Varonis for Active Directory
Varonis helps you find and fix AD misconfigurations that hackers commonly exploit to gain access, move laterally, persist, and ultimately steal your data.
- Misconfigs
- Monitoring
- Alerting






Partner with the leader in data security.
Identity threat detection and response (ITDR)
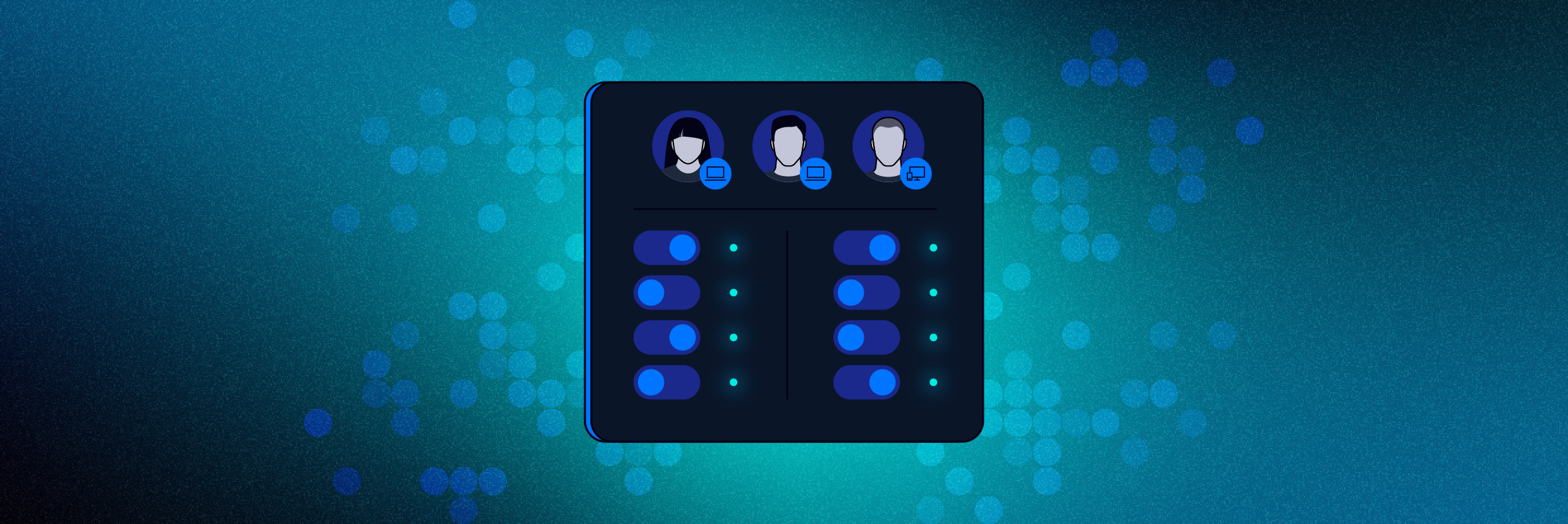
Track and improve your AD security posture.
Get real-time awareness of your top AD risks and attack paths such as admins with SPNs and accounts vulnerable to pass-the-ticket attacks. Untangle complex domains, close your gaps, and reduce risk.
Monitor Active Directory and Entra ID events.
By correlating AD events with data access and network activity, Varonis can spot behavioral anomalies like a service account accessing sensitive data for the first time.
Get AI-powered threat detection with 24x7 coverage.
Varonis uses machine learning to develop user behavior profiles and baselines for every user and device in your environment. Add MDDR to unlock a global team that will investigate and respond to your alerts 24x7x365.
"Varonis alerts us to authentication anomalies, permission modifications, administrator group changes—anything suspicious that’s happening within our Active Directory."
Senior Admin, Major Healthcare Technology Provider
Read case studyVaronis solves common Active Directory security challenges.
Kerberoasting, ticket attacks, password sprays
- Varonis has many expert-built threat models to detect common AD attacks
- Detect and respond to Kerberoasting and delegation attacks
- Identify and fix accounts and configurations that make you vulnerable to password sprays, credential stuffing, and other brute force attacks
DCSync and DCShadow attacks
- Varonis has built in threat models designed to catch both DCSync and DCShadow attacks
- No custom rule-writing or static detections required
- Trigger automated actions in response to AD attacks and/or send alerts to your SIEM/SOC/SOAR
Changes to GPOs and DC settings
- Varonis tracks all changes to group policies, users, computer accounts, password settings and much more
- Full audit log of all changes performed in AD with who, what, when, where details
- Setup alerts to be notified of changes outside of change control windows, changes to privileged accounts and groups, password resets, and more
One platform for multi-cloud, SaaS, and on-premises data.
Varonis protects enterprise data where it lives — in the largest and most important data stores and applications across the cloud and behind your firewall.
Active Directory security resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital