Data Lifecycle Automation
Automatically enforce data governance, lifecycle, and compliance policies without writing any code.
- Automated
- Secure
- Scalable






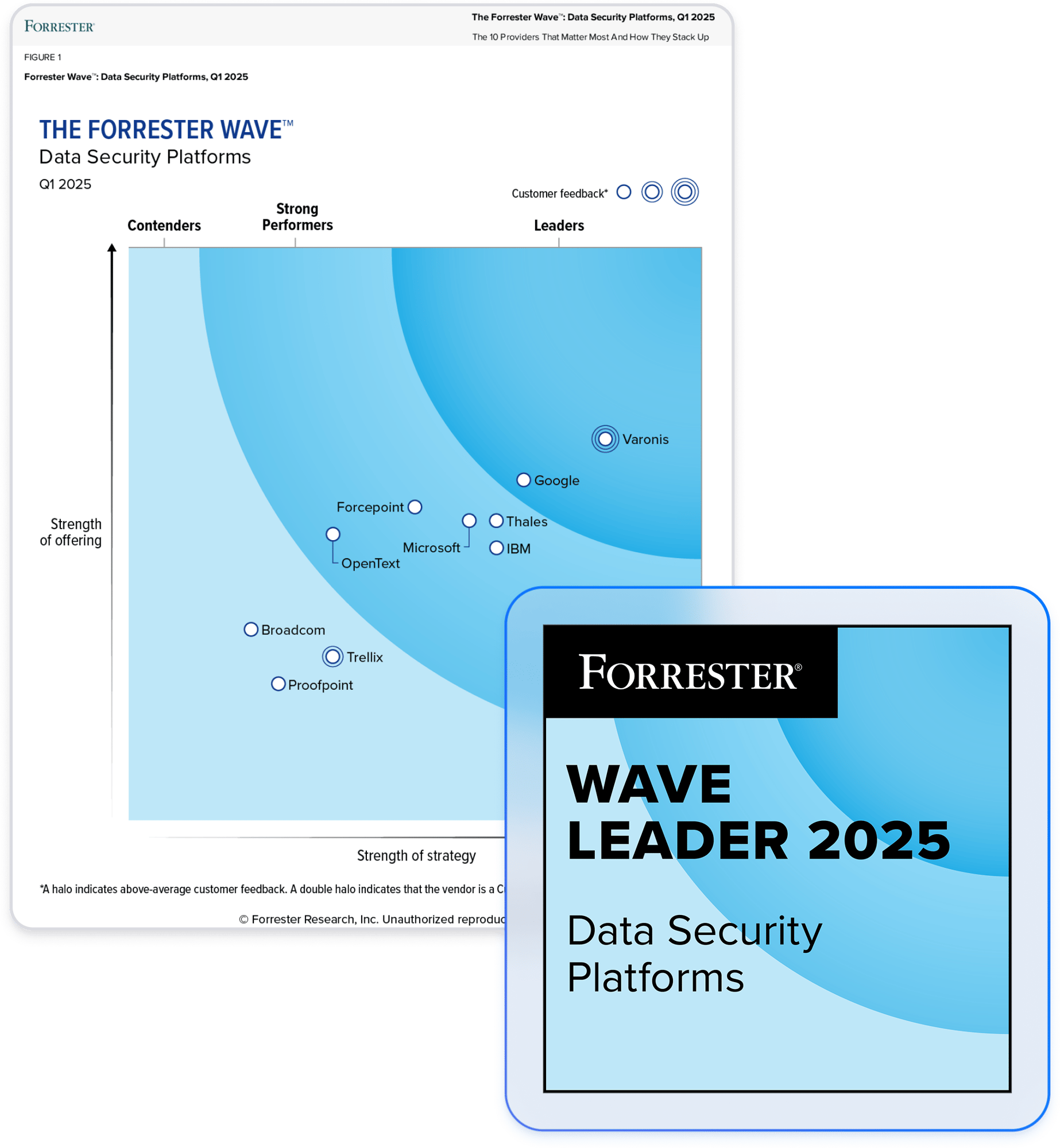
Partner with the leader in data security.
Automate your data governance and compliance efforts.
Automate data governance
- Enforce lifecycle policies
- Migrate data at scale
- Reduce storage costs
Streamline compliance
- Detect compliance violations
- Enforce retention and residency
- Comply with privacy laws
Reduce the blast radius
- Quarantine out-of-location data
- Eliminate sensitive data exposure
- Prevent risky AI access
“Varonis really saved us time with moving data around. If you’re trying to do things like file server migrations manually, it takes a lot of time. With Varonis, you click a few buttons, and then off your data goes. This was huge, especially with everyone moving data to the cloud.”
Shane Barry
IT Security Manager, Pizza Express, Retail
Read case studyAutomated policy enforcement
Automatically enforce lifecycle, retention, and residency requirements for different departments, servers, data types, and sensitivity levels. Create and enforce custom data governance and compliance policies without writing code.
Blast radius reduction
Varonis continuously monitors your data and enforces quarantine rules when it detects a policy violation. Automatically relocate data to a pre-determined secure location to reduce data risk and minimize the impact of a breach.
Domain consolidation and cloud migrations
Consolidate domains and handle large-scale cloud data migrations efficiently, ensuring data security and maintaining least privilege access. Take full control of naming conventions, permission structures, and collision behavior to ensure consistency as data moves.
Storage optimization
By continuously monitoring data activity, Varonis identifies stale and obsolete files and automatically transfers them to a designated location for archival or deletion – optimizing storage and reducing costs.
Our customers have spoken
One platform for multi-cloud, SaaS, and on-premises data.
Varonis protects enterprise data where it lives — in the largest and most important data stores and applications across the cloud and behind your firewall.
Additional governance and compliance resources
Go beyond data governance.
Varonis tackles hundreds of use cases, making it the ultimate platform to prevent data breaches and ensure compliance.
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital








