Moving your company’s data to cloud-based storage is a big job, and we want to make sure you understand what it takes to ensure that your Office 365 data is managed, protected, and accessible.
- Before Migrating to Office 365
- Common Migration Paths and Methods
- Office 365 Migration Steps
- How Varonis Helps Protect Data in Office 365
- Migrating Emails
- Office 365 Migration Tools
Before Migrating to Office 365
Before you migrate to Office 365, you need to know what data you need to keep, what data you can get rid of, and how you are going to establish a permissions structure in Office 365.
Is your Office 365 and Teams data as secure as it could be? Find out with our Free Video Course.
Understand Your Data
Do you understand your data: the security, organization, and access before you make the move?
Here are some key questions you should consider when thinking about your Office 365 strategy:
- Does it make sense to move all of your files, or leave some behind?
- Once you create a policy that describes what should be migrated to Office 365, how will you find the files and folders that meet the criteria?
- What administrative tasks that currently happen onsite will be affected by moving to Office 365? Some examples:
- Permissions management
- Backups
- Disaster recovery
- Data loss prevention
- Access auditing
- Will you have the appropriate level of controls on Office 365 to manage and protect your data?
- Will you be subject to any additional compliance requirements?
Meanwhile, if you need to perform complex searches for eDiscovery or compliance purposes, you’ll need a third party solution.
Ask Questions Before Migrating Your Data
Migration can be difficult, particularly for organizations that maintain a hybrid deployment of on premise and cloud-based users. Hybrid deployments allow you to move some data to the cloud, while being able to support internal systems, ensure compliant environments, and more.
- Will users in both systems be able to share a common directory during transition/migration?
On-premise environments might require third party tools to manage Office 365: hybrid deployments require prerequisites (for example, with Exchange 2007/2010 environments there must be at least one Exchange 2013 Client Access and Mailbox server in place to run the Hybrid configuration wizard.)
- How do users access data? What will change? Do they need VPN access to get to Office 365 data?
- Will you need additional cloud apps to manage the migration and maintenance?
- Have you recently done an assessment of permissions audits, access activity, and content classification?
- How will you ensure that only the right people will have access to data in Office 365?
Map Out Your Infrastructure
Office 365 requires Azure Active Directory, AD Synchronization appliance (DirSync) and Active Directory Federation Services (AD FS). If you have more than one AD forest, or want to sync with an additional LDAP directory, you’ll need a custom deployment of Forefront Identity manager 2010 R2. Depending on the details of your existing infrastructure, you’ll want to plan out what 3rd party solutions you’ll want to integrate as well.
Know the Physical Location of Your Data
How do you make sure your sensitive data and confidential information is secure? Office 365 does not provide advanced threat protection for targeted attacks, nor native surveillance features for monitoring communications or access activity (important for compliance.) Patch management, software upgrades, backup and recovery of data are controlled solely by Microsoft: you’ll likely need a 3rd party backup solution.
- Do you have a disaster recovery plan? An incident response plan?
- Do you understand the risk associating with storing restricted and regulated data?
- Is Office 365 SRA complaint within your region?
- Will you need to rebuild the permissions structure?
Common Migration Paths and Methods
In general, there are three approaches to migrating an enterprise to Microsoft 365.
Cutover
The cutover method is when you want the transition done fast. One day you turn on Office 365 and turn off the previous systems. The cutover method is a disruptive option and can incur a heavy load on IT resources while users figure the new system out.
- Pros:
-
- Promotes immediate adoption of the new platform
-
- Migrates all data at once
-
- Microsoft provides many tools to facilitate a total on-premise to cloud migration
- Cons:
-
- Requires the most preparation with the highest possibility of business continuity issues
-
- Most useful for smaller organizations
Staged
Staged migrations are total migrations to Office 365, but completed in stages. Most are in two parts, but there could be more.
- Pros:
-
- Better for larger orgs than a cutover
-
- It’s possible to migrate smaller chunks of data, like everything touched in the last month, first
-
- Microsoft provides many tools to facilitate a total on-premise to cloud migration
- Cons:
-
- It can become hard to manage an organization that lives in two different places until the migration is complete
Hybrid
The hybrid migration model is the one most common in the enterprise. This model adds the Office 365 functionality on top of the existing infrastructure to create a mixture of cloud and on-premise, hence “hybrid.”
- Pros:
-
- Builds on current infrastructure to keep the business impact minimal during migration
-
- Microsoft has developed many tools for Office 365 to support a hybrid infrastructure
- Cons:
-
- Can be more difficult to secure than fully on-premise or cloud system
-
- Hybrid infrastructures require more resources to manage and support
Office 365 Migration Steps
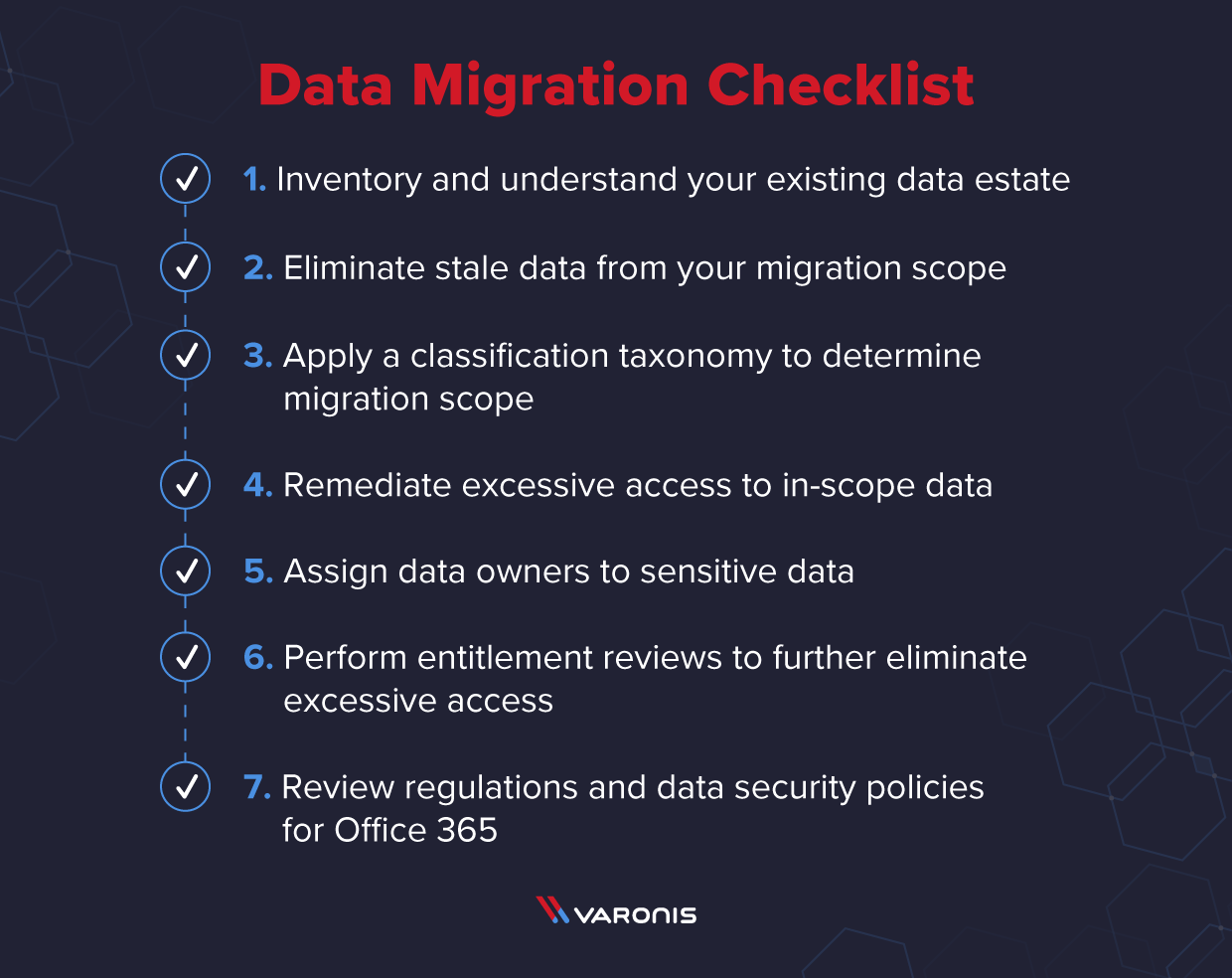
Follow this process to best set yourself up for a successful Office 365 rollout.
1. Inventory and understand your existing data estate
The first step is to map your current data stores – you have to know what you need to migrate.
Building a complete and accurate inventory, establishing a classification taxonomy, and prioritizing data sets are essential steps for a successful migration. Varonis gives you the visibility required to take these steps without heaps of manual work and without relying solely on surveying end-users.
2. Eliminate stale data from your migration scope
Because Varonis is actively monitoring all user activity on data—every file open, move, rename, modify, delete—we can confidently identify data that is stale and can be excluded from your migration scope, archived, or deleted.
3. Apply a classification taxonomy to determine migration scope
Determine what sensitive data — if any — you will migrate and create controls around that data to prevent data breaches.
Varonis classifies data for PCI, GDPR, HIPAA, CCPA, and many more regulations out-of-the-box, at a petabyte scale.
4. Remediate excessive access to in-scope data
One of the biggest challenges in all of data security, regardless of where data lives, is to visualize and remediate overexposed sensitive data. Our global risk report shows that, on average, 22% of all company data is exposed to everyone in the company.
We suggest customers remediate excessive access prior to their migration. With Automation Engine, remediation of hundreds of terabytes of data can be complete in days, not years.
Varonis automatically remediates Global Access Groups (GAGs) and Broken Access Control Lists (BACLs) to alleviate two enormous sources of risk quickly and easily.
Global Access Groups are the default groups in Windows systems like Everyone or Authenticated Users. Varonis can detect global access and automatically revoke that access without interrupting users who actively use the data.
Broken ACLs are permissions issues where the permissions on a child folder don’t match the parent and other similar issues. Broken ACLs occur for many reasons, but what you need to know about them for your cloud migration is that just because you move your data to the cloud, it doesn’t mean your data on-premise is safe.
Varonis provides recommendations of users that have permissions to data based on cluster analysis and machine learning, so you can safely revoke permissions without affecting productivity. Use the Review tab in DatAdvantage and to safely revoke access to over-permissive folders before you move them to the cloud.
5. Assign data owners to sensitive data
Varonis’ algorithms are very good at determining who should and shouldn’t have access to data, but it’s a best practice to assign data owners to critical data sets. Data owners can review who has access and make decisions based on business context.
Varonis has a tried-and-true process, using both quantitative and qualitative methods, to a.) determine which data should have an owner and b.) who the owner should be.
6. Perform entitlement reviews to further eliminate excessive access
Once you have data owners established, force an entitlement review pre-migration to ensure that they weed out excess access that your automated remediation didn’t tackle.
Varonis DataPrivilege makes it easy for data owners to review and revoke access via entitlement reviews, inspect usage of their data via a self-service portal, and approve/deny incoming access control requests.
You can schedule entitlement views to occur on a monthly or quarterly basis, or kick one off manually before your migration to the cloud. Each data set or department can have a custom review schedule and, when completing a review, the data owner is notified if the folders or sites they are reviewing contain any sensitive or regulated information.
7. Review regulations and data security policies for Office 365
Your organization’s security policies and the regulations your data is subject to will often dictate which features in Office 365 should be enabled or disabled.
One of the most important decisions to make prior to migrating is how data should be shared—both internally and externally.
- What will your external sharing policy be?
- How will you ensure that policy isn’t violated?
- Is it different for sensitive vs. non-sensitive?
- Is it different for OneDrive vs. Teams vs. SharePoint?
This topic is covered extensively in our 1-Hour Office 365 Sharing Security Audit video course, led by renowned Microsoft MVP Vlad Catrinescu.
When you complete this course, you’ll be confident that despite all the fine-grained controls Microsoft gives you, your Office 365 sharing settings match your organization’s desired sharing policy.
How Varonis Helps Protect Data in Office 365
Varonis provides Office 365 users with data monitoring and advanced threat detection and analysis capabilities to protect your data and investment in the cloud.
- View reports of all kinds of sharing links and automate remediation if necessary
- Continuously monitor permissions and access to SharePoint and OneDrive
- Detect cybersecurity threats by monitoring data and email activity, pulling in perimeter telemetry and individual user baselines, and comparing current data to threat models built by security experts to detect malware, ransomware, APT, insider threats, and more
- Level-up your Incident Response team with Varonis alerts and context to begin an investigation of potential attacks with actionable data security intelligence
Migrating Emails
Migrating emails is radically different from migrating unstructured data. Emails are structured because they are managed in a system like Exchange, or GSuite, or whichever mail system you use.
To migrate emails from one system to Office 365, you will need a way to export the emails from the old system and then import them to Office 365.
Microsoft does have a list of best practices for reference. And they have tools and instructions to migrate from Exchange on-prem and IMAP email systems for reference.
Office 365 Migration Tools
The market is filled with tools and services offerings for Office 365 migration tools. Refer to Microsoft’s Office 365 migration tools page for approved resources.
Varonis can transfer files and make your data safer when you move to the cloud. Usually, the opposite occurs.
The key takeaway is to plan your Office 365 migration thoroughly before you start. Manage permissions both on your current data and onto any data you move to the cloud. Search for sensitive data, and then use advanced analytics to detect threats against your cloud-facing data.
And finally, check out our webinar on security in Teams to learn why you need Varonis to manage your Office 365 environment.
What you should do now
Below are three ways we can help you begin your journey to reducing data risk at your company:
- Schedule a demo session with us, where we can show you around, answer your questions, and help you see if Varonis is right for you.
- Download our free report and learn the risks associated with SaaS data exposure.
- Share this blog post with someone you know who'd enjoy reading it. Share it with them via email, LinkedIn, Reddit, or Facebook.