The Unified Data Security Platform
Secure your most valuable and vulnerable asset with the industry’s most complete data security platform. Reduce your blast radius and stop data breaches.
- Cloud-native
- Accurate
- Automated






Partner with the leader in data security.
Meaningful security outcomes without the manual effort.
Real-time visibility
- Discover and classify sensitive data
- Map and visualize your blast radius
- Monitor and query all data activity
Automated prevention
- Remove excessive permissions
- Fix risky misconfigurations
- Apply labels and enforce DLP policies
Proactive detection
- Alert on abnormal behavior
- Automate threat response actions
- 24x7x365 incident response support
We are way more prepared... not only from the automation, but the incident response that comes with that. Our security risk is 10X lower.
The Unified Data Security Platform
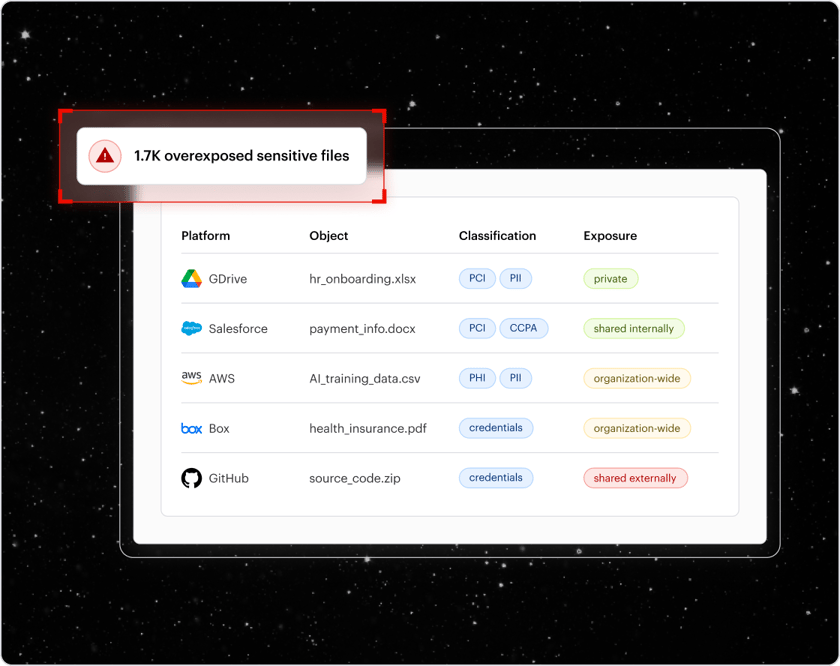
Accurate data discovery and classification
Continuously scan your sensitive data stored across your entire environment, including cloud, SaaS, and data centers. The combination of sophisticated rule-based and AI classification achieves 99% accuracy at scale and provides deep risk and exposure analysis.
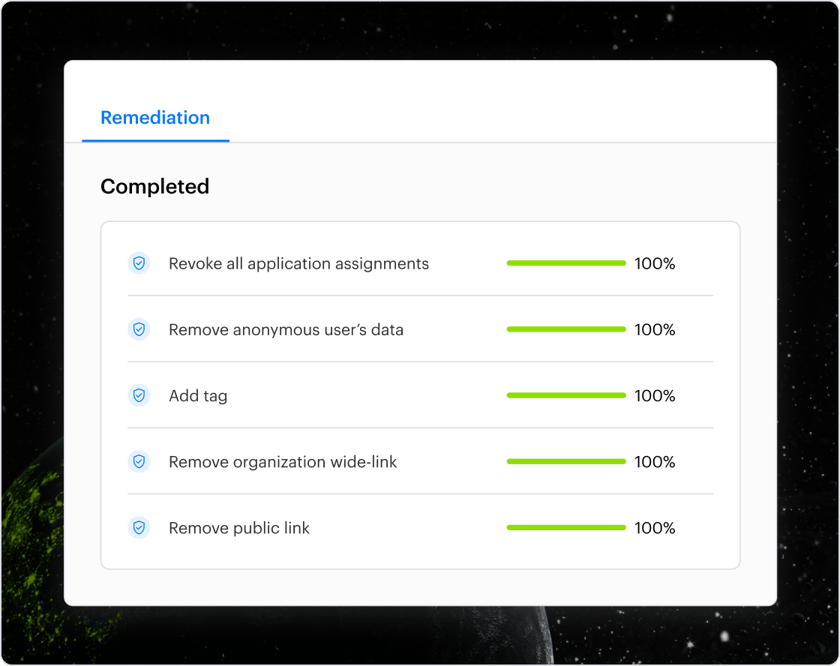
Automated remediation
Automatically remediate risky permissions, misconfigurations, ghost users, sharing links, and more. Varonis comes with ready-made remediation policies that can be customized for your organization.
Data-centric threat detection
Hundreds of expert-built threat detection policies automatically detect anomalies, alerting you to unusual file access activity, email send/receive actions, permissions changes, geo-hopping, and much more.
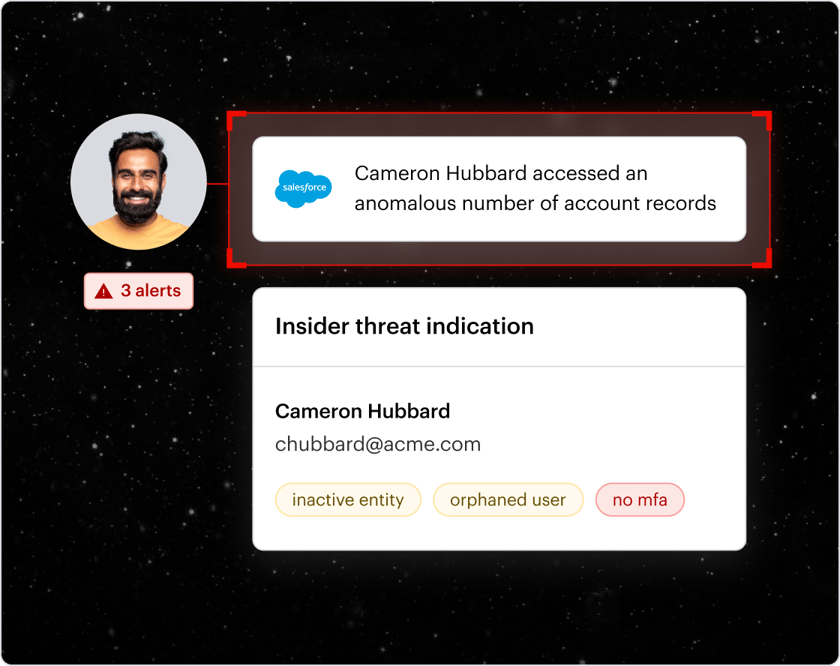
Enterprise ready
Varonis meets the needs of enterprise customers with world-class services, support for frameworks like RBAC, multi-tenancy, and industry standards, like FedRAMP, ISO/IEC, SOC, and HIPAA.
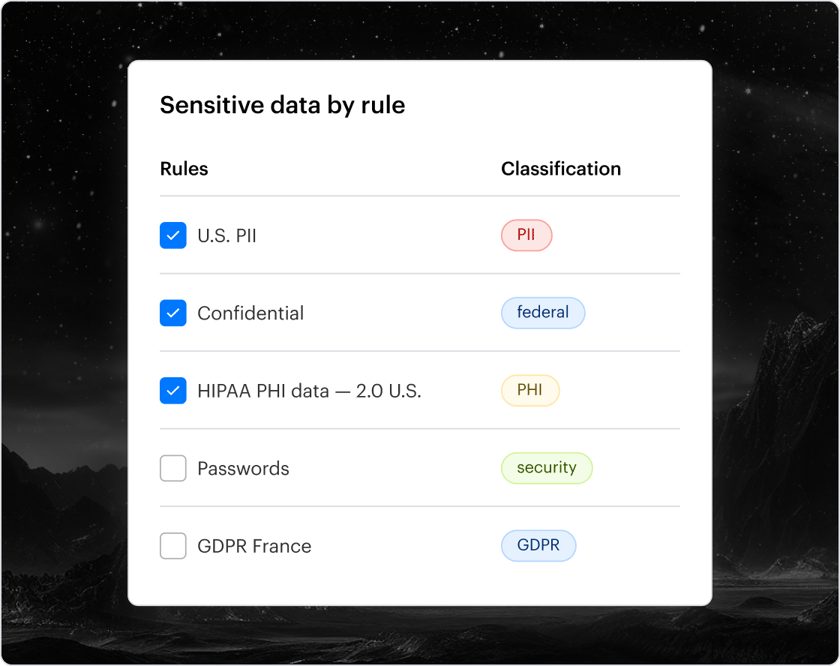
Powerful forensics layer
A powerful forensics layer aids investigations and compliance. It normalizes and enriches logs from your systems to create a searchable audit trail for answering data security questions.
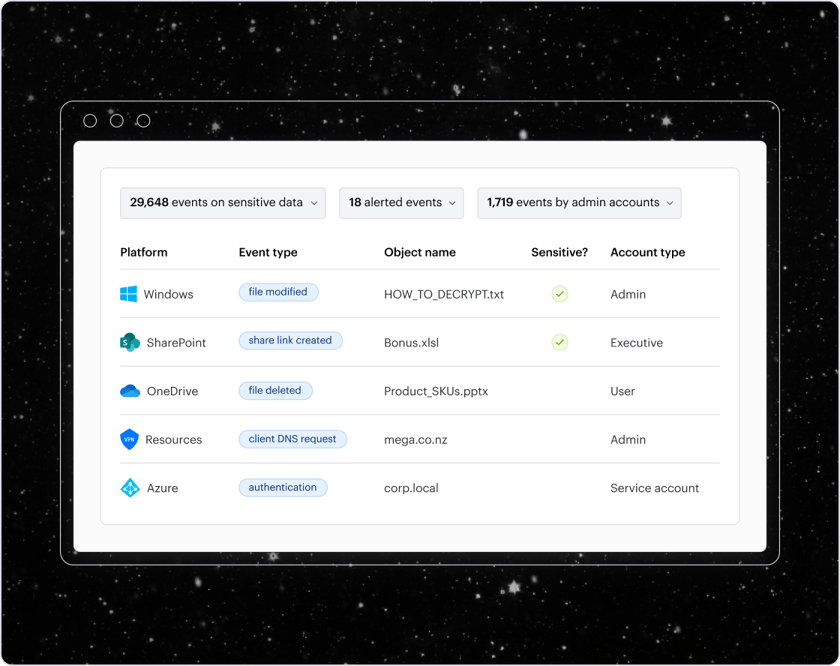
Broad and deep coverage
Varonis covers structured, unstructured, and semi-structured data across domains. Map and monitor attack paths that provide access to data, including directory services, network traffic, VPNs, DNS, and firewalls, and API/OAuth connections.

We watch your data, so you don’t have to.




Featured Resources
SECURITY STACK NEWSLETTER
Get the latest threat research and attack sims sent right to your inbox.
SECURITY STACK NEWSLETTER
Get the latest threat research and attack sims sent right to your inbox.
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital