Insider Risk Management
- Cross-cloud
- Real-time
- Automated






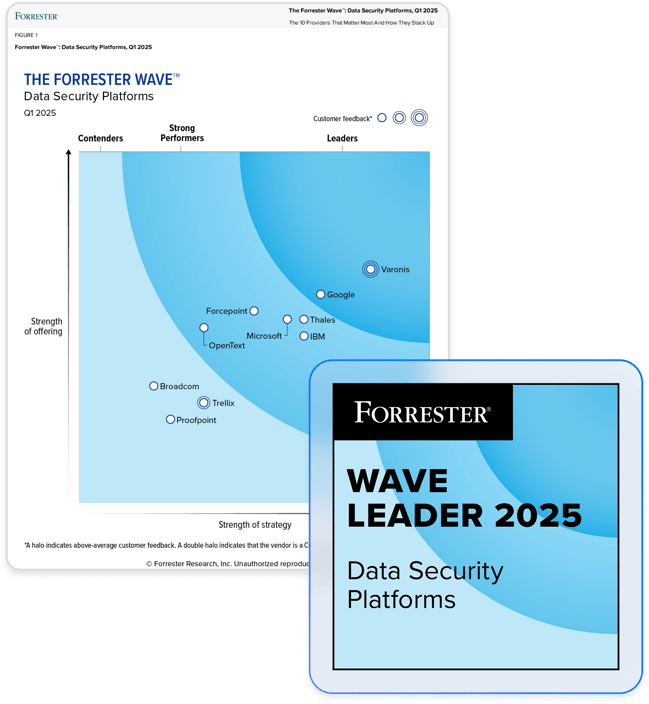
Partner with a leader in data security.
Protect your data from insider threats.
Proactive Monitoring
- Alert on abnormal behavior
- Automate response
- Get 24x7x365 MDDR support
Searchable Forensics
- Respond to file access events
- Triage privilege escalation
- Investigate suspicious activity
Permissions Remediation
- Identify over-permissioned users
- Revoke risky entitlements at scale
- Minimize insider blast radius
Varonis has meant a lot for our organization. They were able to detect an incident that happened in our environment where other tools that we had in place did not detect it.
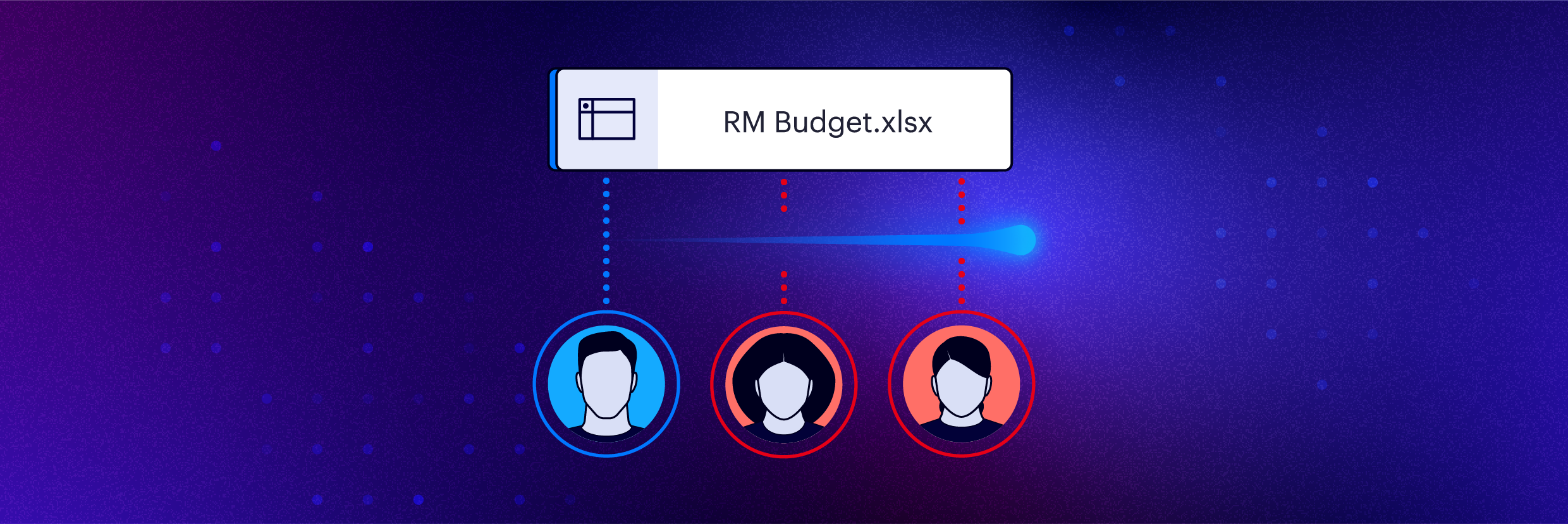
Least privilege automation
Managing insider risk starts with intelligent decisions about who needs access to data and who doesn’t. Varonis continually reduces your blast radius without human intervention and automates permissions management at scale.
Data activity auditing
Varonis detects insider threats by continuously monitoring key indicators of compromise. Hundreds of threat models automatically detect anomalies and alert you to abnormal activity like unusual file access, permissions changes, removing labels or protections, and much more.
Continuous risk assessment
Varonis provides a real-time view of your data security posture by combining file sensitivity, access, and activity. From shared links to nested permissions groups, we calculate effective permissions and prioritize remediation based on risk.
Proactive monitoring and investigation
Our team of cybersecurity experts monitors your data for threats, investigates alerts, and only surfaces incidents that require your attention – saving your team time and hardening your security defenses.
Our customers have spoken
One platform for multi-cloud, SaaS, and on-premises data.
Varonis protects enterprise data where it lives — in the largest and most important data stores and applications across the cloud and behind your firewall.
Insider Risk Management Resources
Go beyond Insider Risk.
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital