Varonis for Salesforce
Eliminate risky misconfigurations, find and remediate exposed sensitive data, and detect anomalous behavior with the most complete Salesforce security product on the planet.
- Agentless
- SHIELD
- AppExchange






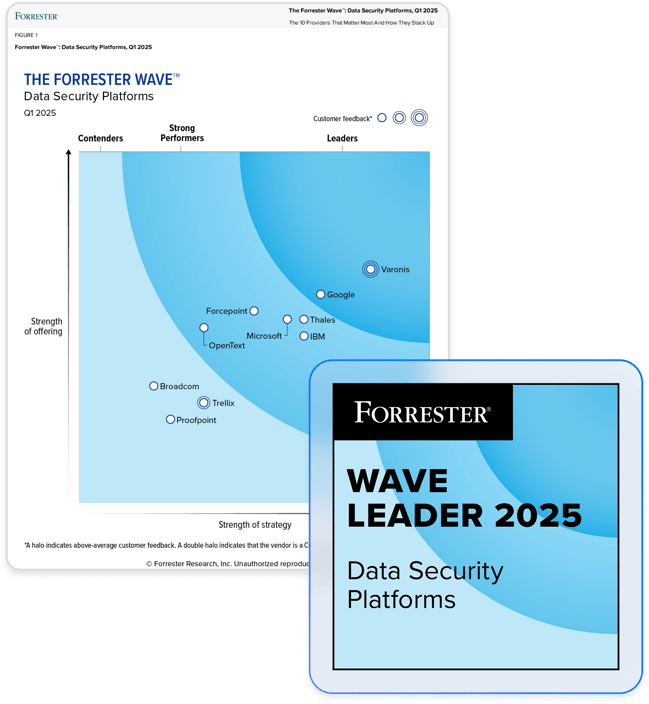
Partner with the leader in data security.
Meet your Salesforce safety net.
Identify at-risk sensitive data in hard-to-find places.
Varonis scans every file and attachment across your Salesforce instances, flags the sensitive ones, and shows you where you’re at risk. Filter your classification results to Salesforce-only, or view sensitive data across all your SaaS apps, IaaS, and file stores.
Simplify complex permissions.
Varonis simplifies Salesforce's complex permissions and automatically surfaces users assigned high-risk entitlements with a real-time, interactive view across users, profiles, and permission sets.
Proactively reduce sensitive data exposure.
Varonis automatically fixes misconfigurations, revokes high-risk permissions, remediates public exposure, and removes risky third-party app connections to reduce your blast radius and secure sensitive data.
Stop attackers and rogue insiders.
Varonis detects suspicious activity – such as accessing an unusual number of records, escalating privileges, or exporting reports – that could put your Salesforce data at risk.
Integrate with Salesforce Shield.
Varonis ingests Shield events and enriches them with unique metadata to supercharge threat detection and investigation. Ready-made alerts make Salesforce Shield events actionable – no Apex coding required.
Varonis for Salesforce Demo
See how you can keep sensitive data in Salesforce secure with Varonis.
"It was a gaping black hole. I’d heard horror stories about Salesforce permissions and how literally hundreds can be applied in a manner of different ways."
Tony Hamil
Senior Cybersecurity Engineer, Top Real Estate Organization
Read case studyVaronis solves common Salesforce data security challenges.
Users can view, modify, and export all data
- Varonis uncovers standard users that have admin-like privileges
- Easily find and eliminate profiles and permission sets that grant unnecessarily broad access
- Surface critical misconfigurations like users with API enabled and admins without MFA
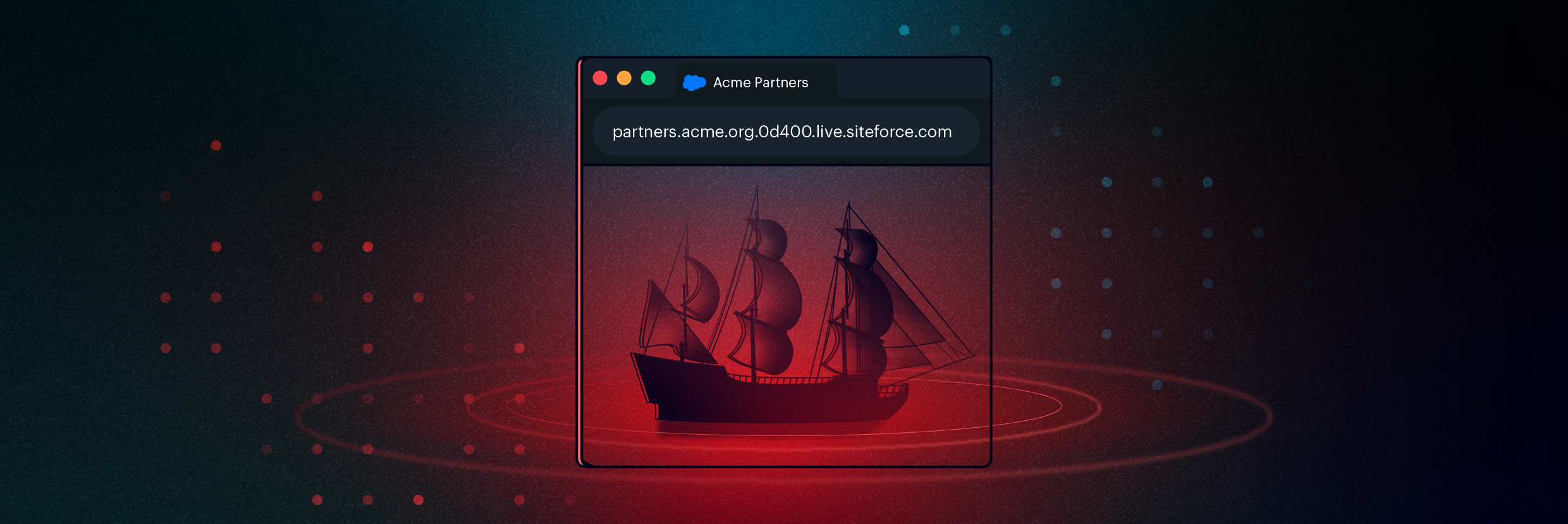
Risky third-party apps with broad access
- Varonis continuously scans and identifies third-party apps installed on Salesforce
- See which apps can access sensitive data
- Identify and revoke stale or excessive app assignments
Sensitive files shared via public links
- Varonis shows you all public links, whether they are sensitive, who created them, when, and more
- Create a policy to automatically revoke sensitive links, stale links, or all public links
- Remediate profiles and permission sets that allow public link creation
One platform for multi-cloud, SaaS, and on-premises data.
Varonis protects enterprise data where it lives — in the largest and most important data stores and applications across the cloud and behind your firewall.
Salesforce security resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital