Knowing the right tool to the right job is something that can save you hours of extra work and tedium. We’ve compiled a list of of some of the best general purpose sysadmin tools for troubleshooting, testing, communicating and fixing the systems that you need to keep running.
WireShark
Hate computers professionally? Try Cards Against IT.
Wireshark is the world’s foremost network protocol analyzer. It lets you see what’s happening on your network at a microscopic level. It is the de facto standard across many industries and educational institutions.
Wireshark is cross platform and works on OS X, Windows and Unix.
FileZilla
https://filezilla-project.org/
Filezilla is an GPL licensed FTP client and Server. It’s ability to connect to SSH secured hosts makes it a great choice if you need to give access to client more comfortable with GUI than CLI interfaces.
Fiddler
http://www.telerik.com/fiddler
Fiddler is a proxy server that is meant to run locally to allow for developers to debug web applications. If you have multiple different applications or processes that can modify the values in a form it’s great to be able to see the actual output as transmitted.
If you’re working with a remote API, you can also compose and replay requests as needed.
Sysinternals Suite
http://technet.microsoft.com/en-us/sysinternals/bb545021.aspx
The Sysinternals Suite is a collection of general sysadmin tools for file and disk, networking, process management, security and collecting system information on Windows hosts.
One of the most popular and immediately beneficial utility is Autoruns.exe which will identify programs that start automatically.
Mosh
SSH users will be familiar with the frailty of their remote sessions, a single wifi hiccup and they go down. Mosh is a secure replacement protocol that allows for the resumption of sessions as well as generally improved performance. Mosh is available for almost every platform, including a Chrome plugin for even more portability.
Autossh
http://www.harding.motd.ca/autossh/
Designed more for SSH tunnels than interactive sessions, Autossh will restart dropped SSH sessions and tunnels.
If you’d like a perpetual session, use with “screen”.
Clonezilla
If you’re administering or provisioning a larger number of computers, it is very beneficial to create a master image and then push it to all of the target machines, which is exactly what the open source Clonezilla does.
The multi-cast feature of Clonezilla SE let you update machines in massive parallel batches.
Clusto

https://github.com/clusto/clusto
A python based server cluster management tool, Clusto lets you maintain an abstracted interface for interacting with your infrastructure.
Clusto stores data in any database that you can interact with via SQLAlchemy, easing your management as you can get started with anything you have in place.
Ansible
Ansible bills itself as the simplest way to automate IT provisioning tasks.
Ansible Playbooks are the programmatic method of bundling instructions to be run, which you can then replay on any number of servers you’re connecting to over SSH.
Chef
Chef helps automate your server infrastructure via Chef clients installed on each node in your network. Periodically the clients poll the central Chef server and check their internal config against the instructed configuration – if discrepancies are found it then runs the commands to bring them into compliance.
Chef’s constant compliance checking is very helpful in quickly recovering if manual changes are made by sysadmins.
Puppet
Puppet allows for declarative configuration of servers via their ruby DSL. If you already know ruby it’s easy to dig into Puppet and manage any number of servers.
If you want to get an easy taste for Puppet, they offer a preconfigured VM that you can play around with.
Dnsmasq
http://www.thekelleys.org.uk/dnsmasq/doc.html
Dnsmasq is a much lighter weight DNS resolver for local networks than BIND, or other ‘heavyweight’ servers. It is ideally suited for use in low resource environments like routers and firewalls.
It caches requests locally but falls back to an upstream DNS provider.
Bugzilla
Primarily used to report and process software bugs, Bugzilla has expanded to allow for quality assurance management and the submission and review of patches.
Buzilla integrates with many source control systems, letting you setup two way communications so that you can close bugs with commits, etc.
Sysdig
Sysdig is an open source, system level management tool. It lets you capture, filter and save the different processes that are active within a Linux machine at any given point.
Sysdig makes some common tasks, like tracking any file opened in a directory in real time trivially easy.
Lua scripts can be used to modify and extend the core Sysdig functionality.
TreeSize

http://www.jam-software.com/treesize_free/
Treesize is a NTFS file space viewer that helps visualize space usage in a Windows Explorer like view.
Treesize works off of the Master File Table of the target machine, letting you read results faster and without the need for content read permissions.
7-Zip
An open source windows compression utility. 7-zip works extremely fast on even very large zip files and can produce self extracting archives in the 7z format.
Notepad++

http://notepad-plus-plus.org/download/
An excellent Open Source Windows text editor with regular expression support, syntax highlighting and a tabbed interface.
If you’re moving between machines, checkout Notepad++ Portable which you can run from a share or a USB drive.
KeePass
An opensource password manager, KeePass lets you generate strong random passwords per site or application. Stored securely, KeePass lets you maintain secure passwords without have to remember hundreds of 20 character plus password or even worse – writing one down.
If you need to share your password file with others, or access it from multiple locations, keep it on a DataAnywhere share.
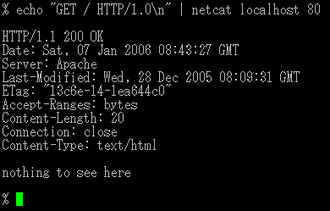
Netcat
http://netcat.sourceforge.net/
Often described as the ‘swiss-army’ knife of network utilities, netcat is tremendously useful for anything dealing with sending or receiving network port information.
Example: if you need a one-shot webserver on port 8080
{ echo -ne "HTTP/1.0 200 OK\r\nContent-Length: $(wc -c <some.file)\r\n\r\n"; cat some.file; } | nc -l 8080
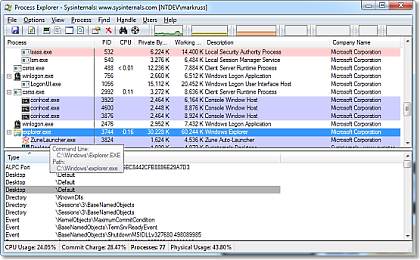
Process Explorer
http://technet.microsoft.com/en-us/sysinternals/bb896653.aspx
Track, identify, start and stop processes that need manipulation on a Windows machine. Additionally, it is a great way to track down memory leaks and find rogue processes.
ADModify.NET
https://blogs.technet.microsoft.com/exchange/2004/08/04/admodify-net-is-here/
ADModify.NET is a tool primarily utilized by Exchange and Active Directory administrators to facilitate bulk user attribute modifications.
What should I do now?
Below are three ways you can continue your journey to reduce data risk at your company:
Schedule a demo with us to see Varonis in action. We'll personalize the session to your org's data security needs and answer any questions.
See a sample of our Data Risk Assessment and learn the risks that could be lingering in your environment. Varonis' DRA is completely free and offers a clear path to automated remediation.
Follow us on LinkedIn, YouTube, and X (Twitter) for bite-sized insights on all things data security, including DSPM, threat detection, AI security, and more.




















-1.png)
