Digital payments are expected to reach an all-time high this year. Projections have digital payment transactions increasing by upwards of 24 percent in 2020 year-over-year, a trend that shows no signs of slowing down. That’s precisely why PCI DSS requirements are more critical than ever, as merchants and payment processors need to ensure the privacy and security of every transaction.
The Payment Card Industry Data Security Standard (PCI DSS) is a framework designed to protect the entire payment card value chain. PCI DSS compliance requirements cover myriad areas, from how cardholder data is stored to how private payment data can be accessed.
But as threats and technology evolve, so do PCI DSS standards. Merchants, payment facilitators, and any other business that handles cardholder data should be aware of the new PCI DSS 4.0 requirements. Our PCI DSS 4.0 compliance checklist is here to help you decipher changes from data encryption to network security and monitoring.
- Overview: PCI DSS Compliance
- 12 PCI DSS Requirements Step-By-Step
- PCI DSS Compliance Checklist
- The Future of PCI Compliance
Get a Free Data Risk Assessment
Overview: PCI DSS Compliance

PCI DSS compliance is a privacy law and organizational requirement for any business that stores, processes or transmits cardholder data.
Here are the high-level goals that the PCI Standards Security Council are setting forth for PCI v4.0:
- Ensure that PCI standards continue to meet the security needs of the payments industry
- Add the flexibility and support of other methodologies to enhance payments security
- Promote cardholder security as a continuous process, merging security with business processes.
- Enhanced validation methods and procedures to streamline the compliance process.
Below are the technical areas that are being considered for modification under PCI DSS 4.0:
- Authentication and password guidance
- Advanced system monitoring requirements
- Additional guidance on multi-factor authentication
In short, PCI DSS 4.0 is designed to further secure cardholder data by helping organizations take a more holistic view of security measures and access controls. In addition, to respond to new threats posed by advances in technology.
12 PCI DSS Requirements Step-by-Step
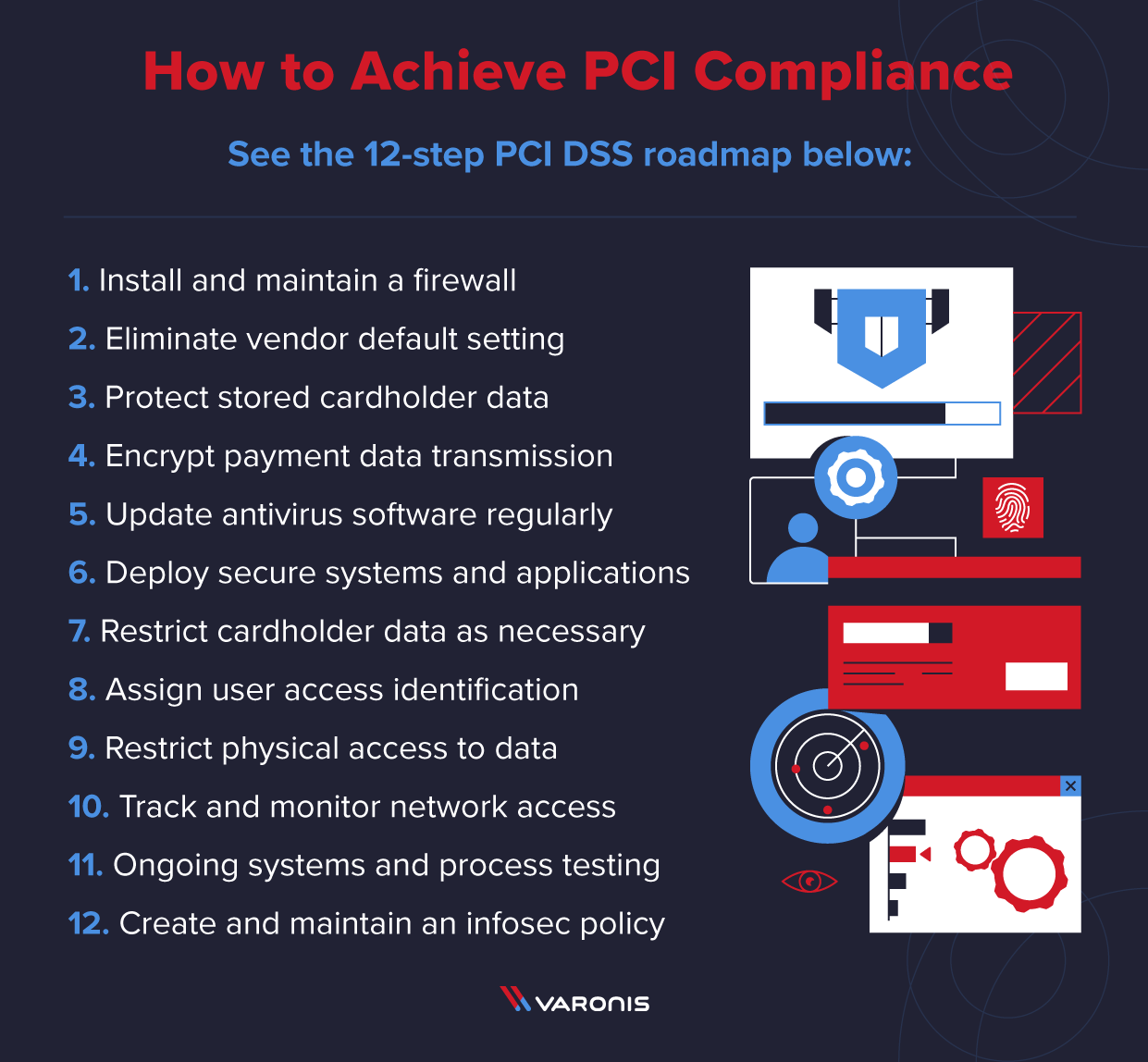
PCI DSS is the roadmap you need to follow to become PCI compliant. PCI DSS is a 12-step plan to protect customer data — see them laid out below step-by-step.
Step 1. Install and maintain a firewall
Meeting the PCI DSS firewall requirements is the first step towards organizational compliance. Firewalls restrict incoming and outgoing network traffic and are often the first line of defense when it comes to hackers.
You’ll need to properly configure your firewall and routers to protect your payment card data environment. Also, establish firewall and router rules and standards that determine which types of traffic are allowed and which aren’t.
Step 2. Eliminate vendor default setting
Never rely on the default settings for any servers, network devices, or software applications. This goes for everything from wifi routers to firewalls. The password, username, and other default security settings are often insufficient to me PCI standards.
This second PCI DSS standard requirement states that you not use vendor-supplied defaults for passwords and other security parameters. Make sure to upgrade your settings for all new devices and hardware, as well as maintain documentation for your configuration security hardening procedures.
Step 3. Protect stored cardholder data
Safeguarding cardholder data is the most critical of all PCI DSS compliance requirements. You need to know where cardholder data is going, the location it will be stored, and for exactly how long. Plus, all cardholder data must be encrypted using industry-accepted algorithms and security keys.
One common mistake is when companies aren’t aware that the primary account numbers (PAN) are stored in an unencrypted fashion. That’s why using a card data discovery tool is useful. This PCI requirement also includes rules for how card numbers should be displayed, such as hiding all but the first six or last four digits.
Step 4. Encrypt payment data transmission
This PCI DSS requirement step is similar to the previous one, only it focuses on data traffic and transmission rather than storage. This includes data-in-motion via open, closed, private, or public networks. Hackers often target data as it’s going from one location to another because they assume it’s more vulnerable.
You should know where cardholder data is going to and coming from, whether it be a merchant, payment gateway, or payment processor. Also, make sure to encrypt cardholder data prior to transmission using secure versions of protocols that will reduce the risk of moving data being compromised. You should be aware that PCI DSS v4.0 will provide more specific guidance on multi-factor authentication (MFA).
Step 5. Update antivirus software regularly
It’s not enough to simply install basic antivirus software to be PCI-DSS compliant. You need to update and patch your antivirus software applications on a regular basis. This PCI security standard is designed to guard against malware and any number of viruses that could compromise your systems and cardholder data.
Antivirus software should be up-to-date throughout your entire cardholder information technology ecosystem. This includes servers, workstations, and laptops or mobile devices used by employees and/or management. Antivirus software should always be actively running, using the latest signatures, and generating logs that can be audited.
Step 6. Deploy secure systems and applications
Next, you’ll need to define and implement processes to both identify and classify risk for the sake of technology deployment. Without first conducting a thorough risk assessment, it’s impossible to manage and utilize technology in compliance with PCI standards.
After a risk assessment, you can then begin rolling out equipment and software used in processing or handling sensitive payment card information. Don’t forget to also apply patches in a timely manner, also a PCI DSS standard requirement. This includes patches for items like databases, point-of-sale terminals, and operating systems.
Step 7. Restrict cardholder data as necessary
Any entity that handles payment card data must also allow or deny access to said data based on roles and permissions. More specifically, PCI DSS requirements state that individuals should only have access to private cardholder data on a need-to-know, business essential basis.
In addition to digital access, organizations must also meet PCI DSS physical security requirements. You should have documented access control policies and procedures based on things like job function, level of seniority, and reason for needing access to cardholder data. Document all users and their access level and keep it up to date at all times.
Step 8. Assign user access identification
Per PCI DSS standard number eight, every user should have their own unique, individual username and password access. Never — under any circumstances — employ group or shared usernames or passwords. Moreover, all unique usernames and passwords should be complex.
This isn’t just to prevent hackers from guessing or stealing passwords to enter the system. It also ensures that — in the event of an internal data breach — activity can be traced and tracked back to specific users with near 100 percent certainty. To bolster unique access even further, PCI DSS requirements state that you employ two-factor authentication.
Step 9. Restrict physical access to data
Being PCI compliant isn’t just about digital security. Companies must also take PCI DSS physical security seriously on their own. This PCI requirement covers physical access to things like servers, paper files or workstations that house or transmit cardholder data.
This PCI requirement also mandates the use of video cameras and general electronic monitoring of entry and exit ways of physical locations like file storage and data centers. Recordings and access logs must then be kept for a minimum of 90 days. You should have access processes to distinguish between employees and visitors. Finally, all portable media with cardholder data such as flash drives must be physically guarded and destroyed when it’s no longer necessary for business.
Step 10. Track and monitor network access
Malicious actors consistently target both physical and wireless networks to access cardholder data. That’s why PCI standards require all network systems to be protected and monitored at all times, with a clear history of activity to reference. Network activity logs should be kept and sent back to a centralized server to be reviewed daily.
You can use a Security Information and Event Monitoring (SIEM) tool to help log system activity, while simultaneously monitoring for suspicious activity. According to PCI compliance requirements, audit trail records of network activity must be kept, time-synchronized, and maintained for at least one year.
Step 11. Ongoing systems and process testing
Malicious actors and cybercriminals are constantly poking and prodding systems in hopes of discovering a vulnerability. That’s why PCI standards include requirements about continuous system and process testing. Activities like penetration and vulnerability testing can help you meet this requirement.
You’ll be required to conduct periodic wireless analyzer scanning on a quarterly basis to identify unauthorized access points. External IPs and domains need to be scanned by a PCI Approved Scanning Vendor (ASV) Internal vulnerability scans should be conducted quarterly as well. And a thorough application and network penetration test should take place annually.
Step 12. Create and maintain an infosec policy
The final step to becoming PCI compliant centers on organizational focus and cooperation. And that’s the creation, implementation, and maintenance of a company-wide information security policy. This infosec policy should cover employees, management, and relevant third parties.
Your infosec policy should be reviewed annually, disseminated to internal and third-parties with all users acknowledging and reading said policy. You’re also required to perform user awareness training and employee background checks to prevent the wrong people from accessing cardholder data.
PCI DSS Compliance Checklist
Before engaging a PCI Qualified Security Assessor (QSA), you’ll want to make sure you have as many items on the following PCI DSS compliance checklist complete:
1. Get your firewall up and running.
- Create a plan for firewall implementation and policy for changes or updates
- Monitor and test your firewall periodically to detect potential vulnerabilities
- Update your firewall with the latest patches and ensure overall maintenance
2. Upgrade settings from vendor default.
- Conduct an audit of default settings and accounts with any new hardware or software
- Adjust settings to address both common threats and internal vulnerabilities
- Maintain an inventory of all system components that all under PCI DSS for documentation
3. Protect cardholder data at all costs.
- Create a PCI compliant policy for how you’ll collect, handle and dispose of data
- Implement strong security measures like encryption and Personal Account Number (PAN) masking
- Document your process for creating, storing and managing cryptographic keys
4. Encrypt cardholder data-in-motion.
- Make sure you’re using strong encryption protocols in both private and public networks.
- Never send PANs with end-user messaging tech like email, instant messaging or SMS.
- Conduct regular employee training about PCI compliant data transmission best practices
5. Keep your antivirus software updated.
- Deploy antivirus software on all hardware and software, especially personal computers and servers
- Make sure that all antivirus software performs continuous monitoring and automatically generates logs
- Configure your antivirus software so that end users can’t adjust settings without managerial approval
6. Only deploy secure hardware and software.
- Enlist a PCI compliance partner to help vet new hardware or software to ensure it’s secure
- Install any vendor-specified updates or security patches within one month of release
- Develop any internal software applications with PCI compliance measures in mind
7. Put data access restrictions in place.
- Limit cardholder data access only to individuals who require it for business purposes
- Implement key cards, pass-codes and biometrics to strengthen physical access controls
- Train employees regularly on your cardholder access policy to avoid accidental internal breaches
8. Assign unique user IDs and passwords.
- Document processes and measures for creating, assigning and revoking user IDs
- Incorporate two-factor-authentication (2FA) for anyone logging into the system
- Eliminate any existing group user IDs or passwords. These are forbidden by PCI DSS
9. Secure key physical access areas.
- Monitor access to and from physical areas with cameras, CCTV or other surveillance
- Differentiate between onsite personnel and visitors using things like badges or name tags
- Destroy flash drives and other physical media storage devices once they’re no longer necessary
10. Watch and record network access.
- Establish a record of linkage for all physical network devices to specific users
- Automate the generation of audit trails for your network for documentation
- Regularly review your security logs to detect any anomalies or suspicious activities
11. Conduct regular penetration testing.
- Create a plan with a PCI pen testing partner to test vulnerabilities on a quarterly basis at minimum
- Ensure your penetration testing methodologies work at both the network and application levels
- Deploy a change-detection mechanism to perform weekly critical file comparisons
12. Formulate a clear infosec policy.
- Identify key stakeholders across all business units that should be involved in the policy
- Create and document your infosec policy with a PCI compliance partner
- Conduct annual staff training — at minimum — to ensure continuous policy implementation
Bear in mind that non-compliance with PCI requirements can result in severe consequences. If you experience a data breach — and subsequent investigations find that you were non-compliant — fines can range anywhere from $5,000 to $10,000 per month until you reach compliance. Not to mention the reputational damage of suffering a data breach because you didn’t take the PCI DSS recommended precautions.

The Future of PCI Compliance
Overall, PCI DSS v4.0 isn’t about significantly altering the six key goals and 12 requirements of PCI DSS. But what you can expect are adjustments in the methodologies and processes of PCI compliance assessments to keep up with new technologies in the financial technology and payments sector.
The goal is to make PCI DSS compliance more flexible, placing a greater emphasis on both technology and business processes. Sure, you may have firewalls and antivirus software installed, but how do those fit into your overall business processes?
You’ll want to continuously monitor the www.pcisecuritystandards.org FAQ section for published guides and additional information regarding PCI DSS v4.0. But if you’re just getting started along your PCI compliance journey, the best thing to do is go over the goals and requirements with key infosec personnel to determine what you’re compliant with and what you’re not.
After spotting the gaps, you’ll want to consider working with an experienced PCI compliance partner to help you fill in the gaps.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.




-1.png)



