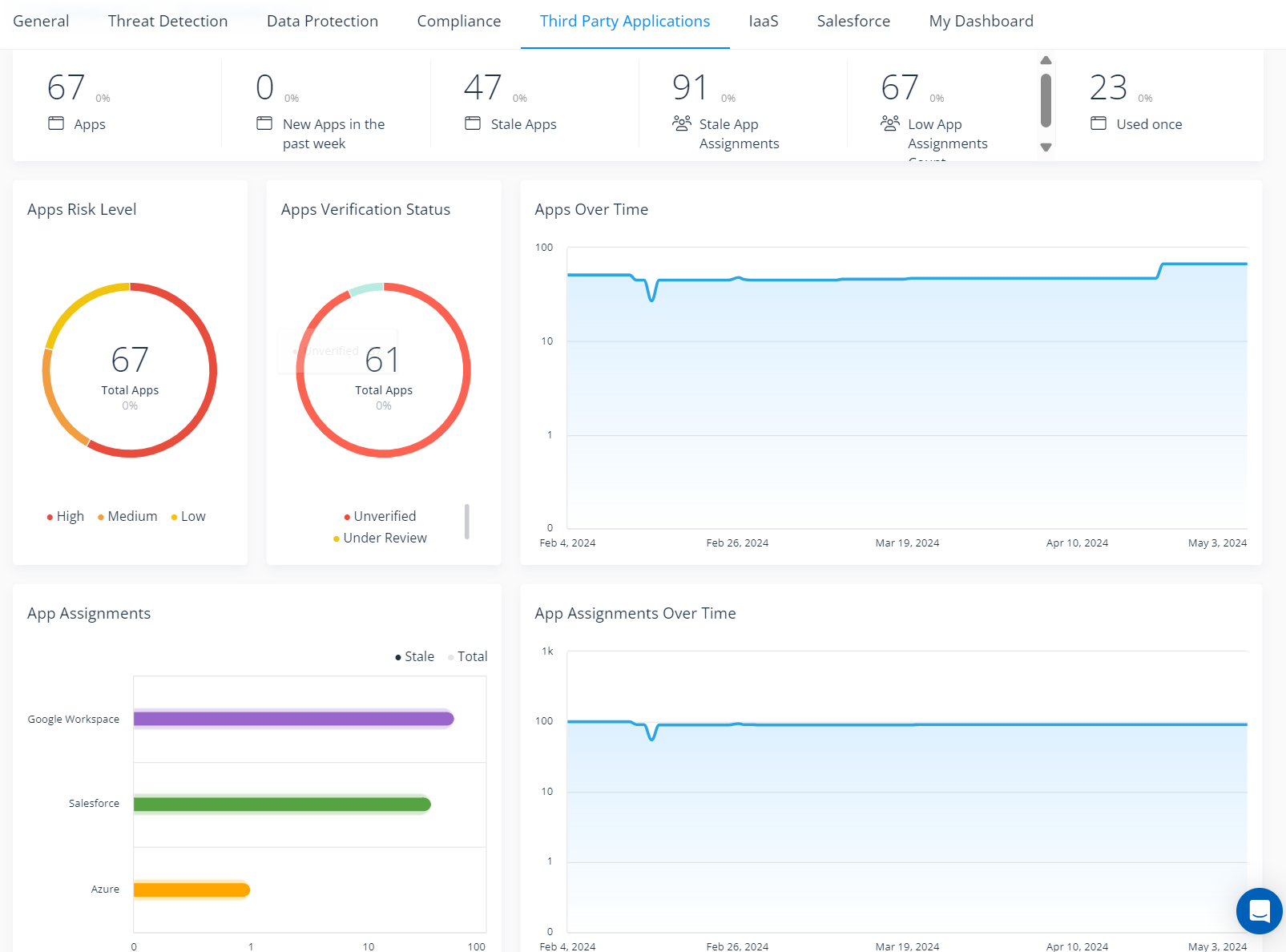
Gain a centralized overview of the third-party applications in your environment and the risks they pose.
Varonis tracks the activity of all your third-party applications and provides a complete and human-readable audit trail of cross-cloud events. We’ll detect any unusual or risky activity and alert you in real-time, so you can immediately investigate and remove the offending third-party app. Varonis can also identify when applications impersonate users and perform activity on their behalf.
Monitor third-party application activity, identify impersonation, and detect threats.
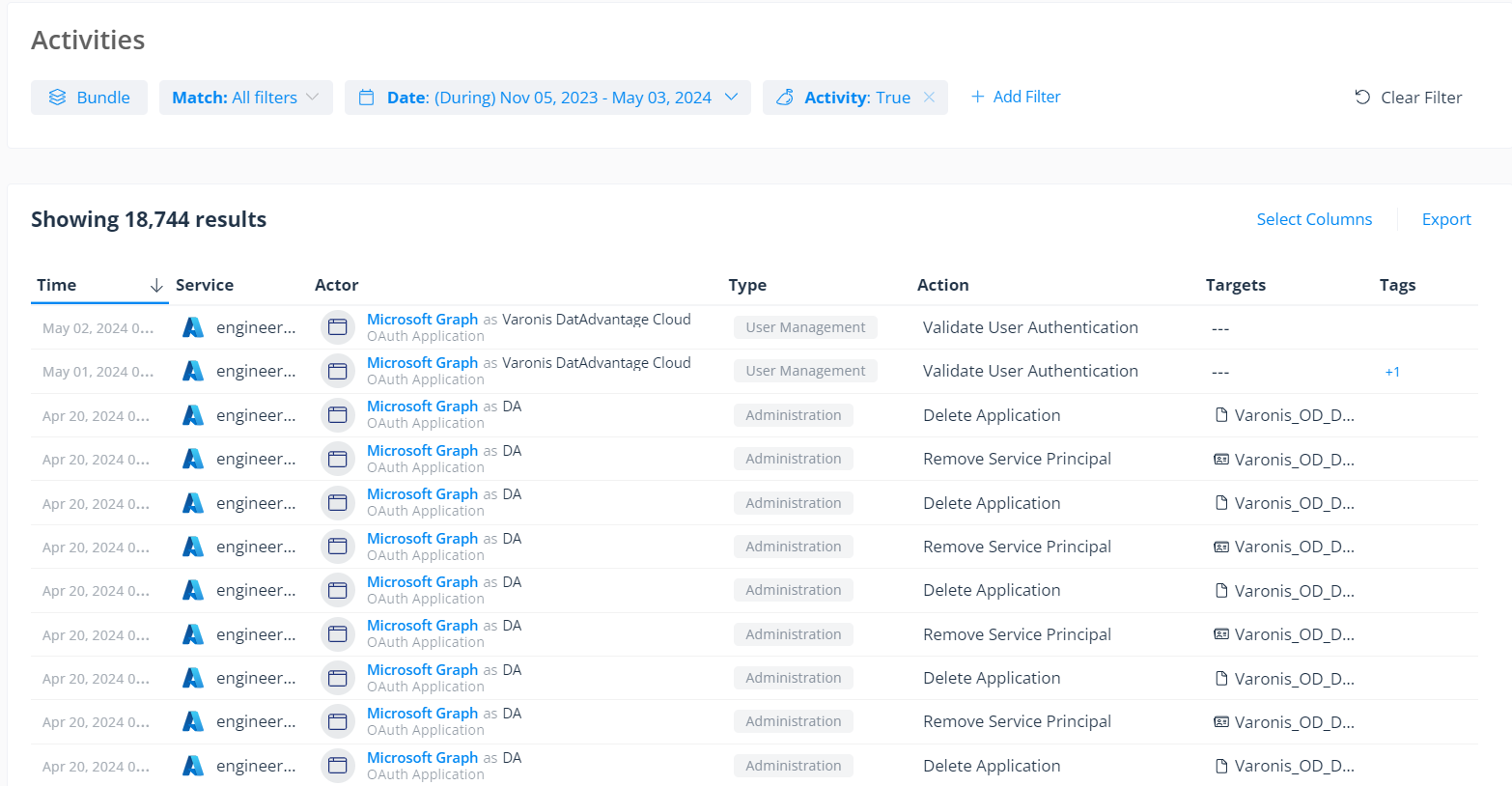
Monitor third-party application activity, identify impersonation, and detect threats.
Varonis gives you a clear picture of the effective permissions of each third-party app. We break third-party app permissions down to a simple to understand CRUDS (Create, Read, Update, Delete, and Share) model making it simple to understand an app’s effective permissions and the risk they pose to sensitive data.
With our bi-directional permissions view, you can also see all the users using a single app or click a user and see every application they have connected.
Get a clear understanding of each application's permission scope.
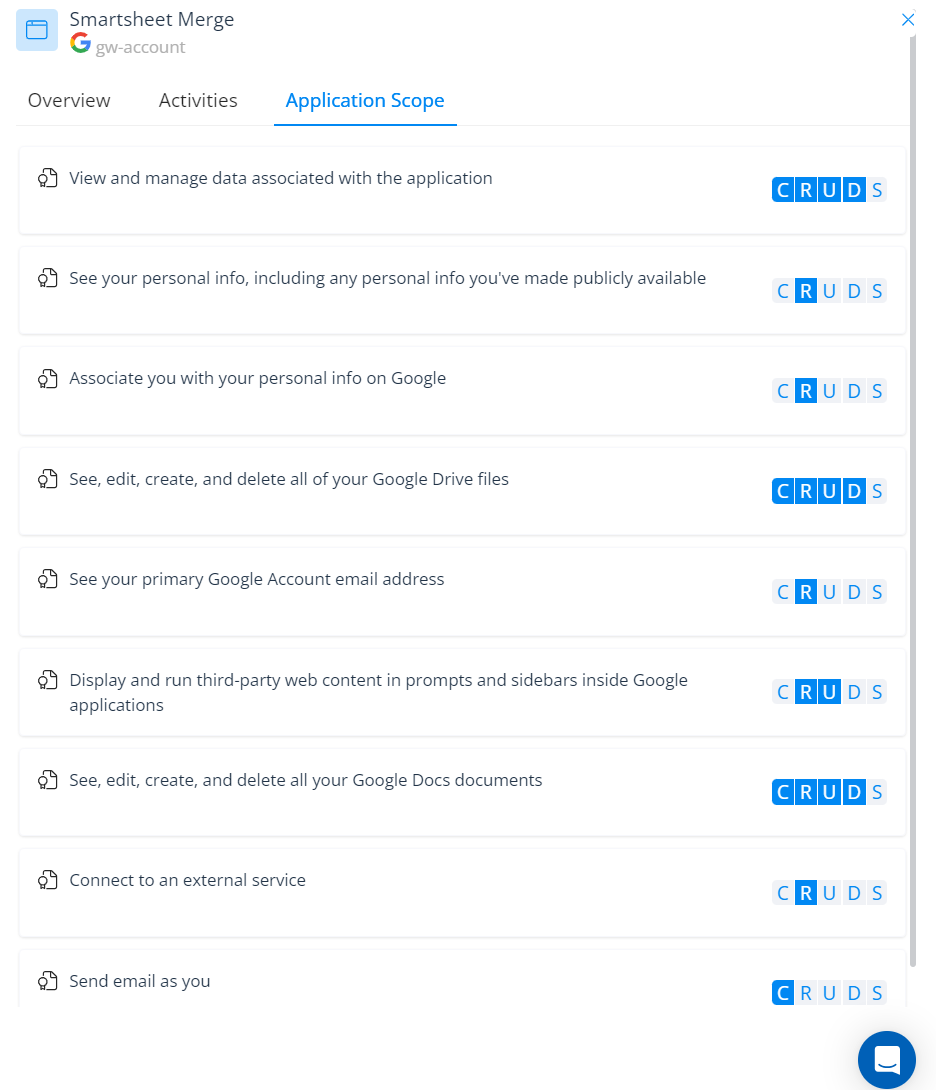
Get a clear understanding of each application's permission scope.
If you identify an application as a potential threat or are worried about its scope of permissions, you can revoke its access to your users or environment directly from the Varonis UI.
Revoke risky or stale third-party application assignments.
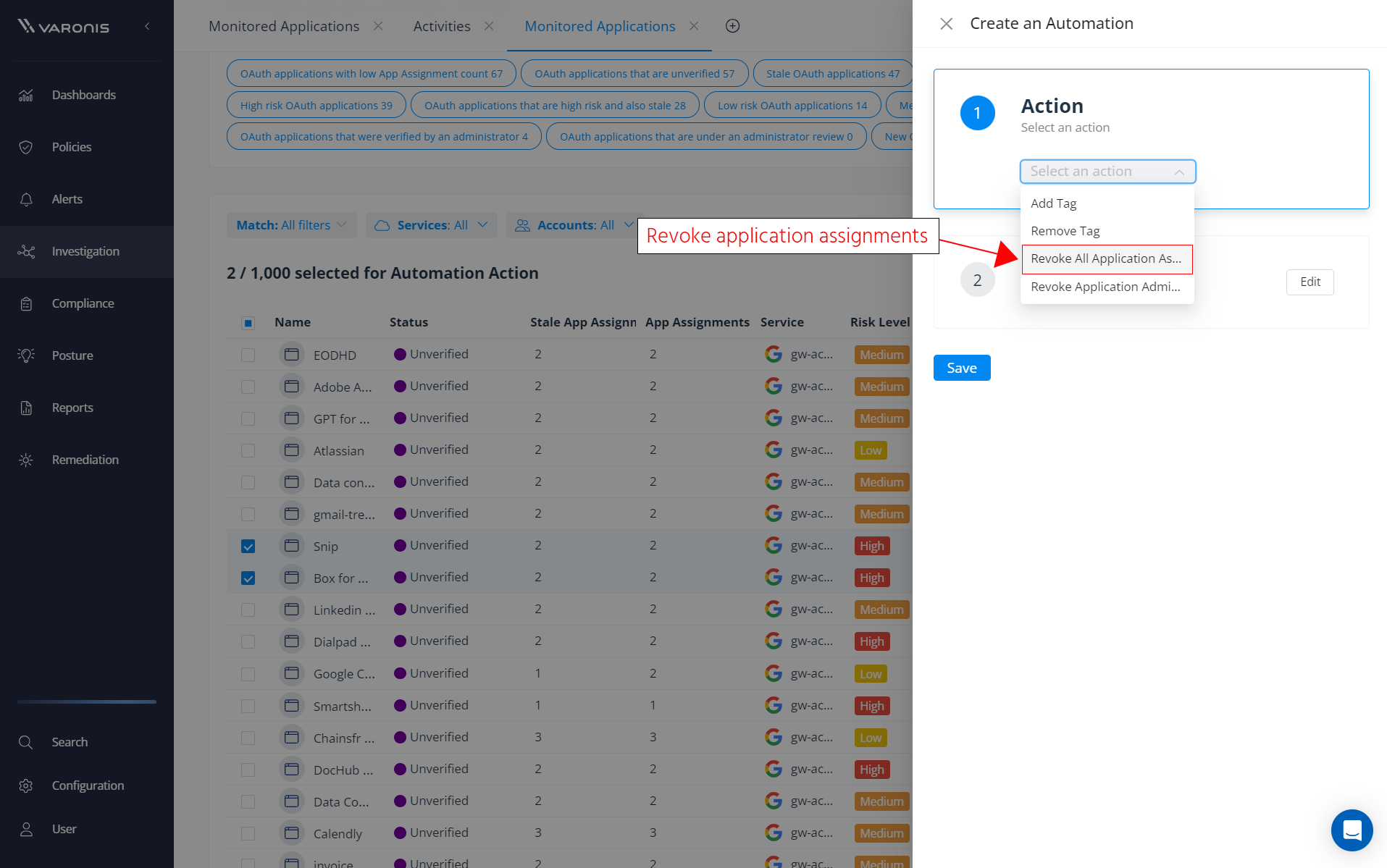
Revoke risky or stale third-party application assignments.
If you are a Dropbox Sign customer who is not currently using Varonis and wants assistance securing and monitoring your data from non-human identities, please reach out to our team.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.








