On May 22, 2025, Commvault’s Metallic SaaS platform — used for Microsoft 365 backups — was compromised via a zero-day vulnerability (CVE-2025-3928) in its web server. The flaw allowed authenticated attackers to deploy web shells and access client secrets stored by Commvault, enabling unauthorized entry into customers’ Microsoft 365 environments.
Recommended Actions:
- Credential Rotation: Immediately rotate application secrets managed by Commvault.
- Audit Logs: Review Microsoft Entra audit logs for unauthorized changes or sign-ins.
- Access Controls: Implement conditional access policies restricting authentication to approved IP addresses.
- Least Privilege: Reassess and minimize permissions granted to service principals.
- Patching: Apply the latest patches provided by Commvault to address CVE-2025-3928 if you self-host the Metallic web server.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) linked the breach to a broader campaign targeting SaaS applications with default configurations and elevated permissions. Although only a small number of customers were directly affected, the incident underscores the risks of overprivileged service principals and third-party credential storage.
Third-Party Risk and Supply Chain Exposure
This breach is a case study in SaaS supply chain risk: even if your internal security is strong, your vendors' weaknesses can become your problem. The attackers exploited Commvault’s vulnerable platform to breach Microsoft 365 environments, underscoring the need to scrutinize not just what a product does, but how it’s built and secured.
JPMorgan’s open letter to suppliers puts it plainly — secure-by-design practices and certifications like FedRAMP, SOC 2, and ISO 27001 should be table stakes. Cybersecurity buyers need to treat vendor risk like internal risk, because in practice, there’s no difference.
Attribution
According to multiple sources, including CISA, the breach has been attributed to a Chinese state-sponsored threat actor known as Salt Typhoon (also referred to as Silk Typhoon). The group is known for targeting U.S. critical infrastructure and cloud software vendors.
The campaign is part of a broader trend of software supply chain attacks aimed at exploiting trust relationships between enterprises and their SaaS providers.
How Varonis protects against these risks
The Commvault incident illustrates the interconnectivity between SaaS services and why it’s critical to have comprehensive visibility and control across your SaaS and cloud estate.
Varonis helps you map your third-party risk, including the apps, service principals, tokens, secrets, and keys that unlock access to your critical SaaS and cloud data.
In addition to mapping the identities, we also connect them to the data they can access so you can fully understand—and reduce—your third-party blast radius and prevent privilege escalation and lateral movement when upstream vendors are compromised.
Varonis continuously monitors for suspicious activity across Microsoft 365, Entra ID, and other cloud services, flagging and blocking abnormal behavior like service accounts accessing atypical sensitive data.
Backup Service Events in Varonis
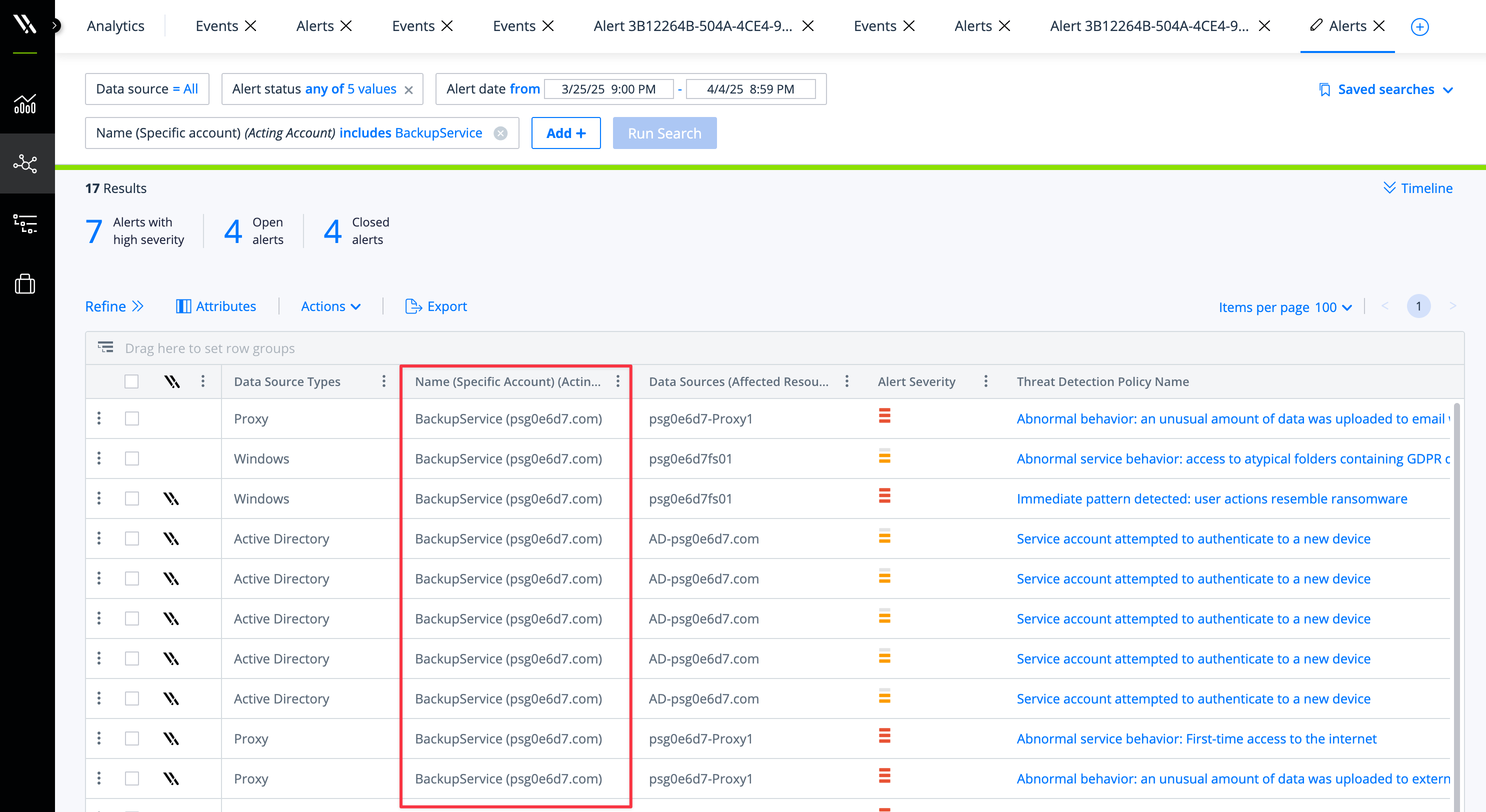
Backup Service Events in Varonis
When our Managed Data Detection and Response team became aware of the Commvault 0-day, we immediately identified our customers’ M365 tenants with the relevant service principal, performed a proactive threat hunt for IOCs, and reached out with mitigation advice.
Indicators of Compromise (IOCs)
CISA and partners identified the following IOCs associated with this activity:
- Web shell filenames: aspx, default.aspx, shell.aspx
- IP addresses: 51.100.23, 203.0.113.77
- Suspicious user agents: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:50.0) Gecko/20100101 Firefox/50.0
- Domain names used for callback traffic: cloudsyncsvc[.]net, metabackup[.]org
Full list of IOCs is available in CISA’s advisory: CISA Advisory
Threat Intelligence Sources
- CISA Alert AA25-143A
- BankInfoSecurity Coverage
- Cyble Research Blog
- CSO Online
- Varonis Threat Labs: Salt Typhoon
This breach highlights the importance of securing machine identities, vetting the security posture of every SaaS vendor, and enforcing strict access controls within modern cloud ecosystems.
If you need assistance with this incident — or any incident — don’t hesitate to contact us.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.







