Varonis for Network
Stop network intrusion and data exfiltration. Monitor VPN, DNS, firewall, and web activity to trace threats from the perimeter back to your data.
- Real-time
- Agentless
- Automated


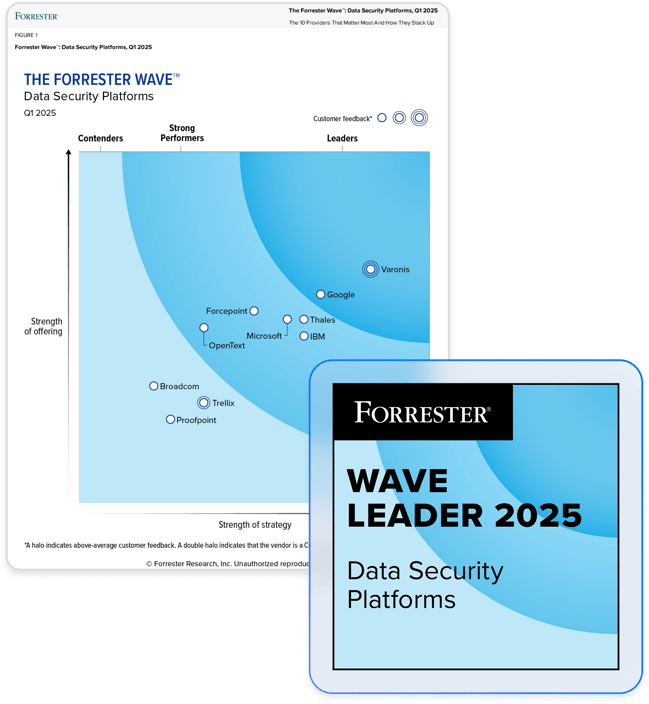
Partner with the leader in data security.
Stop threats before your data is stolen.
Detect threats at the perimeter.
Varonis monitors activity using AI-powered behavioral threat detection to identify abnormal activity at the network perimeter, such as traffic to malicious sites, abnormal VPN access, or DNS tunneling.
Trace incidents from the perimeter back to your data.
Varonis analyzes VPN, DNS, firewall, and web activity in the context of data, email, and the identity fabric to provide a comprehensive audit trail of activity that traces threats from the perimeter back to your data. With this expanded field of view, you can easily answer the crucial question, “Is our data safe?”
Extend your security team with MDDR.
Our global team of cybersecurity experts watches your data, user activity, and network 24x7x365 to detect threats, saving your team time and strengthening your data security — all without needing additional resources.

Automate threat response.
With instant and automated responses, Varonis stops attacks and limits the potential damage. Connect Varonis to your SOAR tools for automated, efficient incident response and recovery.
"Varonis was the only solution that was able to detect DNS tunneling threats. No other product was able to detect it. Some of them could collect DNS events, but even they couldn’t tell me at a glance what was going on like Varonis could."
Tony Hamil
Cyber Security Engineer, Top Real Estate Company
Read case studyVaronis solves common network security challenges
Data exfiltration
- Detect abnormal file uploads, downloads, and link sharing with built-in AI-powered threat models
- Identify C2 traffic in DNS, web proxy, and VPN traffic
- Trigger automated threat responses and send alerts to your SIEM/SOC/SOAR
Noisy, out-of-order, and disparate logs
- Monitor DNS, web proxy, and VPN activity and gain clean, normalized, and chronological event logs
- Correlate network activity with data, email, and identity activity to provide a complete picture of events
- Enrich logs with valuable context like URL reputation, account type, and data sensitivity
Ransomware, insider threats, and APTs
- Detect ransomware, insider threats, and APTs with expert-built behavioral threat models before they steal your data
- Set up alerts to be notified of abnormal access, encryption, lateral movement, and privilege escalation
- No custom rule-writing or static detections required
One platform for multi-cloud, SaaS, and on-premises data.
Varonis protects enterprise data where it lives — in the largest and most important data stores and applications across the cloud and behind your firewall.
Network security resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital