Protect your critical Microsoft 365 data with least privilege automation, data-centric UEBA, and world-class data classification.
- Agentless
- Automated
- Azure Marketplace

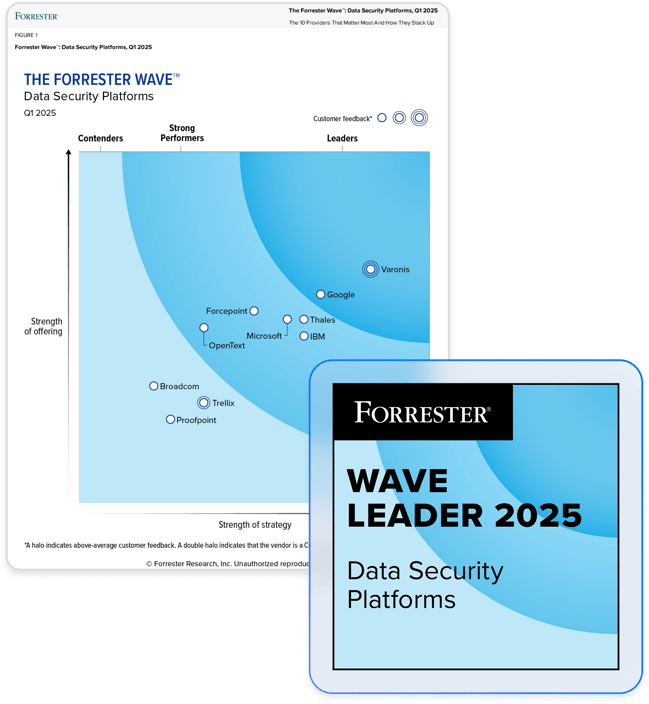
Partner with the leader in data security.
Securely deploy Microsoft 365 Copilot.
Find and classify sensitive data across Microsoft 365.
Automatically and accurately classify sensitive data shared across your environment. Varonis looks inside every file and folder to find sensitive information, and show you exactly where it lives and who has access to it — all in an easy-to-read file tree.
Apply accurate and actionable MPIP labels.
Varonis fully integrates with Microsoft Purview to enhance Microsoft's native classification in E3 and E5. Create granular policies to fit your needs, automatically fix manual gaps, and re-label files as your data changes — making downstream DLP controls more effective.
Enforce least privilege across Microsoft 365.
Effortlessly eliminate data exposure from shared links and excessive permissions. Varonis makes intelligent decisions about who needs access to data and who doesn’t and then automatically remediates risky permissions at scale.
Uncover data exposure with deep permissions analysis.
View your Microsoft environment's permission structures in a single interface and ensure only the right people have access to important files, folders, and mailboxes. We calculate effective permissions so you can prioritize remediation based on risk.
Stop attackers and rogue insiders.
Streamline cross-cloud investigations.
Varonis monitors data access activity in Microsoft 365 and corporate file shares and logs a complete audit trail, quickly investigating threats that move laterally across your cloud and on-prem environments.
Protect critical identities in Entra ID.
"Varonis' integration gives customers the added security and compliance controls necessary to quickly and confidently adopt Microsoft Copilot for Microsoft 365.”
Anat Gil, Partners Lead
Microsoft South-East Europe
Learn moreVaronis solves common Microsoft 365 and Entra ID data security challenges.
Sensitive data exposure from risky permissions
- Identify shared links and excessive permissions.
- Automatically correct org-wide permissions and delete stale users.
- Limit access change permissions to a small group of admins.
Microsoft Teams sprawl
- Use dynamic dashboards to clearly visualize the impact of Teams collaboration.
- Pinpoint and remediate stale, risky, or excessive access.
- Monitor activity to detect suspicious sharing behavior or unusual permission changes.
Exposed mailboxes and calendars in Exchange
- Identify mailboxes exposed to guest and external users, non-mailbox owners, or delegates.
- Right-size access to sensitive mailboxes and calendars.
- Detect and flag data privacy violations or improper data handling.
Protect your data, wherever it lives.
One platform for complete data security across multi-cloud, SaaS, hybrid, and AI.
Microsoft 365 security resources
Ready to see the #1 Data Security Platform in action?
Ready to see the #1 Data Security Platform in action?
“I was amazed by how quickly Varonis was able to classify data and uncover potential data exposures during the free assessment. It was truly eye-opening.”
Michael Smith, CISO, HKS
"What I like about Varonis is that they come from a data-centric place. Other products protect the infrastructure, but they do nothing to protect your most precious commodity — your data."
Deborah Haworth, Director of Information Security, Penguin Random House
“Varonis’ support is unprecedented, and their team continues to evolve and improve their products to align with the rapid pace of industry evolution.”
Al Faella, CTO, Prospect Capital