Data Discovery and Classification
Accurately classify your data and get deep visibility across your environment with the combination of AI and sophisticated pattern matching.
- Complete
- Current
- Contextual






Varonis Named a Customers' Choice in Gartner® Peer Insights™ Voice of the Customer DSPM Report
Accurate discovery and classification at scale.
Scan everything, everywhere
- Structured databases and data warehouses
- Unstructured data in files, folders, and buckets
- Semi-structured data in SaaS apps and email
Reduce your data risk
- Find and fix exposed data
- Eliminate stale sensitive data
- Monitor and alert on suspicious activity
Auto-enforce labeling and DLP policies
- Automatically apply missing labels
- Automatically fix incorrect labels
- Better enable encryption and masking
The confidence that I have in the data classification engine and its ability to recognize sensitive data is outstanding.
Julia Bruce
Automatic data discovery
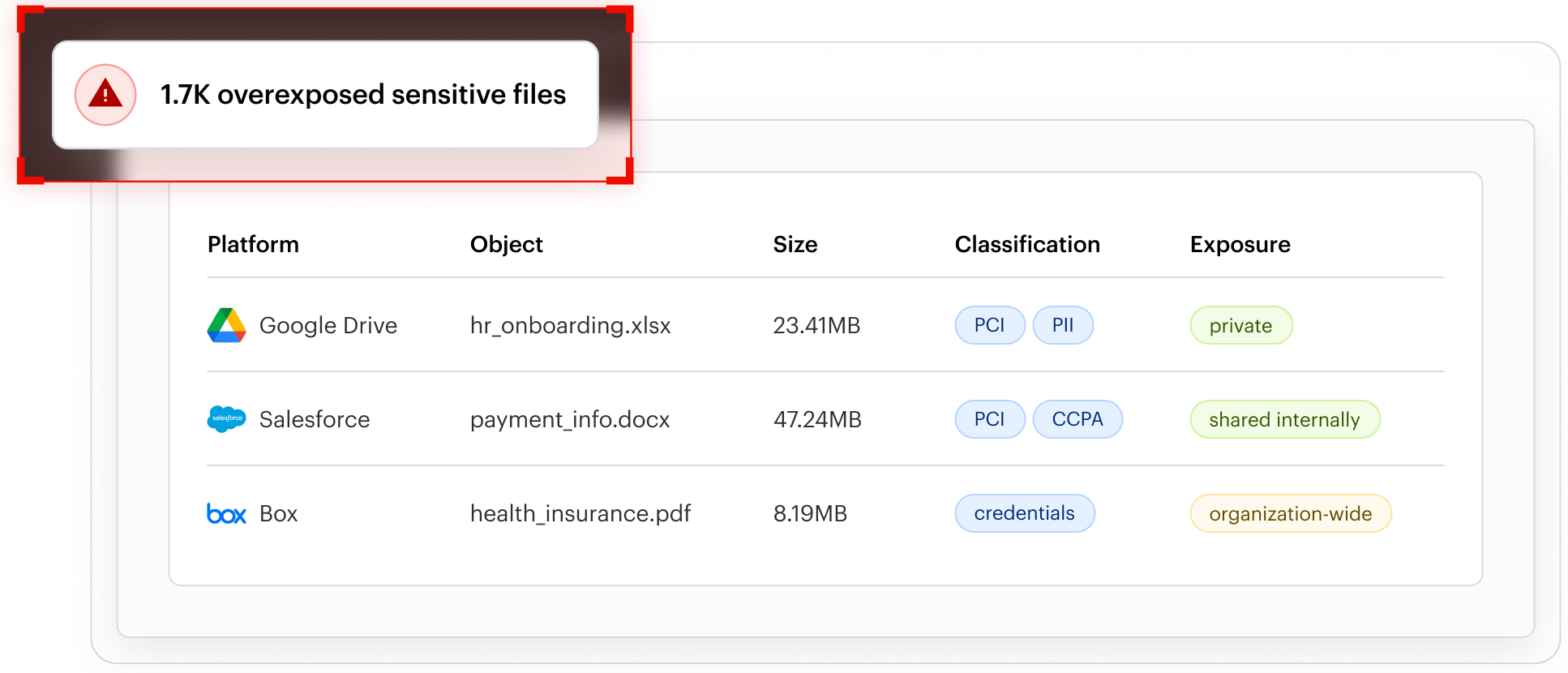
Accurate data classification
Classify your data at scale with 99% accuracy with the combination of sophisticated pattern matching and AI. Classify PII, PCI, PHI, passwords, secrets, and tokens with reduced false negatives and false positives with minimal training. Confirm findings with file analysis to show exactly where classification results appear within a document.
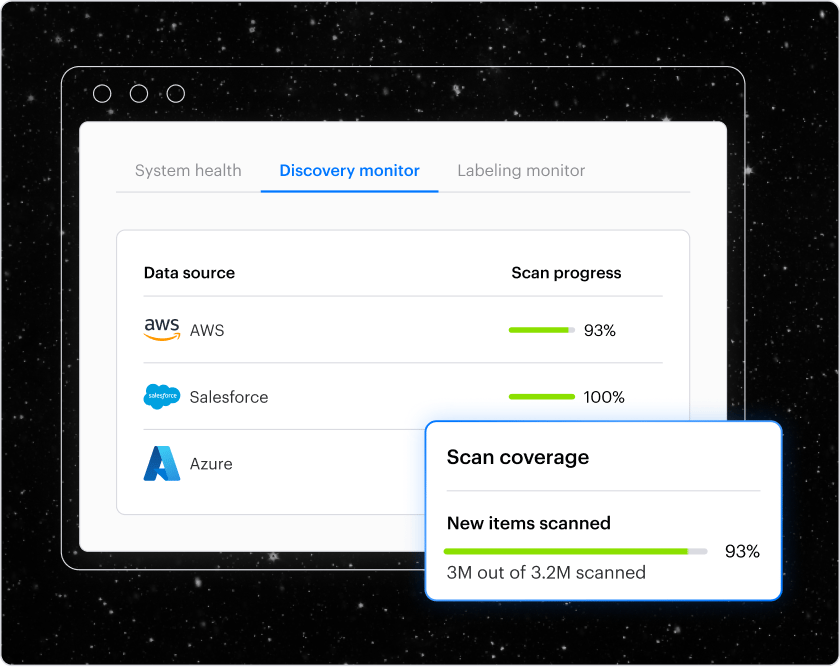
Enhance labels for improved DLP
Create granular policies, automatically fix manual gaps, and re-label files as your data changes to make downstream DLP controls more effective with accurate and actionable labels. Varonis fully integrates with MPIP to enhance Microsoft's native classifications.
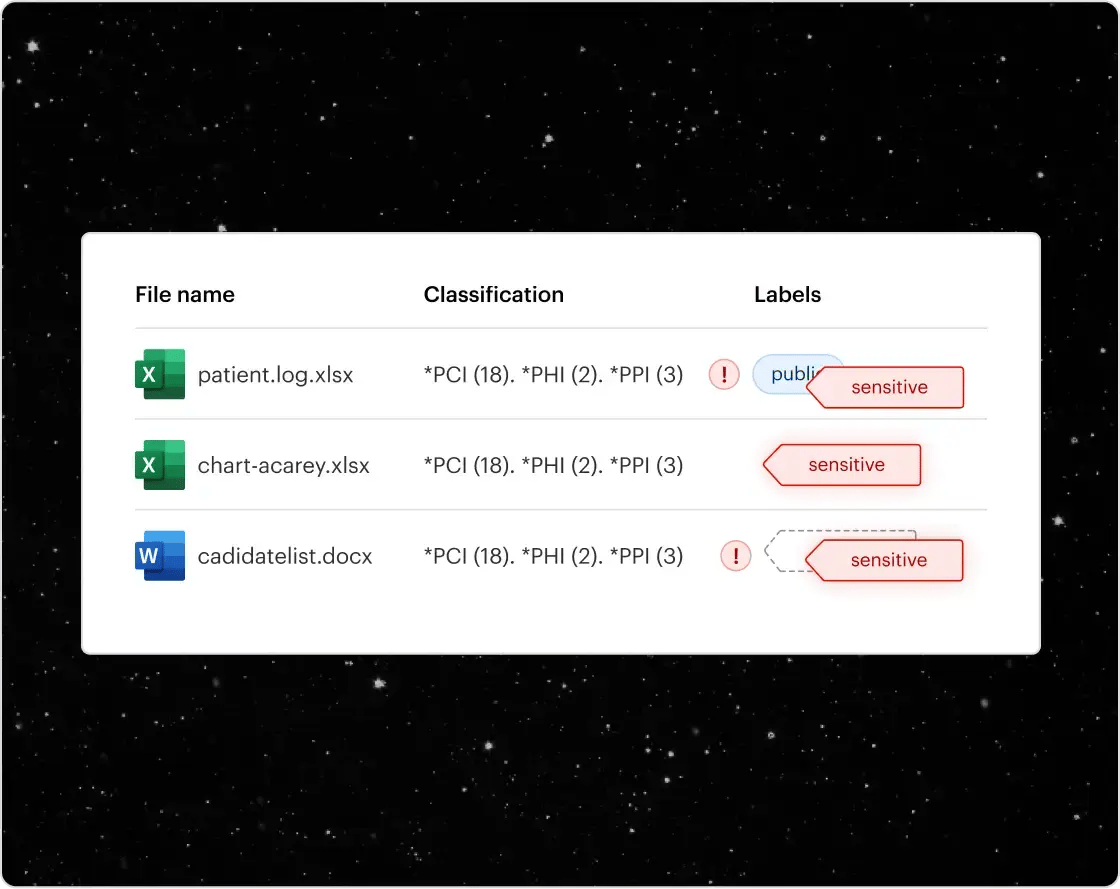
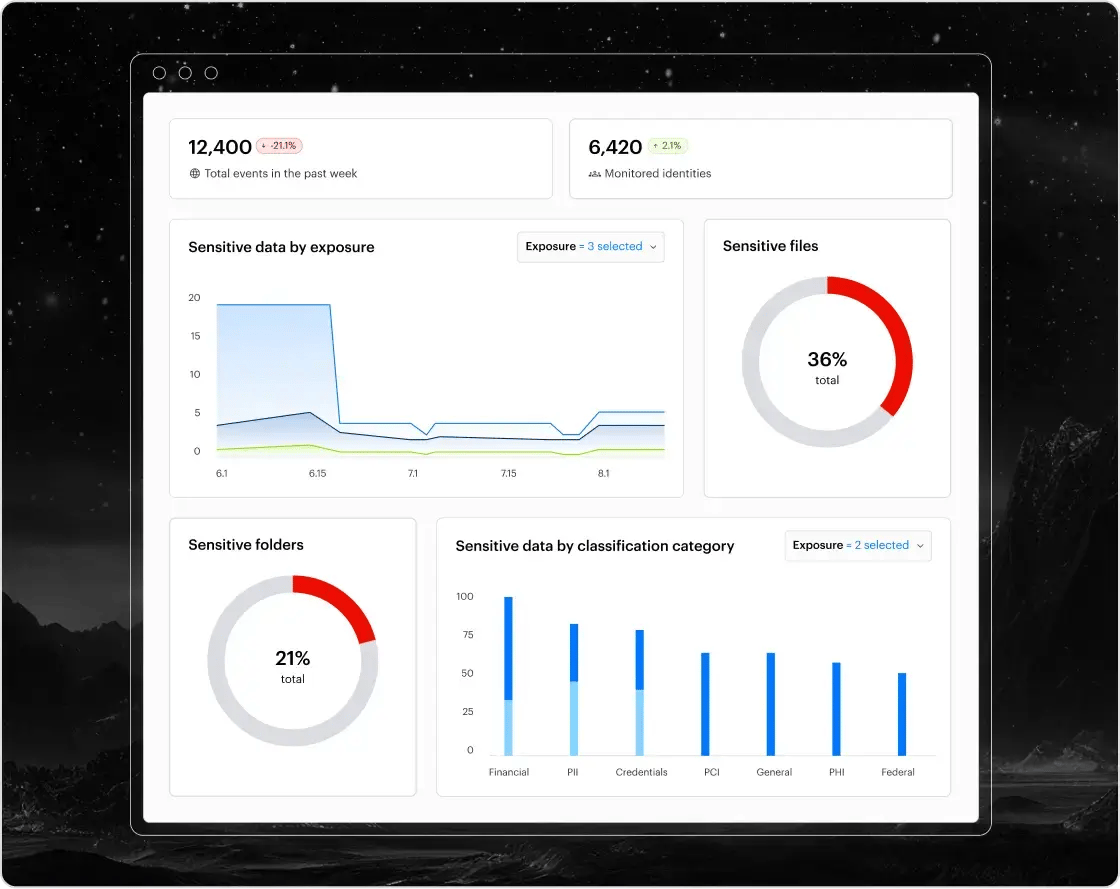
A comprehensive data inventory
Varonis creates a comprehensive record of your sensitive data that goes in-depth down to the file-level. Easily understand your concentrations of sensitive by type, like PII, PCI, PHI, and prioritize based on exposure, activity, density, metadata, size, and staleness.
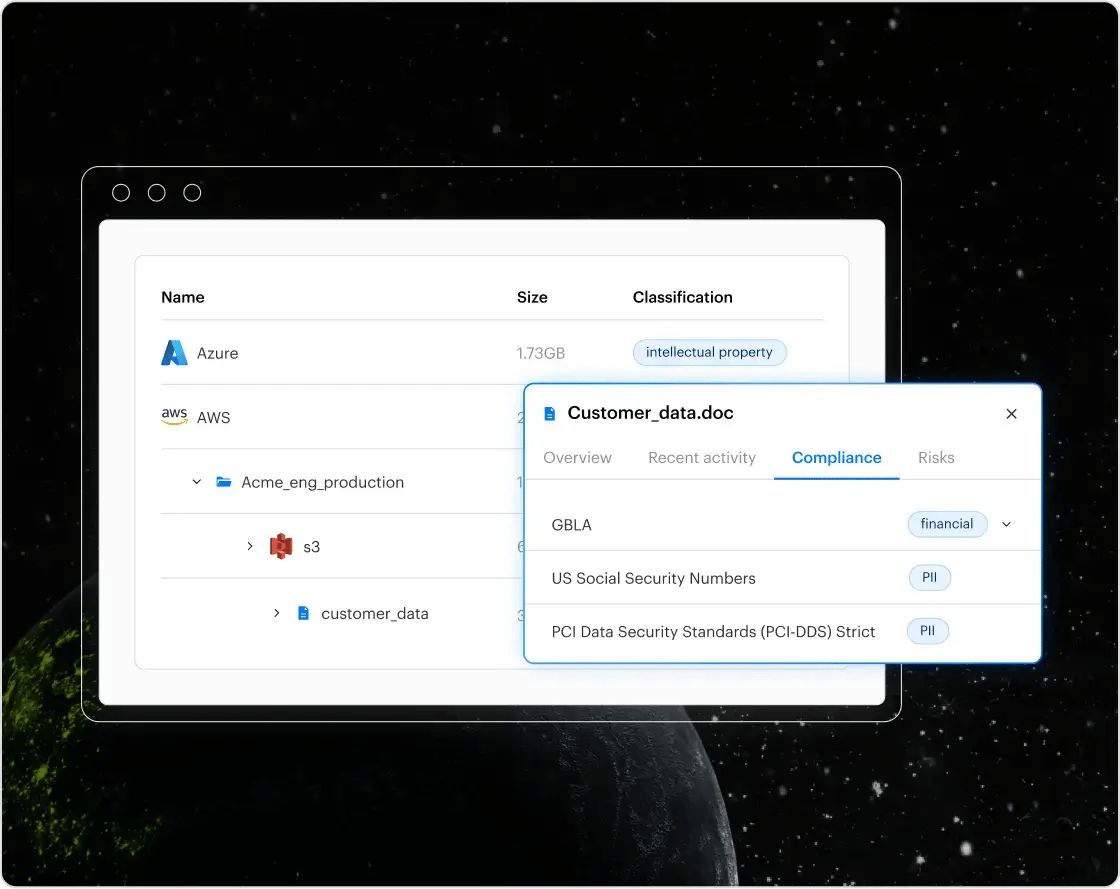
Efficient e-discovery
Our privacy automation capabilities, backed by a specialized search engine, empower you to efficiently locate files with personal information across cloud and on-prem data stores. Easily filter and share with legal or compliance teams.
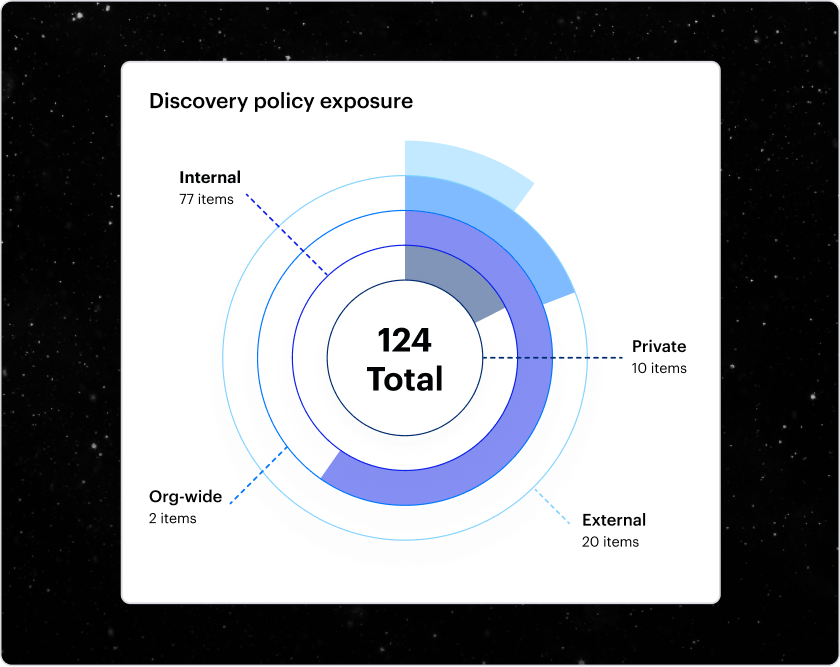
Scalable scanning
Varonis discovery scans are always current no matter how much data you have. With incremental scanning, we detect when files are created or changed and scan exactly what need to be scanned.
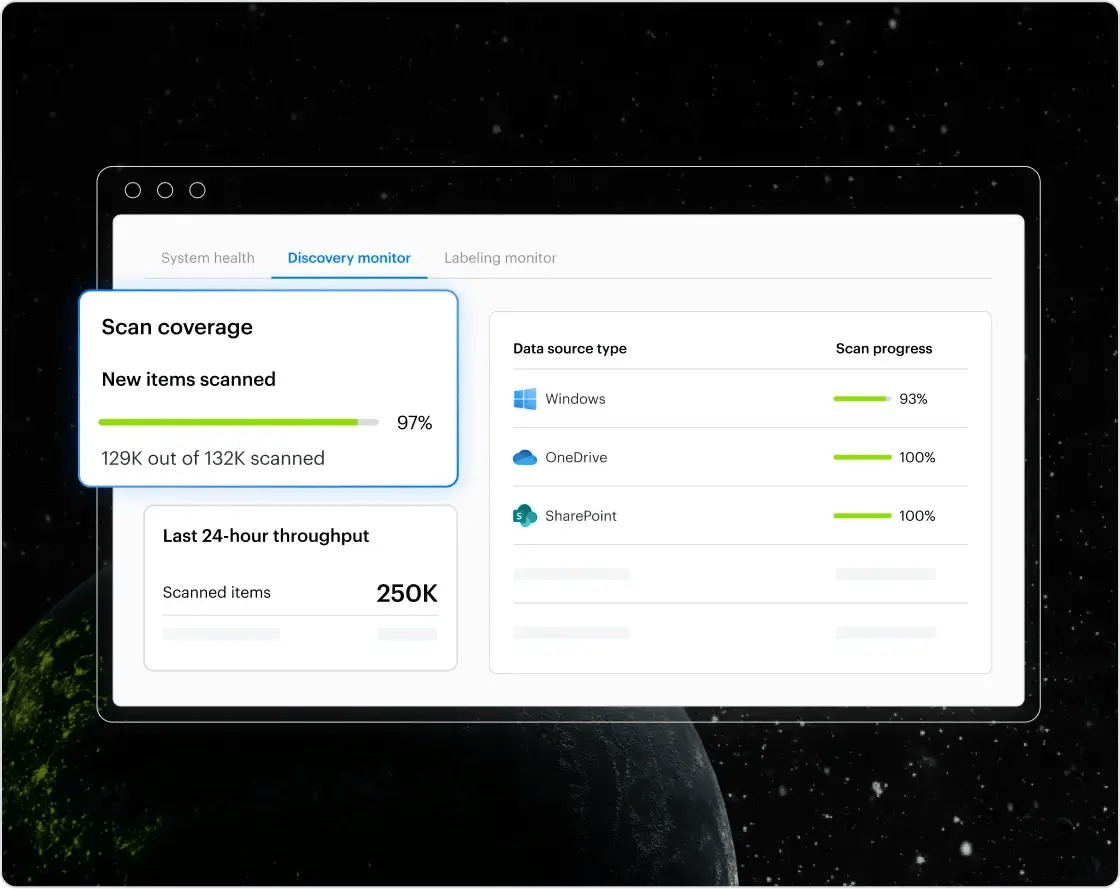
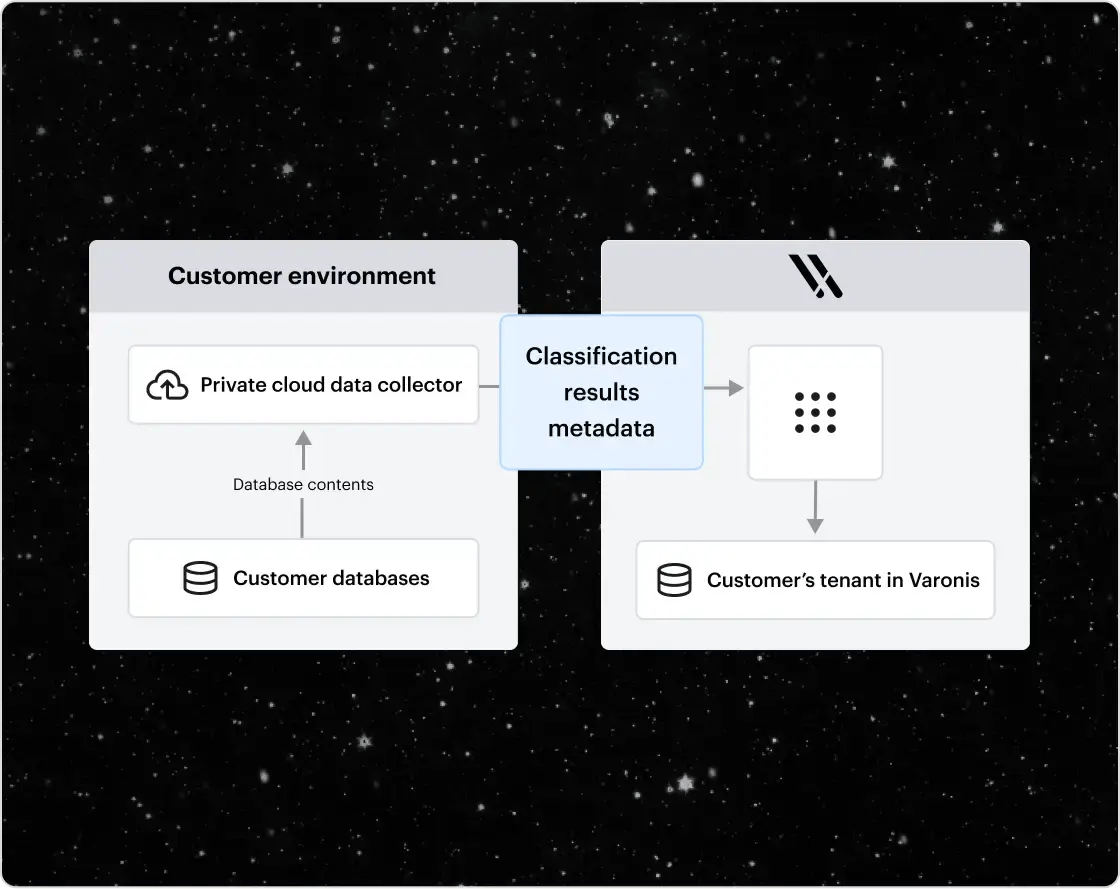
Local scanning and data sovereignty
Varonis AI models are computationally efficient enough to run on local compute, reducing costs and ensuring that your data doesn’t need to leave your environment to be scanned.
Our customers have spoken
One platform for multi-cloud, SaaS, and on-premises data.
Varonis protects enterprise data where it lives — in the largest and most important data stores and applications across the cloud and behind your firewall.
Data Discovery and Classification Resources
Go beyond Data Discovery and Classification.
Varonis tackles hundreds of use cases, making it the ultimate platform to prevent data breaches and ensure compliance.
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital