This article is part of the series "Data Security Compliance and DatAdvantage". Check out the rest:
I can’t really overstate the importance of risk assessments in data security standards. It’s really at the core of everything you subsequently do in a security program. In this post we’ll finish discussing how DatAdvantage helps support many of the risk assessment controls that are in just about every security law, regulation, or industry security standard.
Last time, we saw that risk assessments were part of NIST’s Identify category. In short: you’re identifying the risks and vulnerabilities in your IT system. Of course, at Varonis we’re specifically focused on sensitive plain-text data scattered around an organization’s file system.
Get the Free Essential Guide to US Data Protection Compliance and Regulations
Identify Sensitive Files in Your File System
As we all know from major breaches over the last few years, poorly protected folders is where the action is for hackers: they’ve been focusing their efforts there as well.
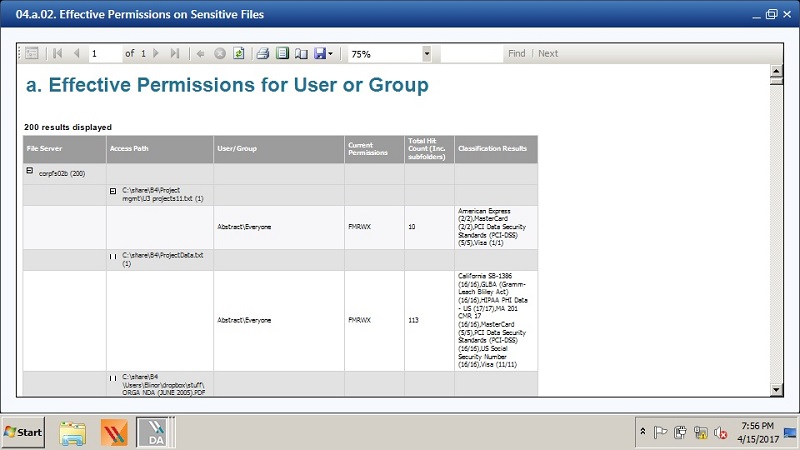
The DatAdvantage 4a report I mentioned in the last last post is used for finding sensitive data in folders with global permissions. Varonis uses various built-in filters or rules to decide what’s considered sensitive.
I counted about 40 or so such rules, covering credit card, social security, and various personal identifiers that are required to be protected by HIPAA and other laws. And with our new GDPR Patterns there are now filters — over 250! —covering phone, license, and national IDs for EU countries
Identify Risky and Unnecessary Users Accessing Folders
We now have a folder that is a potential source of data security risk. What else do we want to identify?
Users that have accessed this folder is a good starting point.
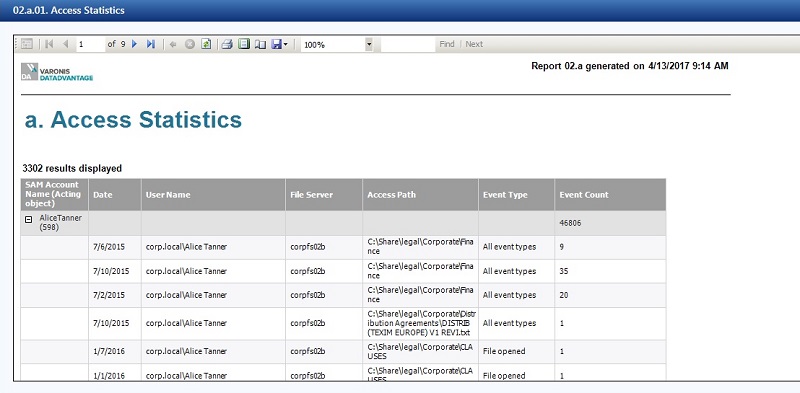
There are a few ways to do this with DatAdvantage, but let’s just work with the raw access audit log of every file event on a server, which is available in the 2a report. By adding a directory path filter, I was able to narrow down the results to the folder I was interested in.
So now we at least know who’s really using this specific folder (and sub-folders). Often times this is a far smaller pool of users then has been enabled through the group permissions on the folders. In any case, this should be the basis of a risk assessment discussion to craft more tightly focused groups for this folder and setting an owner who can then manage the content.
In the Review Area of DatAdvantage, there’s more graphical support for finding users accessing folders, the percentage of the Active Directory group who are actually using the folder, as well as recommendations for groups that should be accessing the folder. We’ll explore this section of DataAdvantage further below.
For now, let’s just stick to the DatAdvantage reports since there’s so much risk assessment power bundled into them.
Another similar discussion can be based on using the 12l report to analyze folders containing sensitive data but have global access – i.e., includes the Everyone group.
There are two ways to think about this very obvious risk. You can remove the Everyone access on the folder. This can and likely will cause headaches for users. DatAdvantage conveniently has a sandbox feature that allows you to test this.
On the other hand, there may be good reasons the folder has global access, and perhaps there are other controls in place that would (in theory) help reduce the risk of unauthorized access. This is a risk discussion you’d need to have.
Another way to handle this is to see who’s copying files into the folder — maybe it’s just a small group of users — and then establish policies and educate these users about dealing with sensitive data.
You could then go back to the 1A report, and set up filters to search for only file creation events in these folders, and collect the user names (below).
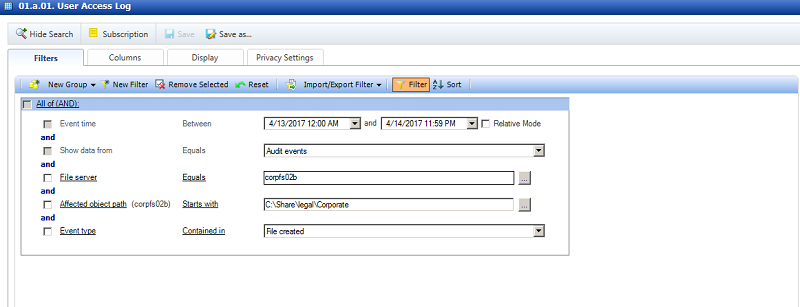
After emailing this group of users with followup advice and information on copying, say, spreadsheets with credit card numbers, you can run the 12l reports the next month to see if any new sensitive data has made its way into the folder.
The larger point is that the DatAdvantage reports help identify the risks and the relevant users involved so that you can come up with appropriate security policies — for example, least-privileged access, or perhaps looser controls but with better monitoring or stricter policies on granting access in the first place. As we’ll see later on in this series, Varonis DatAlert and DataPrivilege can help enforce these policies.
In the previous post, I listed the relevant controls that DA addresses for the core identification part of risk assessment. Here’s a list of risk assessment and policy making controls in various laws and standards where DatAdvantage can help:
- NIST 800-53: RA-2, RA-3, RA-6
- NIST 800-171: 3.11.1
- HIPAA: 164.308(a)(1)(i), 164.308(a)(1)(ii)
- Gramm-Leach-Bliley: 314.4(b),(c)
- PCI DSS 3.x: 12.1,12.2
- ISO 27001: A.12.6.1, A.18.2.3
- CIS Critical Security Controls: 4.1, 4.2
- New York State DFS Cybersecurity Regulations: 500.03, 500.06
Thou Shalt Protect Data
A full risk assessment program would also include identifying external threats—new malware, new hacking techniques. With this new real-world threat intelligence, you and your IT colleagues should go back re-adjust the risk levels you’ve assigned initially and then re-strategize.
It’s an endless game of cyber cat-and-mouse, and a topic for another post.
Let’s move to the next broad functional category, Protect. One of the critical controls in this area is limiting access to only authorized users. This is easier said done, but we’ve already laid the groundwork above.
The guiding principles are typically least-privileged-access and role-based access controls. In short: give appropriate users just the access they need to their jobs or carry out roles.
Since we’re now at a point where we are about to take a real action, we’ll need to shift from the DatAdvantage Reports section to the Review area of DatAdvantage.
The Review Area tells me who’s been accessing the legal\Corporate folder, which turns out to be a far smaller set than has been given permission through their group access rights.
To implement least-privilege access, you’ll want to create a new AD group for just those who really, truly need access to the legal\Corporate folder. And then, of course, remove the existing groups that have been given access to the folder.
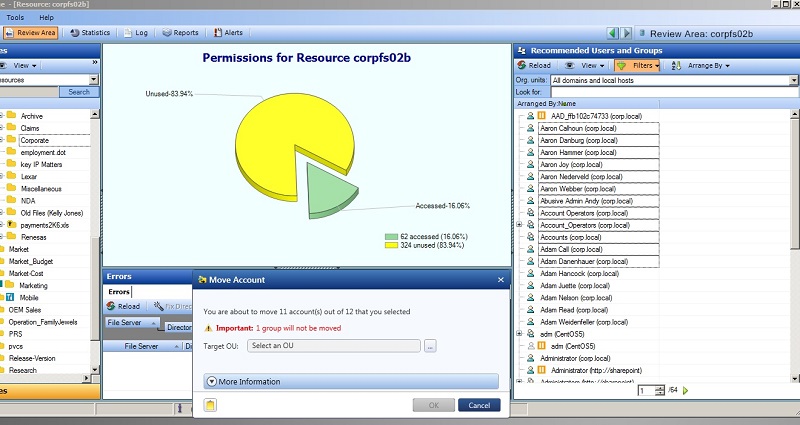
Yeah, this assumes you’ve done some additional legwork during the risk assessment phase — spoken to the users who accessed Corporate\legal folder, identified the true data owners, and understood what they’re using this folder for.
DatAdvantage can provide a lot of support in narrowing down who to talk to. So by the time you’re ready to use the Review Area to make the actual changes, you already should have a good handle on what you’re doing.
One other key control, which will discuss in more detail the next time, is managing file permission for the folders.
Essentially, that’s where you find and assign data owners, and then insure that there’s a process going forward to allow the owner to decide who gets access. We’ll show how Varonis has a key role to play here through both DatAdvatange and DataPrivilege.
I’ll leave you with this list of least permission and management controls that Varonis supports:
- NIST 800-53: AC-2, AC-3, AC-6
- NIST 800-171: 3.14,3.15
- PCI DSS 3.x: 7.1
- HIPAA: 164.312 a(1)
- ISO 27001: A.6.1.2, A.9.1.2, A.9.2.3
- CIS Critical Security Controls: 14.4
- New York State DFS Cybersecurity Regulations: 500.07
What you should do now
Below are three ways we can help you begin your journey to reducing data risk at your company:
- Schedule a demo session with us, where we can show you around, answer your questions, and help you see if Varonis is right for you.
- Download our free report and learn the risks associated with SaaS data exposure.
- Share this blog post with someone you know who'd enjoy reading it. Share it with them via email, LinkedIn, Reddit, or Facebook.