Varonis for SaaS
Easily monitor your SaaS applications to surface sensitive data, stop malicious insiders, and investigate cross cloud cyber threats with Varonis.
- SSPM
- DSPM
- Agentless






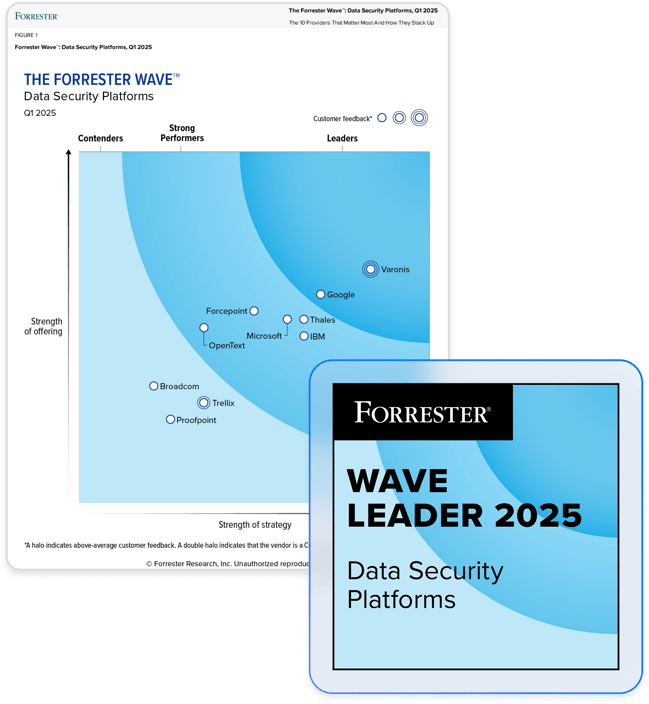
Partner with the leader in data security.
Unified visibility and control for all your SaaS apps.
Identify sensitive data in hiding in your SaaS apps.
Automatically discover where sensitive data might be lurking in apps such as Salesforce, GitHub, Google Drive, and Box. Varonis looks inside objects and files to find sensitive information matching hundreds of classification patterns and vigorously prioritizes remediation based on exposure.
Enforce least privilege across apps.
Varonis makes intelligent decisions about who needs access to data and who doesn’t — highlighting users that have more access than they need. Create policies to continually reduce your blast radius without human intervention and without breaking the business.
Control third-party API and app risk.
Varonis discovers and monitors all the third-party apps or APIs connected to your SaaS platforms. Reduce your attack surface by removing unsanctioned or unused apps directly from a single console.
Detect and fix SaaS misconfigurations.
Varonis finds and fixes misconfigurations and toxic combinations that put your data or organization at risk. We'll spot risks such as changes to admin accounts, privilege escalation attempts, missing MFA, and default credentials to continually reduce your blast radius.
Stop malicious insiders and attackers.
Varonis offers hundreds of built-in threat models and customizable rules to detect and stop suspicious behavior like excessive data access, data exfiltration attempts, and identity abuse across your SaaS environments.
Investigate cross-cloud threats.
Varonis tracks user and entity activity across your different SaaS and IaaS environments in a single standardized audit trail of events, enabling you to investigate threats that move laterally across your cloud ecosystem.
"We had no insight into who was sharing what on Google. Varonis classified our data and gave us visibility we didn’t have before."
Miachael Trofi
CISO, Trofi Security
Read case studyVaronis solves common SaaS app data security challenges
Misplaced regulated data
- See total volume of sensitive and exposed data broken down by financial, federal, PII, and more
- Out-of-the-box and custom policies help you spot and fix risky configurations
- Remediate misconfigurations with a single click
Exposed secrets, tokens, and keys
- Surface insecure or exposed sensitive data and secrets (e.g., API keys, database credentials, encryption certificates, etc.)
- Gain real-time visibility with dashboards tracking sensitive data by type
- Prioritize risk by seeing where sensitive data is concentrated and where it’s at risk
Shadow identities and privilege sprawl
- Uncover shadow identities from personal accounts to application tokens
- Track enrollment of new admins, admin account changes, and segregation of duty violations
- Offboard stale admins, privileged users, and external contractors
One platform for multi-cloud, SaaS, and on-premises data.
Varonis protects enterprise data where it lives — in the largest and most important data stores and applications across the cloud and behind your firewall.
SaaS security resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital